Post Syndicated from Shalabh Mohan original https://blog.cloudflare.com/how-sophisticated-scammers-and-phishers-are-preying-on-customers-of-silicon-valley-bank/


By now, the news about what happened at Silicon Valley Bank (SVB) leading up to its collapse and takeover by the US Federal Government is well known. The rapid speed with which the collapse took place was surprising to many and the impact on organizations, both large and small, is expected to last a while.
Unfortunately, where everyone sees a tragic situation, threat actors see opportunity. We have seen this time and again – in order to breach trust and trick unsuspecting victims, threat actors overwhelmingly use topical events as lures. These follow the news cycle or known high profile events (The Super Bowl, March Madness, Tax Day, Black Friday sales, COVID-19, and on and on), since there is a greater likelihood of users falling for messages referencing what’s top of mind at any given moment.
The SVB news cycle makes for a similarly compelling topical event that threat actors can take advantage of; and it’s crucial that organizations bolster their awareness campaigns and technical controls to help counter the eventual use of these tactics in upcoming attacks. It’s tragic that even as the FDIC is guaranteeing that SVB customers’ money is safe, bad actors are attempting to steal that very money!
Preemptive action
In anticipation of future phishing attacks taking advantage of the SVB brand, Cloudforce One (Cloudflare’s threat operations and research team) significantly increased our brand monitoring focused on SVB’s digital presence starting March 10, 2023 and launched several additional detection modules to spot SVB-themed phishing campaigns. All of our customers taking advantage of our various phishing protection services automatically get the benefit of these new models.
Here’s an actual example of a real campaign involving SVB that’s happening since the bank was taken over by the FDIC.
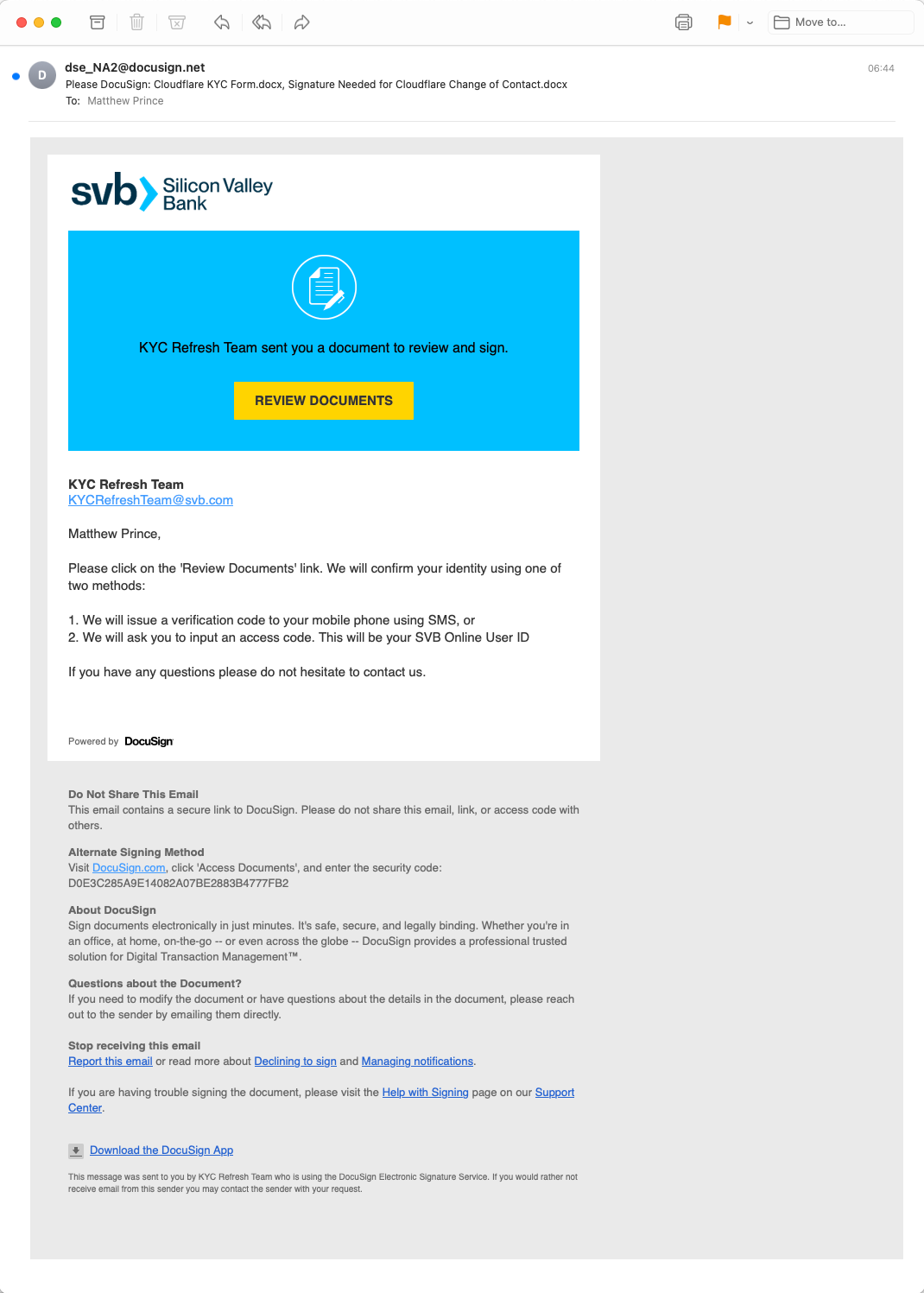
KYC phish – DocuSign-themed SVB campaign
A frequent tactic used by threat actors is to mimic ongoing KYC (Know Your Customer) efforts that banks routinely perform to validate details about their clients. This is intended to protect financial institutions against fraud, money laundering and financial crime, amongst other things.
On March 14, 2023, Cloudflare detected a large KYC phishing campaign leveraging the SVB brand in a DocuSign themed template. This campaign targeted Cloudflare and almost all industry verticals. Within the first few hours of the campaign, we detected 79 examples targeting different individuals in multiple organizations. Cloudflare is publishing one specific example of this campaign along with the tactics and observables seen to help customers be aware and vigilant of this activity.
Campaign Details
The phishing attack shown below targeted Matthew Prince, Founder & CEO of Cloudflare on March 14, 2023. It included HTML code that contains an initial link and a complex redirect chain that is four-deep. The chain begins when the user clicks the ‘Review Documents’ link. It takes the user to a trackable analytic link run by Sizmek by Amazon Advertising Server bs[.]serving-sys[.]com. The link then further redirects the user to a Google Firebase Application hosted on the domain na2signing[.]web[.]app. The na2signing[.]web[.]app HTML subsequently redirects the user to a WordPress site which is running yet another redirector at eaglelodgealaska[.]com. After this final redirect, the user is sent to an attacker-controlled docusigning[.]kirklandellis[.]net website.
Campaign Timeline
2023-03-14T12:05:28Z First Observed SVB DoucSign Campaign Launched
2023-03-14T15:25:26Z Last Observed SVB DoucSign Campaign LaunchedA look at the HTML file Google Firebase application (na2signing[.]web[.]app)
The included HTML file in the attack sends the user to a WordPress instance that has recursive redirection capability. As of this writing, we are not sure if this specific WordPress installation has been compromised or a plugin was installed to open this redirect location.
<html dir="ltr" class="" lang="en"><head>
<title>Sign in to your account</title>
<script type="text/javascript">
window.onload = function() {
function Redirect (url){
window.location.href = url;
}
var urlParams = new URLSearchParams(window.location.href);
var e = window.location.href;
Redirect("https://eaglelodgealaska[.]com/wp-header.php?url="+e);
}
</script>
Indicators of Compromise
na2signing[.]web[.]app Malicious Google Cloudbase Application.
eaglelodgealaska[.]com Possibly compromised WordPress website or an open redirect.
*[.]kirklandellis[.]net Attacker Controlled Application running on at least docusigning[.]kirklandellis[.]net.
Recommendations
-
Cloudflare Email Security customers can determine if they have received this campaign in their dashboard with the following search terms:
SH_6a73a08e46058f0ff78784f63927446d875e7e045ef46a3cb7fc00eb8840f6f0Customers can also track IOCs related to this campaign through our Threat Indicators API. Any updated IOCs will be continually pushed to the relevant API endpoints.
-
Ensure that you have appropriate DMARC policy enforcement for inbound messages. Cloudflare recommends [p = quarantine] for any DMARC failures on incoming messages at a minimum. SVB’s DMARC records [
v=DMARC1; p=reject; pct=100] explicitly state rejecting any messages that impersonate their brand and are not being sent from SVB’s list of designated and verified senders. Cloudflare Email Security customers will automatically get this enforcement based on SVB’s published DMARC records. For other domains, or to apply broader DMARC based policies on all inbound messages, Cloudflare recommends adhering to ‘Enhanced Sender Verification’ policies across all inbound emails within their Cloudflare Area 1 dashboard. -
Cloudflare Gateway customers are automatically protected against these malicious URLs and domains. Customers can check their logs for these specific IOCs to determine if their organization had any traffic to these sites.
-
Work with your phishing awareness and training providers to deploy SVB-themed phishing simulations for your end users, if they haven’t done so already.
-
Encourage your end users to be vigilant about any ACH (Automated Clearing House) or SWIFT (Society for Worldwide Interbank Financial Telecommunication) related messages. ACH & SWIFT are systems which financial institutions use for electronic funds transfers between entities. Given its large scale prevalence, ACH & SWIFT phish are frequent tactics leveraged by threat actors to redirect payments to themselves. While we haven’t seen any large scale ACH campaigns utilizing the SVB brand over the past few days, it doesn’t mean they are not being planned or are imminent. Here are a few example subject lines to be aware of, that we have seen in similar payment fraud campaigns:
“We’ve changed our bank details”
“Updated Bank Account Information”
“YOUR URGENT ACTION IS NEEDED –
Important – Bank account details change”
“Important – Bank account details change”
“Financial Institution Change Notice” -
Stay vigilant against look-alike or cousin domains that could pop up in your email and web traffic associated with SVB. Cloudflare customers have in-built new domain controls within their email & web traffic which would prevent anomalous activity coming from these new domains from getting through.
-
Ensure any public facing web applications are always patched to the latest versions and run a modern Web Application Firewall service in front of your applications. The campaign mentioned above took advantage of WordPress, which is frequently used by threat actors for their phishing sites. If you’re using the Cloudflare WAF, you can be automatically protected from third party CVEs before you even know about them. Having an effective WAF is critical to preventing threat actors from taking over your public Web presence and using it as part of a phishing campaign, SVB-themed or otherwise.
Staying ahead
Cloudforce One (Cloudflare’s threat operations team) proactively monitors emerging campaigns in their formative stages and publishes advisories and detection model updates to ensure our customers are protected. While this specific campaign is focused on SVB, the tactics seen are no different to other similar campaigns that our global network sees every day and automatically stops them before it impacts our customers.
Having a blend of strong technical controls across multiple communication channels along with a trained and vigilant workforce that is aware of the dangers posed by digital communications is crucial to stopping these attacks from going through.
Learn more about how Cloudflare can help in your own journey towards comprehensive phishing protection by using our Zero Trust services and reach out for a complimentary assessment today.