Post Syndicated from David Haynes original https://blog.cloudflare.com/fixing-recent-validation-vulnerabilities-in-octorpki/
A number of vulnerabilities in Resource Public Key Infrastructure (RPKI) validation software were disclosed in a recent NCSC advisory, discovered by researchers from the University of Twente. These attacks abuse a set of assumptions that are common across multiple RPKI implementations, and some of these issues were discovered within OctoRPKI. More details about the disclosed vulnerabilities can be found in this RIPE labs article written by one of the researchers. In response, we published a new release of OctoRPKI, v1.4.0, to address and remediate these vulnerabilities.
Cloudflare customers do not have to take any action to protect themselves from these newly discovered vulnerabilities, and no Cloudflare customer data was ever at risk.
We have not seen any attempted exploitation of these vulnerabilities described in the advisory. We use OctoRPKI to perform Border Gateway Protocol (BGP) route validation so that our routers know where to direct IP packets at Layer 3 of the TCP/IP stack. TLS provides additional security at the TCP layer to ensure the integrity and confidentiality of customer data going over the Internet in the event of BGP hijacking.
RPKI and the discovered vulnerabilities
Resource Public Key Infrastructure (RPKI) is a cryptographic method of signing records that associate a BGP route announcement with the correct originating Autonomous System (AS) number. In order to validate the records that contain that information we use an open source software called OctoRPKI that is part of the cfrpki toolkit.
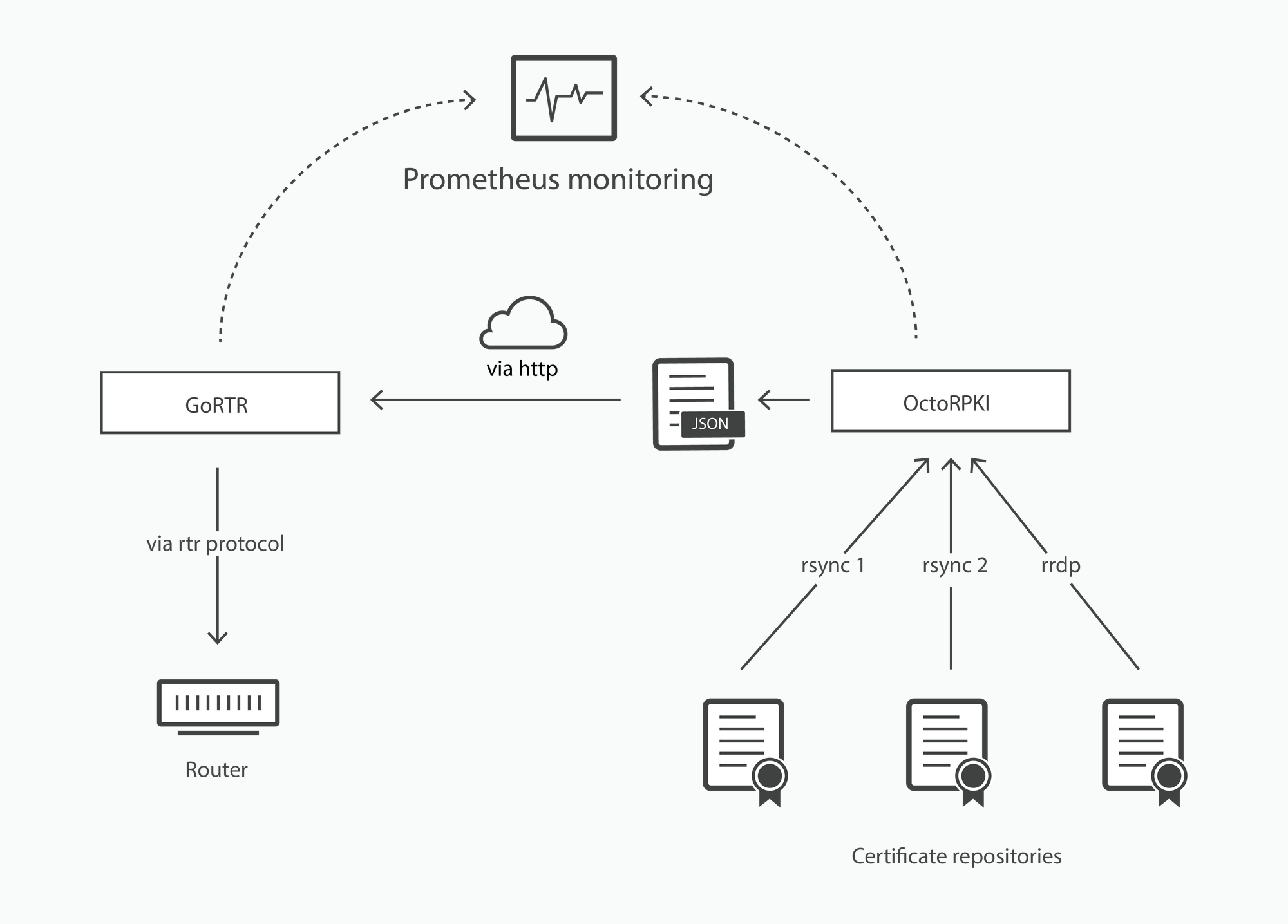
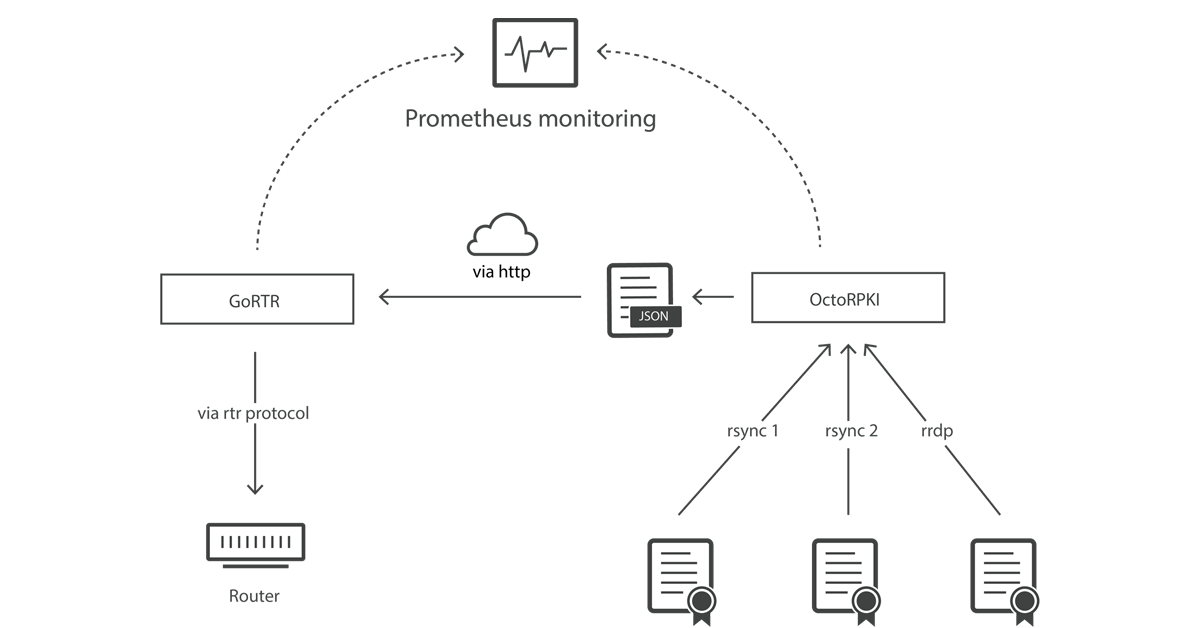
OctoRPKI traverses a set of trusted certificate repositories, downloads all the records and manifests that they contain, and performs a set of validation checks on them. If they are valid, OctoRPKI will add their contents into a JSON file that is made available for GoRTR instances to consume.
RFC6481 further defines the role of certificate repositories:
To validate attestations made in the context of the Resource Public
Key Infrastructure (RPKI) [RFC6480], relying parties (RPs) need
access to all the X.509/PKIX Resource Certificates, Certificate
Revocation Lists (CRLs), and signed objects that collectively define
the RPKI.
Each issuer of a certificate, CRL, or a signed object makes it
available for download to RPs through the publication of the object
in an RPKI repository.
The repository system is a collection of all signed objects that MUST
be globally accessible to all RPs. When certificates, CRLs and
signed objects are created, they are uploaded to a repository
publication point, from whence they can be downloaded for use by RPs.
The main list of trusted repositories that OctoRPKI uses can be found here. In general, OctoRPKI will attempt to process any file that it downloads from a repository. However, this leaves validation software open to processing malicious input. For example, OctoRPKI could be instructed to download and cache a file which contains a path that performs directory traversal, or it could be provided with a classic GZIP bomb attack leading to a crash. The RFC does not necessarily define limits on content within files returned by a repository and thus, a large number of undefined behaviors can occur.
Compounding this issue is the fact that any single repository in the chain of trust could introduce undefined behavior. Imagine a scenario where a malicious entity is able to compromise a single repository (there can be hundreds) within a trusted organization, or is able to introduce a malicious Trust Anchor Locator (TAL) file onto the host machine that is running OctoRPKI. In both cases, bad actors can attempt to trigger undefined behavior on machines running OctoRPKI by leveraging the fact that OctoRPKI will attempt to process arbitrary input. Our mitigations were primarily to fail closed whenever these events occurred as there is no other guidance in the RFC.
Undefined Behavior
There were two classes of attacks disclosed in the NSCS advisory that affected OctoRPKI:
Arbitrary File Writes
- CVE-2021-3907 – Arbitrary filepath traversal via URI injection
Impact
OctoRPKI does not escape a URI with a filename containing “..”, which allows a malicious repository to create a file, for example rsync://example.org/repo/../../etc/cron.daily/evil.roa, which would then be written to disk outside the base cache folder. This could allow for remote code execution on the host machine OctoRPKI is running on.
Mitigation
In v1.4.0 we now filter URIs and force them to remain in the cache folder by overriding any upwards directory traversal.
Crash or uncontrolled resource consumption
- CVE-2021-3908 – Infinite certificate chain depth results in OctoRPKI running forever
- CVE-2021-3909 – Infinite open connection causes OctoRPKI to hang forever
- CVE-2021-3910 – NUL character in ROA causes OctoRPKI to crash
- CVE-2021-3911 – Misconfigured IP address field in ROA leads to OctoRPKI crash
- CVE-2021-3912 – OctoRPKI crashes when processing GZIP bomb returned via malicious repository
Impact
All of these trigger either a crash or infinite runtime by abusing the fact that OctoRPKI will process any file it ingests. For a production critical service it is imperative that undefined behavior is identified early, and either tossed away or caught and presented to the user as an error. Consistent crashes of OctoRPKI can lead to denial of service type attacks.
Mitigation
We implemented bounds checking across many components within OctoRPKI. These include adding instances of checking array length before attempting to index specific locations, or other cases where we utilized built in controls that Go provides when using an HTTP client. Repositories that attempt to abuse bounds checks are either skipped or included in an error message presented to the user.
On our commitment to RPKI security
We are ecstatic to see quality security research, like the vulnerabilities discovered by researchers from the University of Twente, being performed in the RPKI space. It is an incredible sign of progress in the deployment of RPKI, especially considering how recent widespread adoption has been. We are committed to ongoing support of RPKI and look forward to continuing to work with the security community to make the Internet safer and more secure for everyone.