Post Syndicated from Noelle Gotthardt original https://blog.cloudflare.com/inline-dlp-ga/

This post is also available in 简体中文, 日本語, Deutsch, Français and Español.

In July 2022, we announced beta access to our newest Zero Trust product, Data Loss Prevention (DLP). Today, we are even more excited to announce that DLP is Generally Available to customers! Any customer can now get visibility and control of sensitive data moving into, out of, and around their corporate network. If you are interested, check out the bottom of this post.
What is DLP?
Data Loss Prevention helps you overcome one of their biggest challenges: identifying and protecting sensitive data. The migration to the cloud has made tracking and controlling sensitive information more difficult than ever. Employees are using an ever-growing list of tools to manipulate a vast amount of data. Meanwhile, IT and security managers struggle to identify who should have access to sensitive data, how that data is stored, and where that data is allowed to go.
Data Loss Prevention enables you to protect your data based on its characteristics, such as keywords or patterns. As traffic moves into and out of corporate infrastructure, the traffic is inspected for indicators of sensitive data. If the indicators are found, the traffic is allowed or blocked based on the customers’ rules.
The most common use for DLP is the protection of Personally Identifiable Information (PII), but many customers are interested in protecting intellectual property, source code, corporate financial information, or any other information vital to the business. Proper data usage can include who used the data, where the data was sent, and how the data is stored.
How does DLP see my corporate traffic?
DLP is part of Cloudflare One, our Zero Trust network-as-a-service platform that connects users to enterprise resources. Cloudflare One runs traffic from data centers, offices, and remote users, through the Cloudflare network. This offers a wide variety of opportunities to secure the traffic, including validating identity and device posture, filtering corporate traffic to protect from malware and phishing, checking the configurations on SaaS applications, and using Browser Isolation to make web surfing safer for employees. All of this is done with the performance of our global network and managed with one control plane.
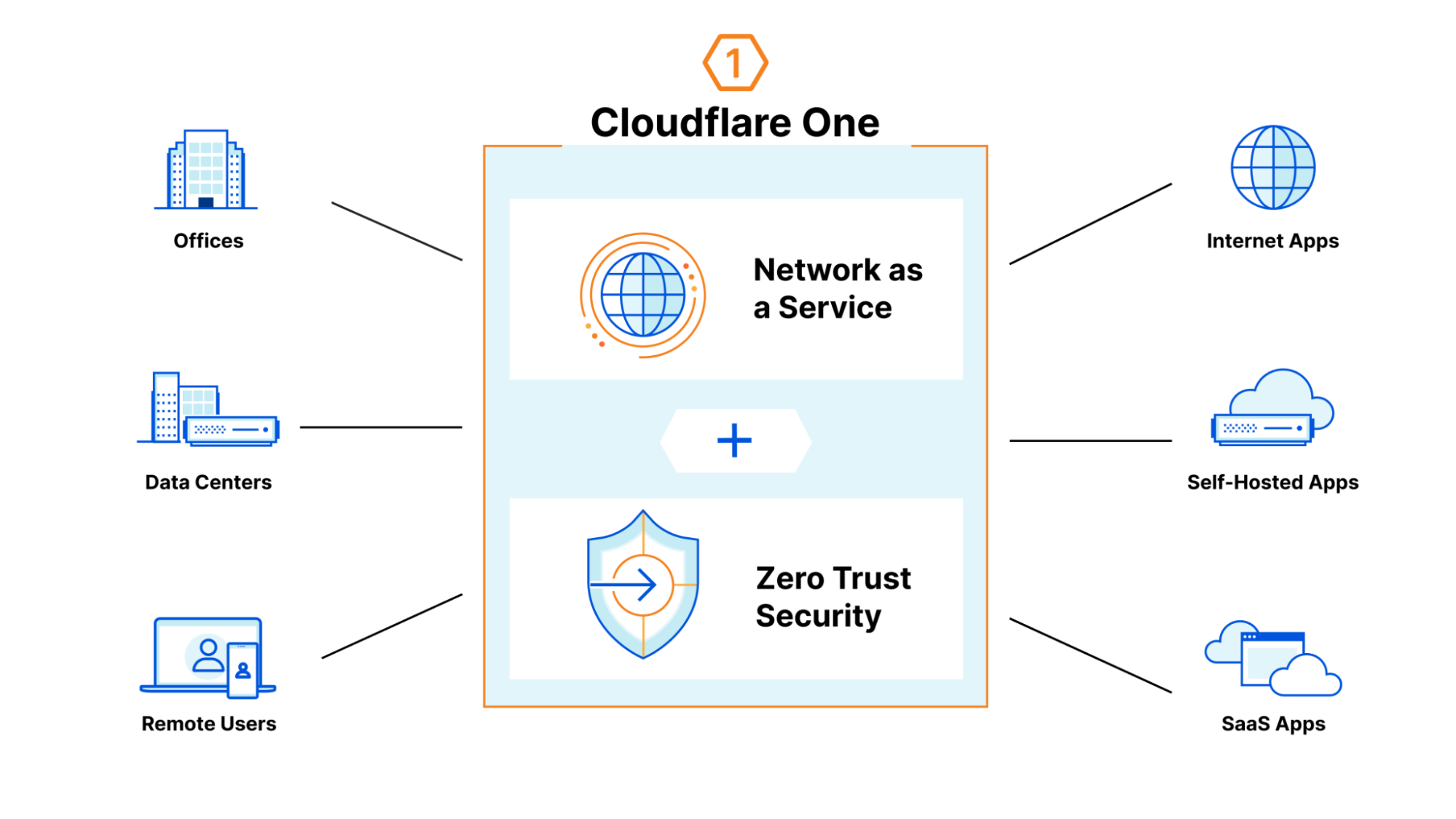
How does it work?
DLP leverages the HTTP filtering abilities of Cloudflare One. As your traffic runs through our network, you can apply rules and route traffic based on information in the HTTP request. There are a wide variety of options for filtering, such as domain, URL, application, HTTP method, and many more. You can use these options to segment the traffic you wish to DLP inspect.
When DLP is applied, the relevant HTTP requests are decompressed, decoded, and scanned for regex matches. Numeric regex matches are then algorithmically validated when possible, such as with checksum calculations or Luhn’s algorithm. However, some numeric detections do not adhere to algorithmic validation, such as US Social Security numbers.
If sensitive data is identified by the detection, the data transfer can be allowed or blocked according to the customer’s ruleset.
How do I use it?
Let’s dive further in to see how this all actually comes to life. To use DLP in the Zero Trust Dashboard, navigate to the DLP Profiles tab under Gateway:
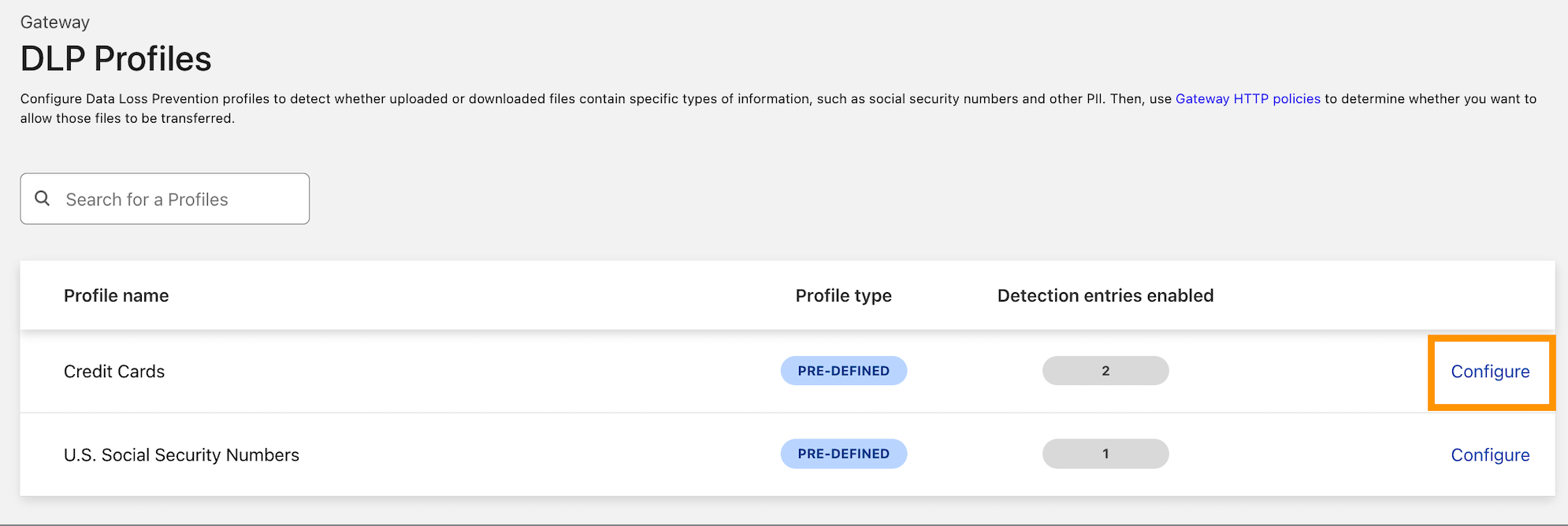
Decide on the type of data you want to protect. We currently detect credit card numbers and US Social Security numbers, but this is where we intend to grow a robust library of DLP detections. Our next steps are custom and additional predefined detections, including more international identifiers and financial record numbers, which will be arriving soon.
When you have decided, select Configure to enable detections:
Enable the detections you want to use. As described above, these card number detections are made using regexes and validated with Luhn’s algorithm. You can make numeric detections for card numbers or detect strings matching card names, such as “American Express.”
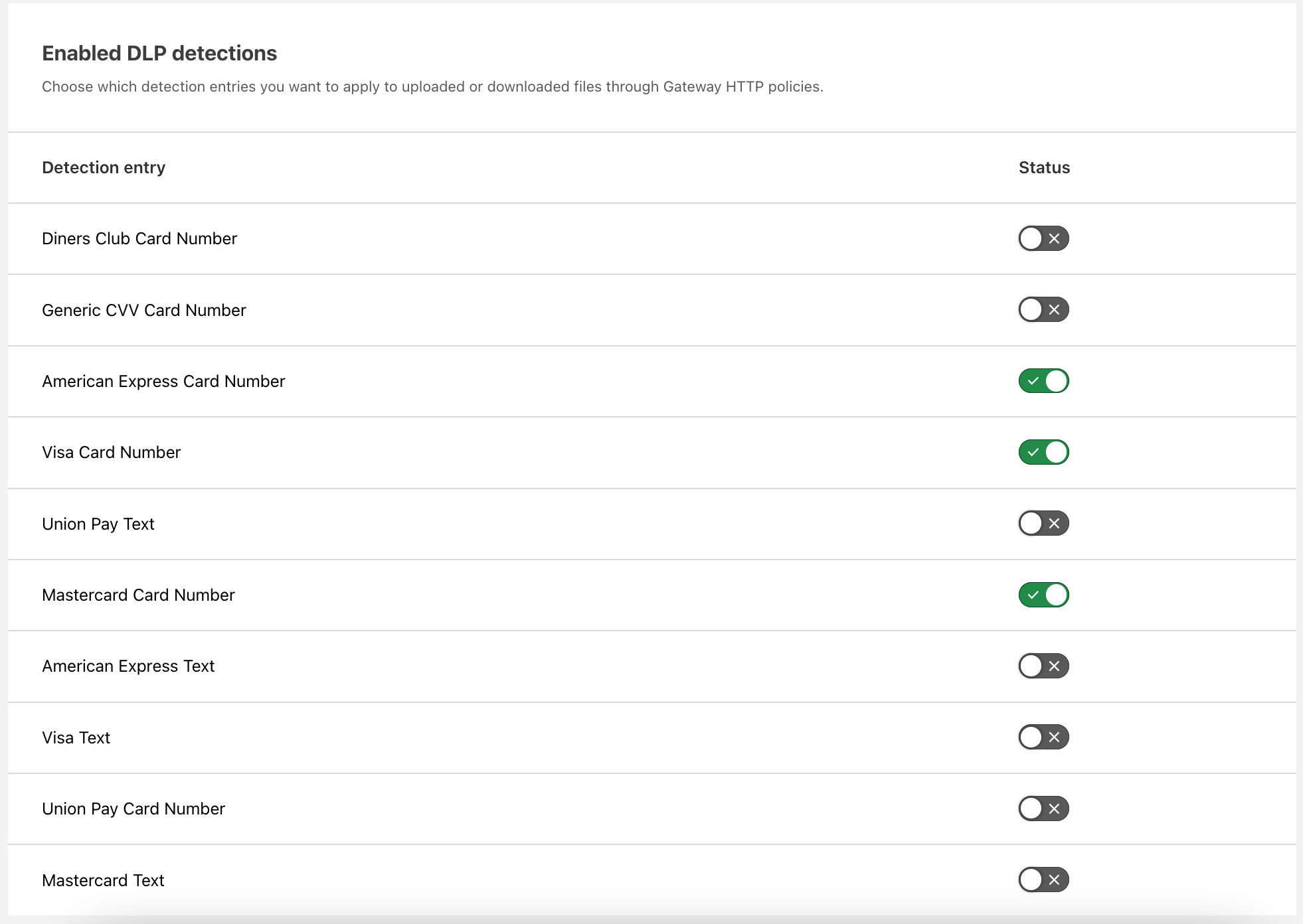
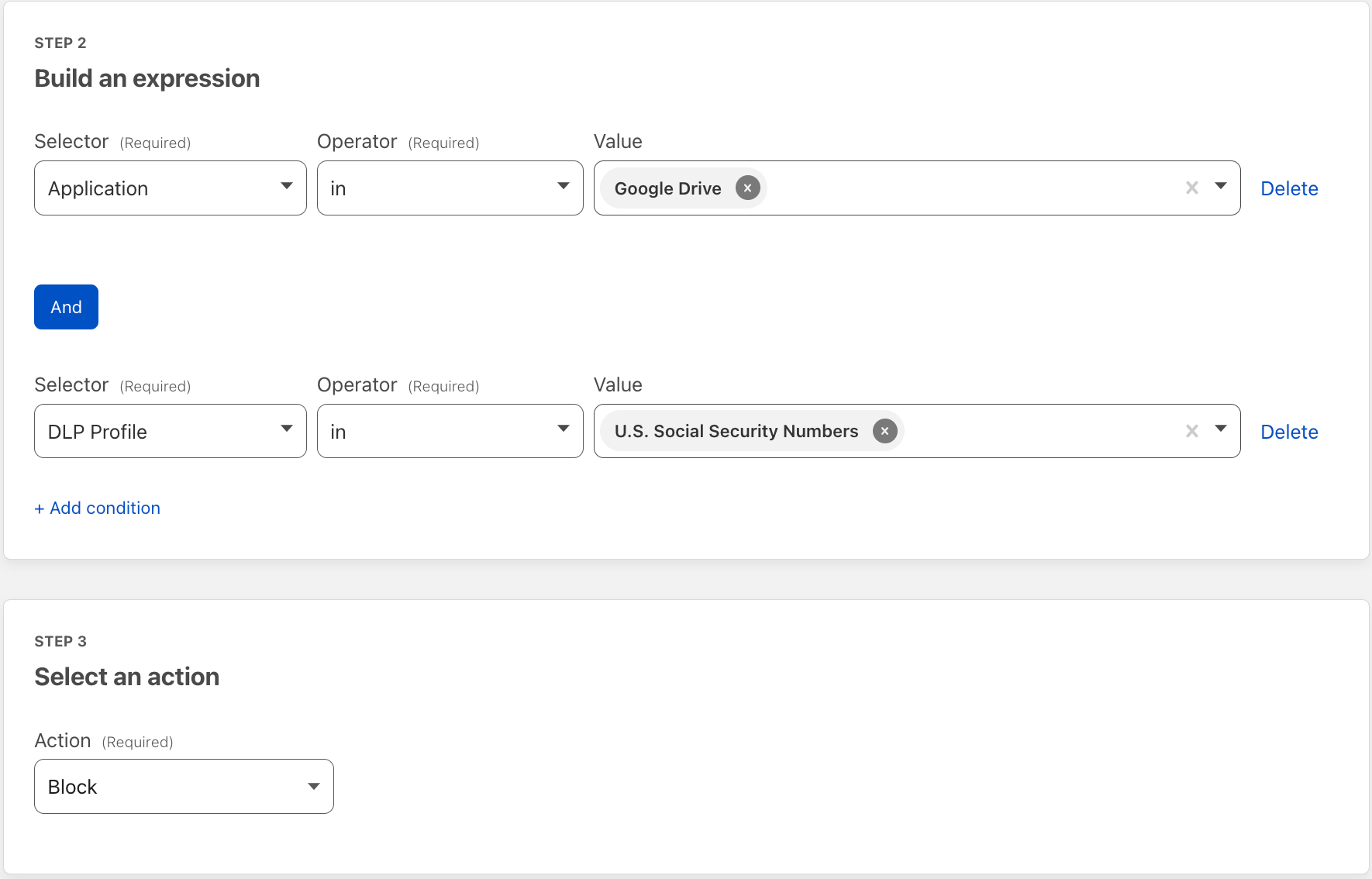
Then apply the detections to a Gateway HTTP policy on the traffic of your choosing. Here we applied DLP to Google Drive traffic. This policy will block uploads and downloads to Google Drive that contain US Social Security Numbers.
Holistic data protection with Cloudflare Zero Trust
Inspecting HTTP traffic for the presence of sensitive data with DLP is one critical way organizations can reduce the risk of data exfiltration, strengthen regulatory compliance, and improve overall data governance.
Implementing DLP is just one step towards a more holistic approach to securing data.
To that end, our Cloudflare Zero Trust platform offers more comprehensive controls over how any user on any device accesses and interacts with data – all from a single management interface:
- To protect data in transit, administrators can enforce identity-aware, granular access policies with our Zero Trust Network Access (ZTNA) service or leverage our in-line Secure Web Gateway (SWG) to apply corporate tenant controls per application.
- Our Remote Browser Isolation (RBI) service can control how users interact with data used within a browser – for example, restricting the downloading, the copy/pasting, and printing of data onto local devices.
- For data at rest, our API-based Cloud Access Security Broker (CASB) – announced as generally available today! – detects if misconfigurations in SaaS applications can lead to data leakage.
We have architected our DLP service to work seamlessly with these ZTNA, SWG, CASB, and other security services. As we continue to deepen our DLP capabilities, this platform approach uniquely equips us to address our customers’ needs with flexibility.
Get Access to Data Loss Prevention
To get access to DLP, reach out for a consultation, or contact your account manager.