Post Syndicated from Wesley Evans original http://blog.cloudflare.com/fr-fr/post-quantum-cryptography-ga-fr-fr/
Au cours des douze derniers mois, nous avons parlé de la nouvelle référence en matière de chiffrement sur Internet : la cryptographie post-quantique. Durant la Semaine anniversaire, l’année dernière, nous avons annoncé que notre version bêta de Kyber était disponible à des fins de test, et que Cloudflare Tunnel pouvait être mis en œuvre avec la cryptographie post-quantique. Au début de l’année, nous avons clairement indiqué que nous estimons que cette technologie fondamentale devait être accessible à tous, gratuitement et pour toujours.
Aujourd’hui, nous avons franchi une étape importante, après six ans et 31 articles de blog : nous lançons le déploiement de la prise en charge de la cryptographie post-quantique en disponibilité générale1 pour nos clients, nos services et nos systèmes internes ; nous le décrivons plus en détail ci-dessous. Ce déploiement inclut des produits tels que Pingora pour la connectivité aux serveurs d’origine, 1.1.1.1, R2, le routage intelligent Argo, Snippets et bien d’autres.
Il s’agit d’une étape importante pour Internet. Nous ne savons pas encore quand les ordinateurs quantiques deviendront suffisamment puissants pour briser la cryptographie actuelle, mais les avantages qu’offre l’adoption de la cryptographie post-quantique sont aujourd’hui manifestes. Des connexions rapides et une sécurité pérenne sont désormais possibles, grâce aux progrès accomplis par Cloudflare, Google, Mozilla, NIST (National Institute of Standards and Technology) des États-Unis, Internet Engineering Task Force et de nombreuses institutions universitaires.
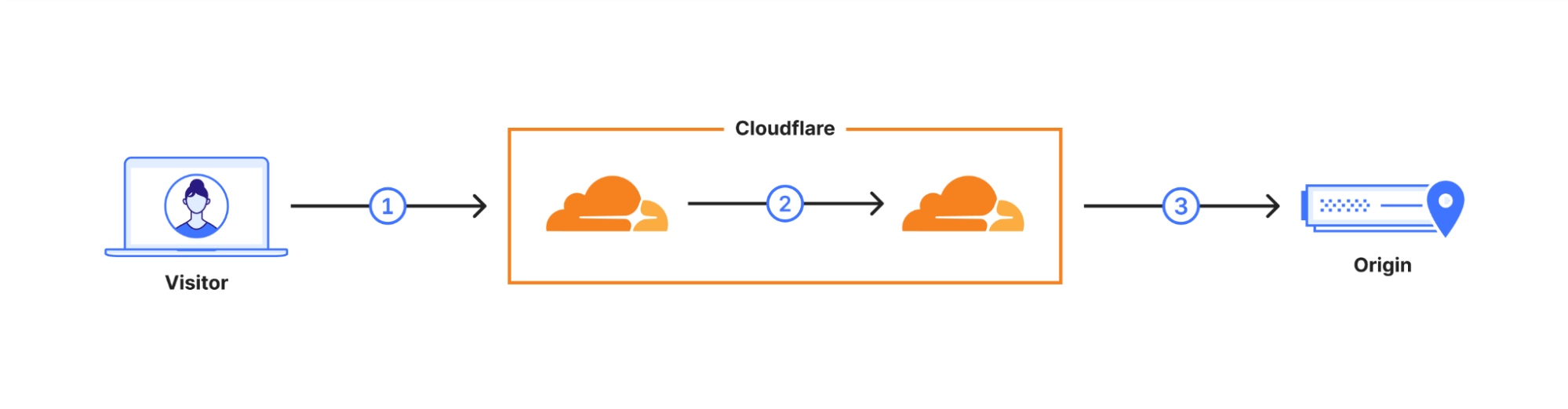
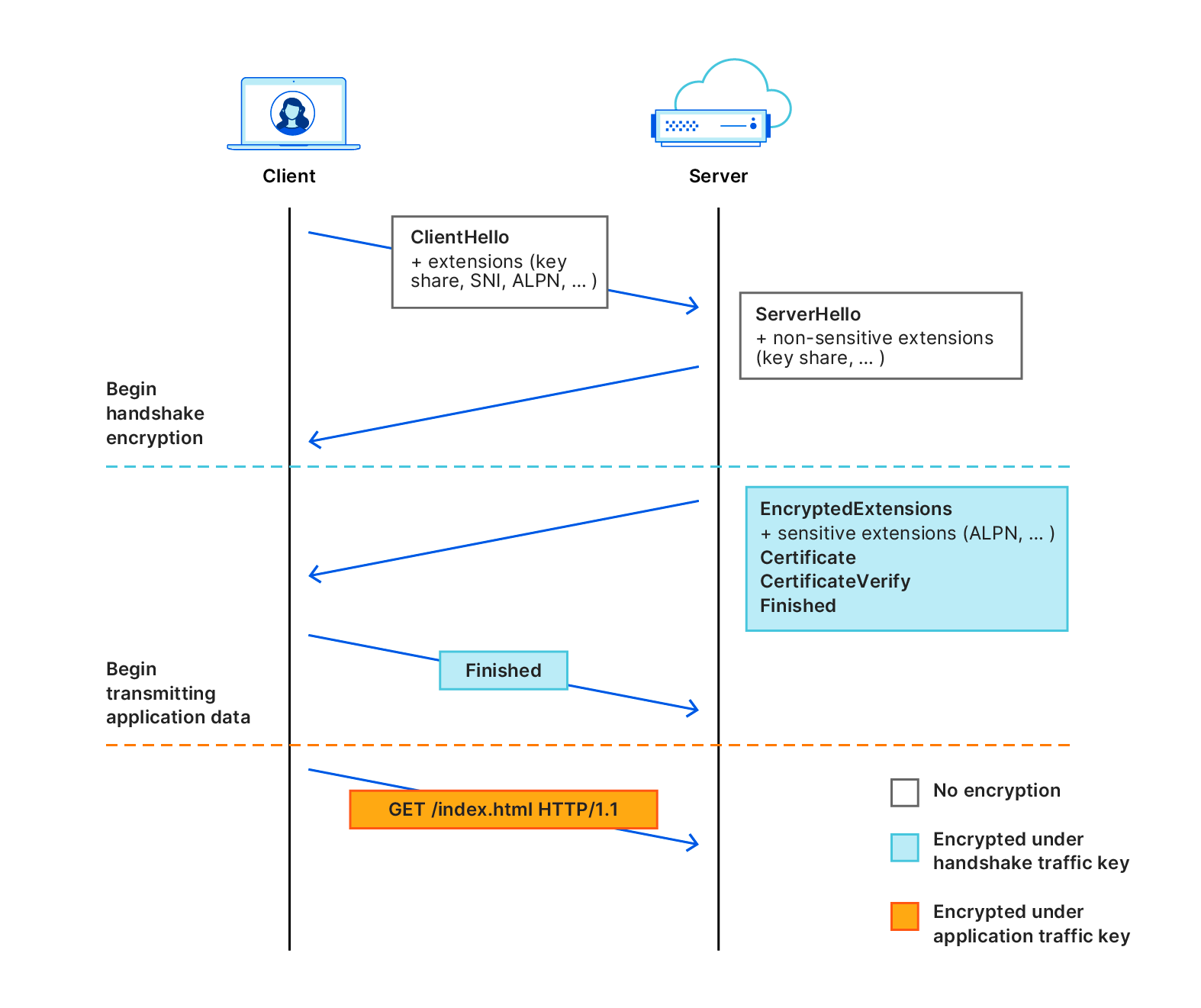
Qu’entend-on par « disponibilité générale » ? En octobre 2022, nous avons déployé X25519+Kyber sous forme de version bêta pour l’ensemble des sites web et API servis par l’intermédiaire de Cloudflare. Cependant, un tango se danse à deux, et une connexion n’est donc sécurisée que si le navigateur prend également en charge la cryptographie post-quantique. À partir d’août 2023, Chrome activera progressivement X25519+Kyber, par défaut.
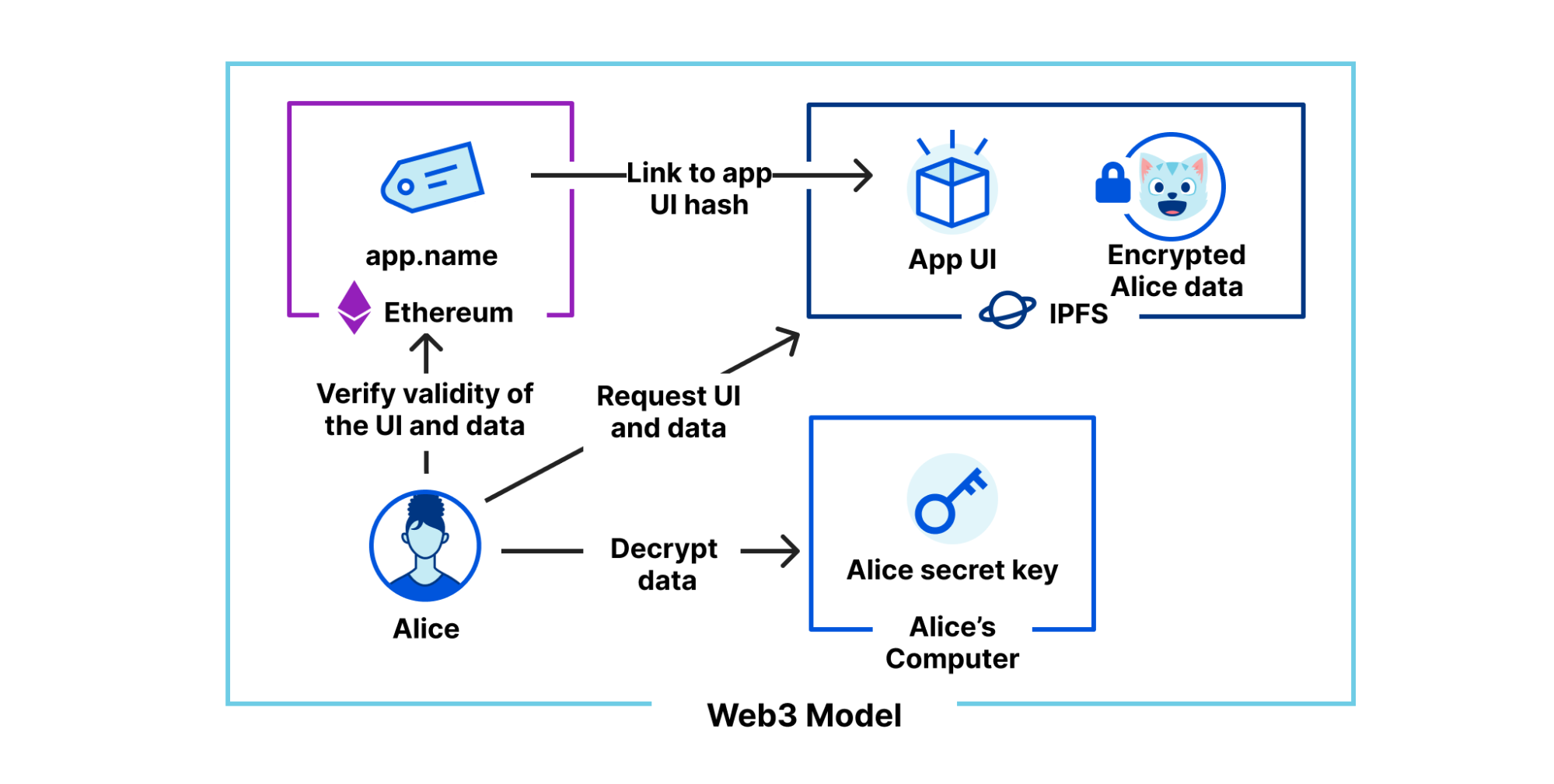
La requête de l’utilisateur est acheminée sur le réseau de Cloudflare (2). Nous avons amélioré un grand nombre de nos connexions internes afin d’utiliser la cryptographie post-quantique, et nous prévoyons de finaliser l’amélioration de toutes nos connexions internes d’ici fin 2024. La dernière liaison demeure donc la connexion (3) entre Cloudflare et le serveur d’origine.
Nous sommes heureux d’annoncer que nous déployons la prise en charge de X25519+Kyber en disponibilité générale pour la plupart des connexions entrantes et sortantes dans le cadre d’une utilisation comprenant les serveurs d’origine et les commandes fetch() de Cloudflare Workers.
| Plan | Prise en charge des connexions sortantes post-quantiques |
|---|---|
| Gratuit | Début du déploiement. Objectif : 100 % d’ici fin octobre. |
| Pro et Business | Objectif : 100 % d’ici la fin de l’année. |
| Enterprise | Le déploiement commencera en février 2024. 100 % d’ici mars 2024. |
Nous transmettrons régulièrement à nos clients Enterprise des informations supplémentaires au cours des six prochains mois, afin de les aider à se préparer au déploiement. Les clients des offres Pro, Business et Enterprise peuvent ignorer le déploiement et s’inscrire dès aujourd’hui dans leur zone, ou se désinscrire à l’avance via une API, décrite dans l’article de blog associé. Avant le déploiement pour les clients de l’offre Enterprise en février 2024, nous ajouterons une option de désinscription au tableau de bord.
Si vous êtes impatient(e) de vous lancer maintenant, consultez notre article de blog contenant les informations techniques détaillées et activez la prise en charge de la cryptographie post-quantique via l’API.
Qu’est-ce qui est inclus et qu’est-ce qui va suivre ?
Avec une amélioration de cette ampleur, nous voulions d’abord prioriser les produits les plus utilisés, puis étendre le déploiement pour prendre en charge les scénarios d’utilisation particuliers. Cette approche nous a conduits à inclure les produits et systèmes suivants dans ce déploiement :
| 1.1.1.1 |
| AMP (Accelerated Mobile Pages) |
| Passerelle API Gateway |
| Routage intelligent Argo |
| Auto Minify |
| Optimisation automatique de plateforme |
| Échanges signés automatiques |
| Trafic sortant de Cloudflare |
| Cloudflare Images |
| Ensemble de règles de Cloudflare |
| Cloudflare Snippets |
| Cloudflare Tunnel |
| Pages d’erreur personnalisée |
| Surveillance fondée sur les flux |
| Contrôles d’intégrité |
| Hermes |
| Host Head Checker |
| Magic Firewall |
| Magic Network Monitoring |
| Journalisation des erreurs réseau |
| Project Flame |
| Quicksilver |
| R2 Storage |
| Request Tracer |
| Rocket Loader |
| Speed sur le tableau de bord de Cloudflare |
| SSL/TLS |
| Traffic Manager |
| Pare-feu WAF, règles gérées |
| Waiting Room |
| Web Analytics |
Si un produit ou un service que vous utilisez ne figure pas dans cette liste, c’est que le déploiement de la cryptographie post-quantique n’a pas encore débuté pour ce produit. Nous travaillons activement au déploiement de la cryptographie post-quantique pour tous nos produits et services, notamment nos produits Zero Trust. Jusqu’à ce que tous nos systèmes prennent en charge la cryptographie post-quantique, nous publierons un article de blog proposant des informations mises à jour à l’occasion de chaque Innovation Week. Cet article présentera les produits pour lesquels nous avons déployé la cryptographie post-quantique, ceux qui en bénéficieront prochainement et ceux pour lesquels la prise en charge est encore à l’horizon.
Voici les produits pour lesquels nous développons la prise en charge de la cryptographie post-quantique :
| Cloudflare Gateway |
| DNS Cloudflare |
| Service d’équilibrage de charge de Cloudflare |
| Cloudflare Access |
| Always Online |
| Zaraz |
| Journalisation |
| D1 |
| Cloudflare Workers |
| Cloudflare WARP |
| Gestion des bots |
Pourquoi maintenant ?
Comme nous l’avons annoncé plus tôt cette année, la cryptographie post-quantique sera incluse gratuitement dans tous les produits et services Cloudflare compatibles. La meilleure technologie de chiffrement devrait être accessible à tous, gratuitement, afin de contribuer à la protection de la confidentialité et des droits de l’homme dans le monde entier.
Comme nous l’avons indiqué en mars dernier :
«Ce qui était autrefois une frontière expérimentale est devenu le substrat sous-jacent de la société moderne. Il est présent dans nos infrastructures les plus critiques, à l’image des réseaux électriques, des hôpitaux, des aéroports et des banques. Nous lui confions nos souvenirs les plus précieux. Nous lui confions nos secrets. C’est pourquoi l’Internet doit être privé par défaut, et doit également être sécurisé par défaut.»
Nos travaux sur la cryptographie post-quantique sont motivés par la théorie selon laquelle les ordinateurs quantiques, capables de briser la cryptographie conventionnelle, sont à l’origine d’un problème comparable à celui du bug de l’an 2000. Nous savons qu’il y aura, à l’avenir, un problème qui pourrait avoir des répercussions catastrophiques sur les utilisateurs, les entreprises et même les États-nations. La différence, cette fois, c’est que nous ne connaissons pas la date et l’heure auxquelles se produira cette véritable rupture du paradigme informatique. Pire encore, tout trafic capturé aujourd’hui pourrait être déchiffré à l’avenir. Nous devons donc nous préparer dès aujourd’hui à cette menace.
Nous sommes impatients de voir tous les utilisateurs adopter la cryptographie post-quantique sur leurs systèmes. Pour suivre les derniers développements du déploiement de la cryptographie post-quantique et de la prise en charge de clients/serveurs tiers, consultez pq.cloudflareresearch.com et suivez ce blog.
***
1Nous utilisons une version préliminaire de Kyber, le choix de l’institut NIST pour les accords de clé post-quantique. Kyber n’a pas été finalisé ; nous nous attendons à la publication d’une norme définitive en 2024, sous le nom « ML-KEM ». Nous l’adopterons alors rapidement, tout en mettant fin à la prise en charge de X25519Kyber768Draft00.