Post Syndicated from Ayush Kumar original http://blog.cloudflare.com/cloudflare-email-security-now-works-with-crowdstrike-falcon-logscale/


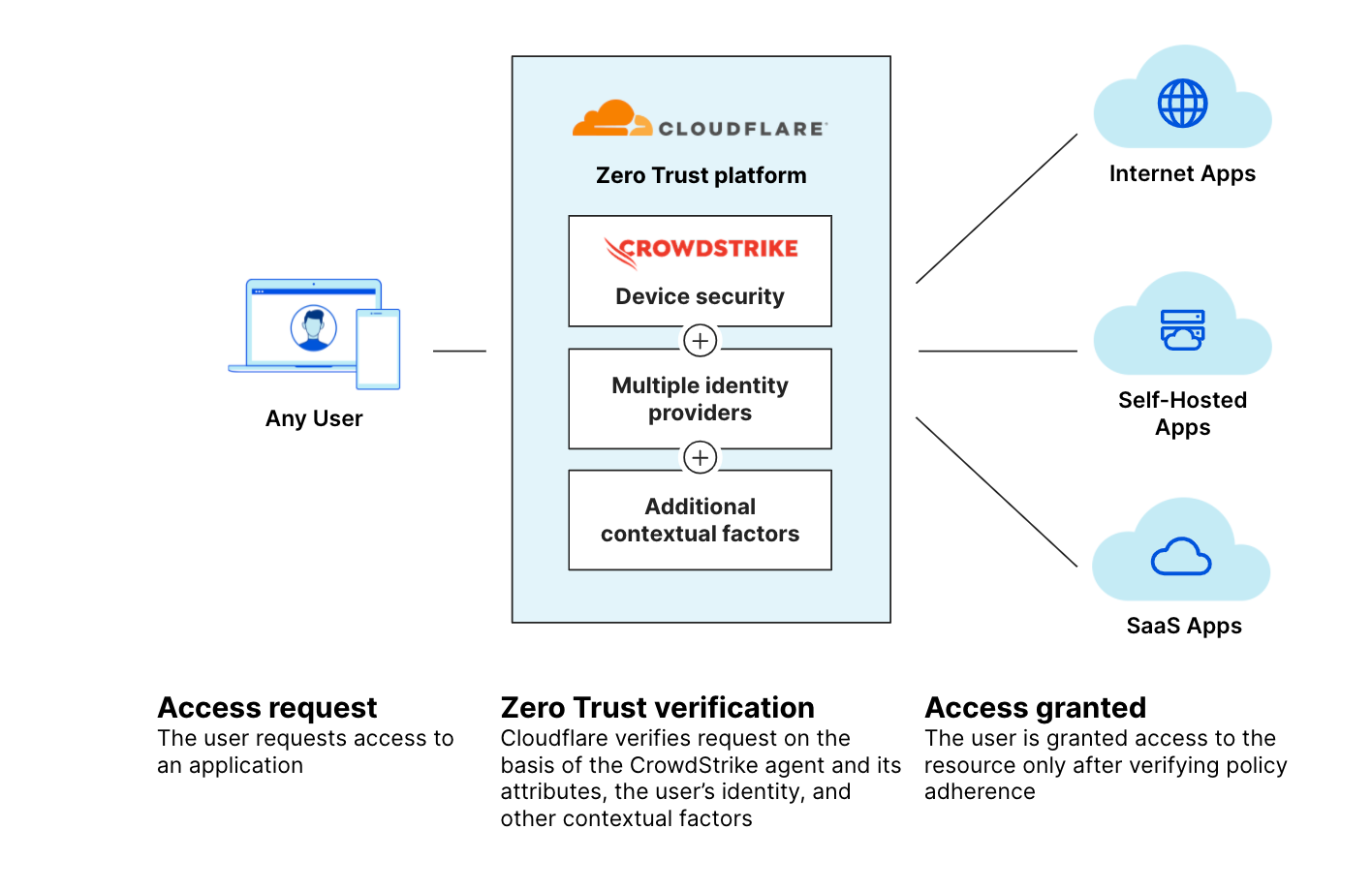
We are excited to announce an extended partnership between CrowdStrike and Cloudflare to bring together Cloudflare Email Security and CrowdStrike Falcon® LogScale. With this integration, joint customers who have both Falcon LogScale and Cloudflare Email Security can now send detection data to be ingested and displayed within their Falcon LogScale dashboard.
What is CrowdStrike Falcon LogScale?
CrowdStrike Falcon LogScale enables organizations to ingest, aggregate and analyze massive volumes of streaming log data from a wide array of sources at petabyte scale. It offers search and visualization capabilities, enabling users to easily query and explore their log data to gain valuable insights and identify security threats or anomalies.
Falcon LogScale helps customers by providing:
Log Ingestion It supports the collection of logs from diverse sources and can handle high volumes of log data in real time.
Real-Time Search Users can perform fast searches across their log data, enabling quick detection and investigation of security incidents or operational issues.
Dashboards and Visualizations Falcon LogScale offers customizable dashboards and visualizations to help teams gain insights from their log data.
All of these capabilities enable proactive threat hunting by leveraging advanced analytics. It helps security teams identify potential threats, detect anomalies, and quickly remediate security incidents. Falcon LogScale is designed to handle large-scale log data ingestion and analysis. It can scale to accommodate growing log volumes and provide consistent performance.
Falcon LogScale is the solution for organizations that are looking to consolidate their log management and analysis efforts. It makes monitoring and securing their environments effective and efficient.
How Cloudflare Email works with Falcon LogScale
Customers who have both Cloudflare Email Security and CrowdStrike Falcon LogScale can now send detection data to Falcon LogScale. Within Falcon LogScale, this detection information can be visualized and queried.
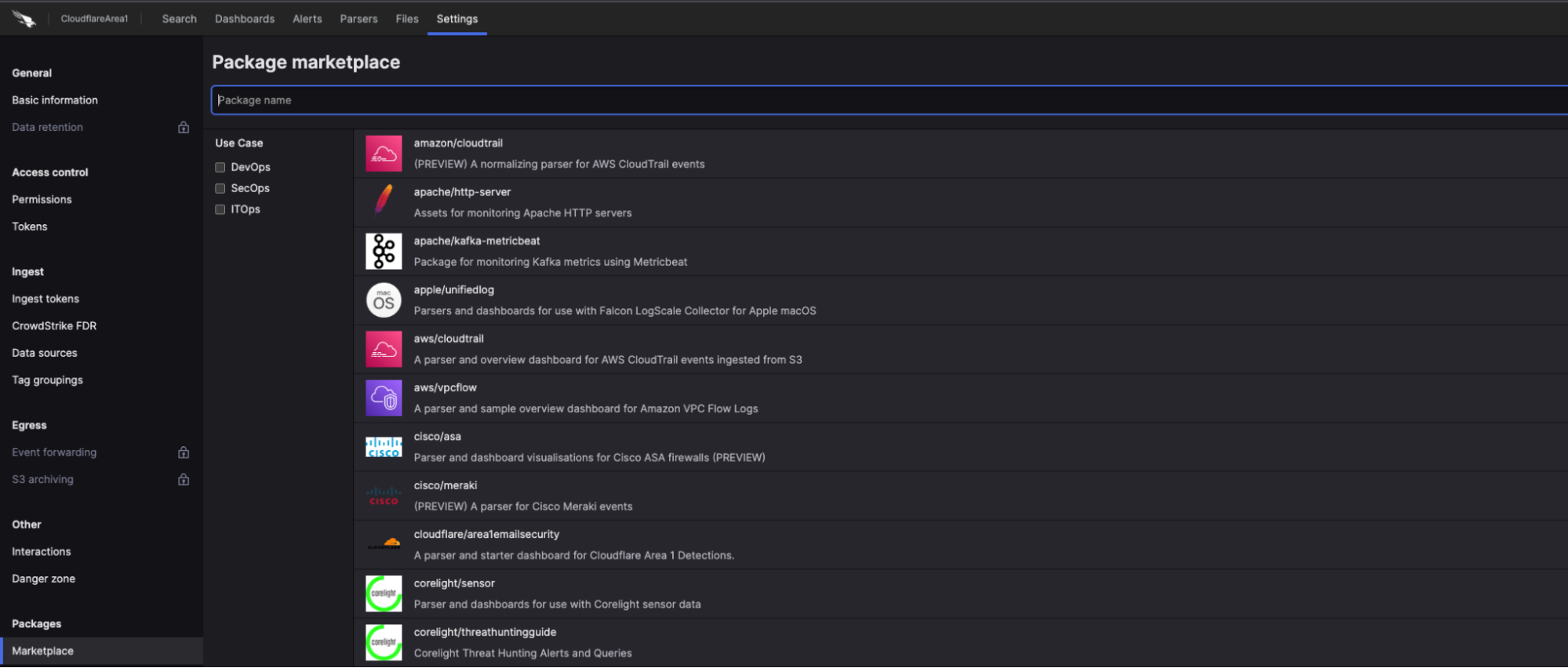
To set up Cloudflare Email Security detections to flow into Falcon LogScale, navigate to the Settings section and choose the Marketplace tab in the lefthand toolbar, as shown in the screenshot below.
After installing the package, an ingest token needs to be generated. Navigate to the “Ingest Tokens” tab under Settings and create one.
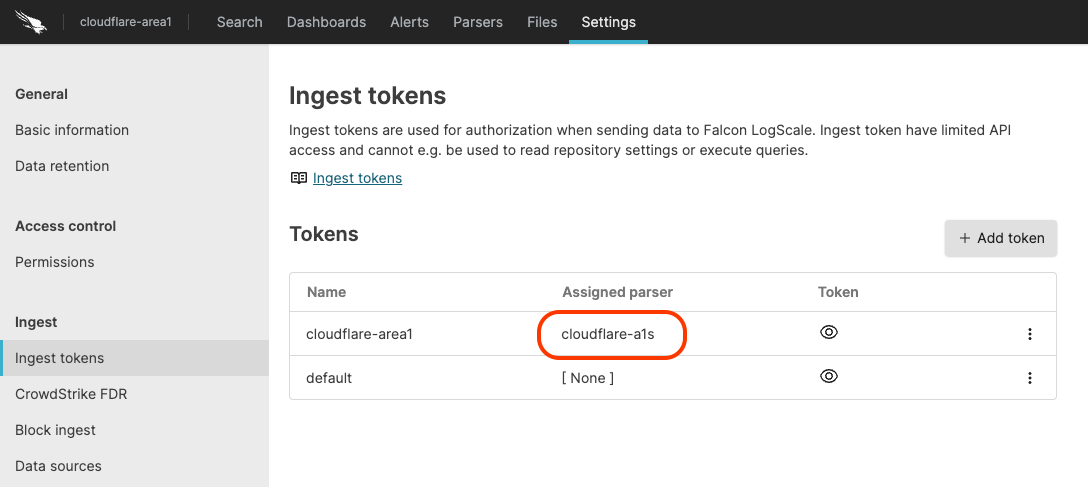
Copy the ingest token to save it for later. From here, customers can navigate to the Cloudflare Email Security dashboard, go to the Settings section, select the Alert Webhooks tab and choose “+ New Webhook”. Then click the SIEM option, choose Other from the dropdown, and input the following information:
Auth Token: Bearer [INGEST TOKEN]
Target: https://cloud.community.humio.com/api/v1/ingest/hec/raw
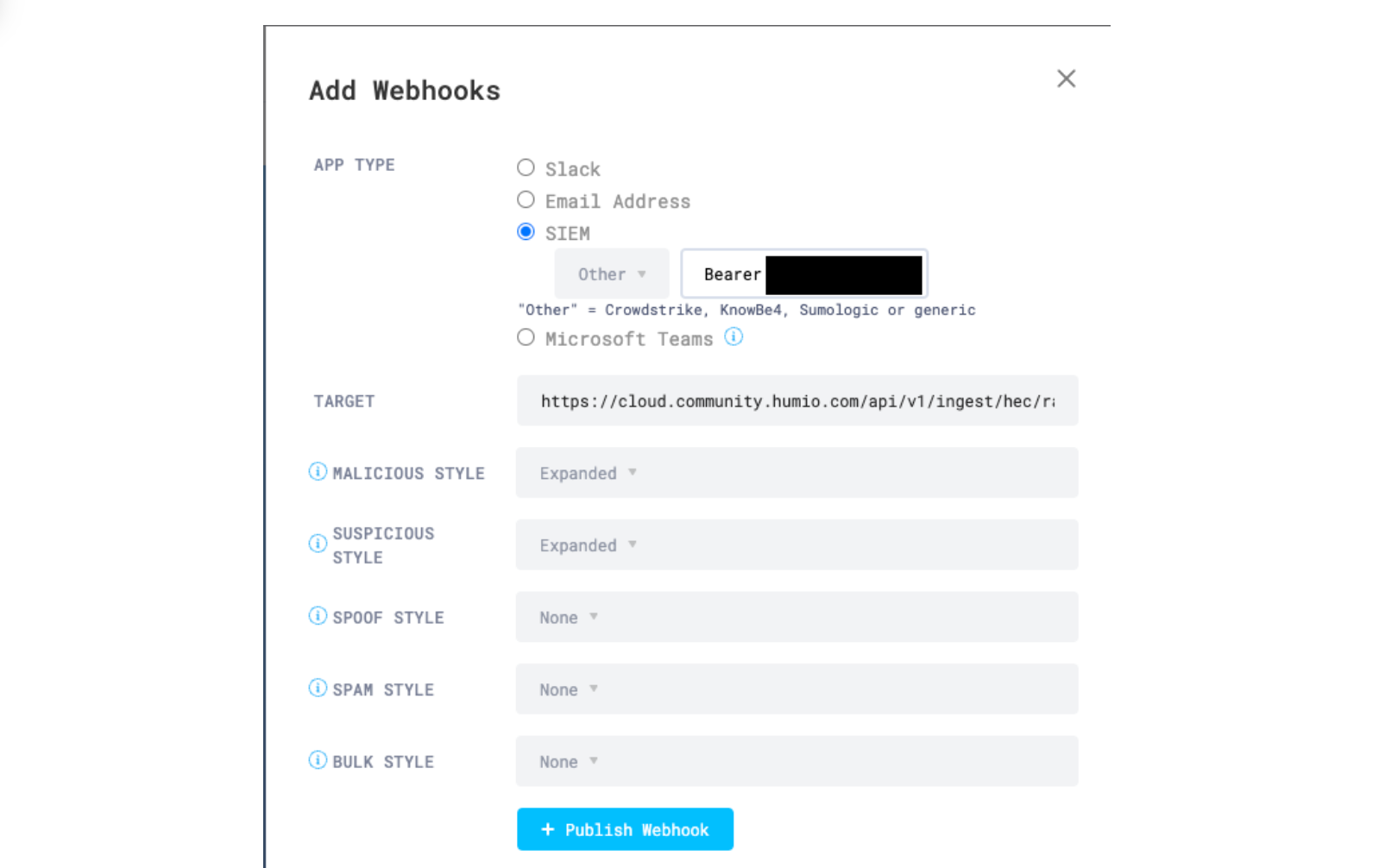
Customers can choose which events to send to Falcon LogScale by selecting the expanded option. In the screenshot above, the user has chosen to only send malicious and suspicious detections.
A few minutes after creating a new webhook, Cloudflare Email Security will start sending detection data to the Falcon LogScale instance.
When the Cloudflare Email Security package from the Falcon LogScale marketplace is installed, customers are provided with a parser for field extraction and out-of-box content through a dashboard. The parser allows the Falcon LogScale product to be able to query the detection data while the dashboard allows organizations to quickly get the relevant information about their email security. Below is what the dashboard looks like:
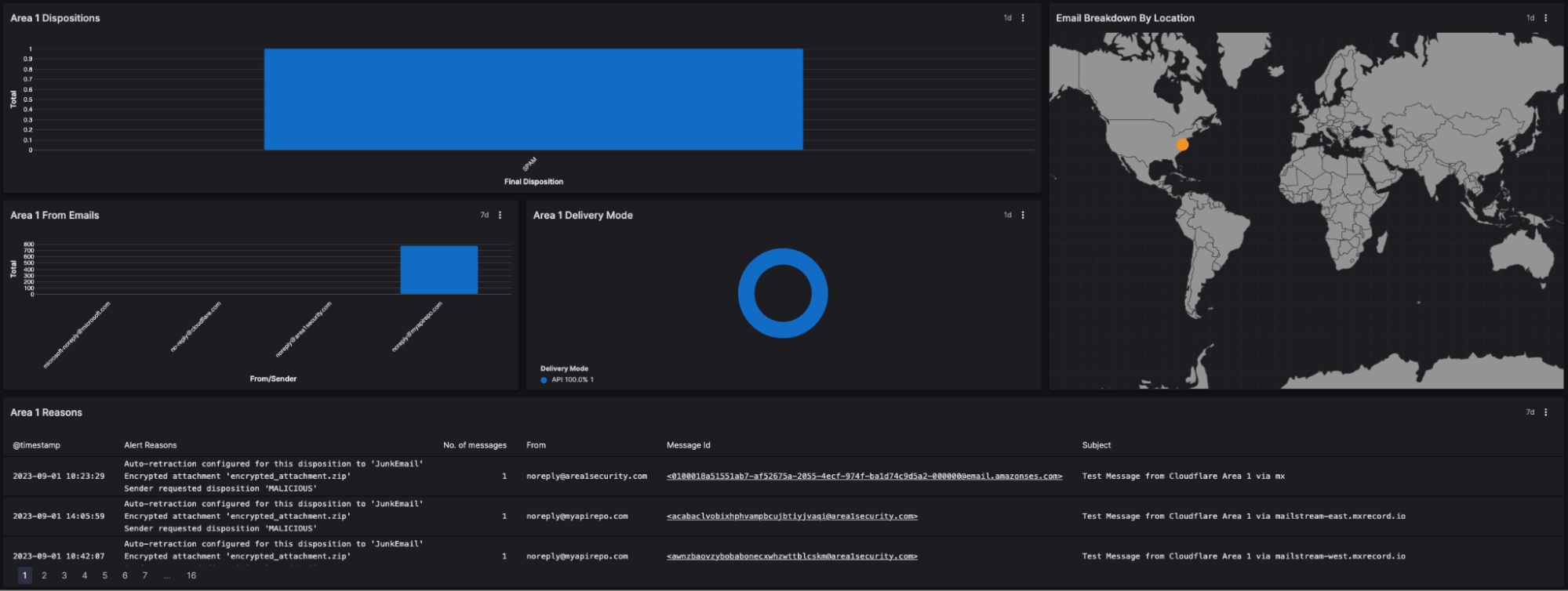
As you can see, we have included visualizations and queries to get teams up and running quickly, but it is meant to be a starting point for customers to build on. Customers can write their own queries and use them to create their own widgets. From there, they can create their own rendition of this dashboard to fit their needs.
More information about setting up this integration can be found here: https://library.humio.com/integrations/integrations-cloudflare-package-area1.html
What’s next
We are currently looking to expand the integration of Cloudflare products with Falcon LogScale. Our plan is to extend the integration to the remaining components of the Zero Trust Suite, enabling the relaying of logs and detection data to Falcon LogScale. This will allow customers to visualize and analyze data from these products, similar to the existing Cloudflare Email Security integration. If you are interested and would like to learn more, please reach out to your Cloudflare account contact.