Post Syndicated from KJ McCann original https://blog.rapid7.com/2022/10/05/whats-new-in-insightidr-q3-2022-in-review/

This Q3 2022 recap post takes a look at some of the latest investments we’ve made to InsightIDR to drive detection and response forward for your organization.
360-degree XDR and attack surface coverage with Rapid7
The Rapid7 XDR suite — flagship InsightIDR, alongside InsightConnect (SOAR), and Threat Command (Threat Intel) — unifies detection and response coverage across both your internal and external attack surface. Customers detect threats earlier and respond more quickly, shrinking the window for attackers to succeed.
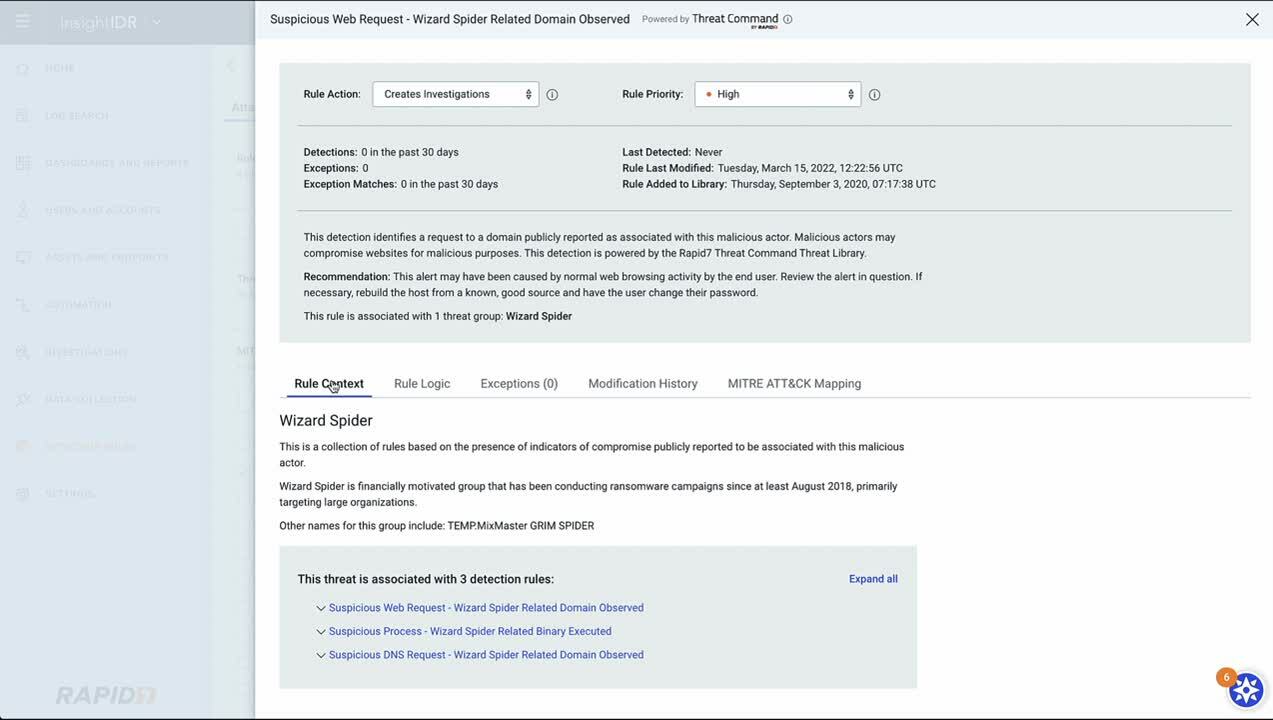
With Threat Command alerts now directly ingested into InsightIDR, receive a more holistic picture of your threat landscape, beyond the traditional network perimeter. By unifying these detections and related workflows together in one place, customers can:
- Manage and tune external Threat Command detections from InsightIDR console
- Investigate external threats alongside context and detections of their broader internal environment
- Activate automated response workflows for Threat Command alerts – powered by InsightConnect – from InsightIDR to extinguish threats faster
Rapid7 products have helped us close the gap on detecting and resolving security incidents to the greatest effect. This has resulted in a safer environment for our workloads and has created a culture of secure business practices.
— Manager, Security or IT, Medium Enterprise Computer Software Company via Techvalidate
Eliminate manual tasks with expanded automation
Reduce mean time to respond (MTTR) to threats and increase confidence in your response actions with the expanded integration between InsightConnect and InsightIDR. Easily create and map InsightConnect workflows to any attack behavior analytics (ABA), user behavior analytics (UBA), or custom detection rule, so tailored response actions can be initiated as soon as an alert fires. Quarantine assets, enrich investigations with more evidence, kick off ticketing workflows, and more – all with just a click.
Preview the impact of exceptions on detection rules
Building on our intuitive detection tuning experience, it’s now easier to anticipate how exceptions will impact your alert volume. Preview exceptions in InsightIDR to confirm your logic to ensure that tuning will yield relevant, high fidelity alerts. Exception previews allow you to confidently refine the behavior of ABA detection rules for specific users, assets, IP addresses, and more to fit your unique environments and circumstances.

Streamline investigations and collaboration with comments and attachments
With teams more distributed than ever, the ability to collaborate virtually around investigations is paramount. Our overhauled notes system now empowers your team to create comments and upload/download rich attachments through Investigation Details in InsightIDR, as well as through the API. This new capability ensures your team has continuity, documentation, and all relevant information at their fingertips as different analysts collaborate on an investigation.

New vCenter deployment option for the Insight Network Sensor
As a security practitioner looking to minimize your attack surface, you need to know the types of data on your network and how much of it is moving: two critical areas that could indicate malicious activity in your environment.
With our new vCenter deployment option, you can now use distributed port mirroring to monitor internal east-west traffic and traffic across multiple ESX servers using just a single virtual Insight Network Sensor. When using the vCenter deployment method, choose the GRETAP option via the sensor management page.
First annual VeloCON brings DFIR experts from around the globe together
Rapid7 brought DFIR experts and enthusiasts from around the world together this September to share experiences in using and developing Velociraptor to address the needs of the wider DFIR community.

Velociraptor’s unique, advanced open-source endpoint monitoring, digital forensic, and cyber response platform provides you with the ability to respond more effectively to a wide range of digital forensic and cyber incident response investigations and data breaches.
Watch VeloCON on-demand to see security experts delve into new ideas, workflows, and features that will take Velociraptor to the next level of endpoint management, detection, and response.
A growing library of actionable detections
In Q3, we added 385 new ABA detection rules to InsightIDR. See them in-product or visit the Detection Library for actionable descriptions and recommendations.
Stay tuned!
As always, we’re continuing to work on exciting product enhancements and releases throughout the year. Keep an eye on our blog and release notes as we continue to highlight the latest in detection and response at Rapid7.