Post Syndicated from Carly Ramsey http://blog.cloudflare.com/author/carly/ original https://blog.cloudflare.com/australia-cybersecurity-strategy-is-here-and-cloudflare-is-all-in

We are thrilled about Australia’s strategic direction to build a world-leading cyber nation by 2030. As a world-leading cybersecurity company whose mission is to help build a better Internet, we think we can help.
Cloudflare empowers organizations to make their employees, applications and networks faster and more secure everywhere, while reducing complexity and cost. Cloudflare is trusted by millions of organizations – from the largest brands to entrepreneurs and small businesses to nonprofits, humanitarian groups, and governments across the globe.
Cloudflare first established a footprint in Australia in 2012 when we launched our 15th data center in Sydney (our network has since grown to span over 310 cities in 120 countries/regions). We support a multitude of customers in Australia and New Zealand, including some of Australia’s largest banks and digital natives, with our world-leading security products and services. For example, Australia’s leading tech company Canva, whose service is used by over 35 million people worldwide each month, uses a broad array of Cloudflare’s products — spanning use cases as diverse as remote application access, to serverless development, and even bot management to help Canva protect its network from attacks.
In support of the Australian Cyber Security Strategy 2023-2030 (The Strategy), released on November 22, 2023, we want to share how we can help empower Australian organizations and individuals to become more secure. The Strategy is clear about the value of cooperation and the vital role of the private sector. We couldn’t agree more, and we look forward to collaborating with individuals, industry, non-profits, and the government to help ensure that Australia’s society and economy is protected from malicious cyber threats.
The Strategy outlines six shields – six layers of defense against cyber attacks, with Australian businesses and individuals in the center (where they should be). Here’s where we think Cloudflare can play a role in each of the shields:
Shield 1: Strong businesses and citizens
The Strategy rightly focuses on helping those individuals and organizations that typically do not have the capability or resources to employ basic cybersecurity tools. We agree that supporting the most vulnerable is a crucial goal as these groups are often powerless to protect themselves against relentless attacks. A 2023 survey by the Australian Cyber Security Center shows that 62% of surveyed Small Medium Enterprises (SMEs) were victims of a cyber attack. Cloudflare’s recent survey of nearly 4000 security leaders across Asia Pacific shows that 81% of medium and 77% of small-sized organizations suffered a cybersecurity incident over the previous 12 months.
Here we believe we have a lot to offer. Our mission is to help build a more secure, more private and more reliable Internet. A key part of that mission is democratizing cybersecurity – making cyber tools readily available for all, including SMEs, non-profits, and individuals. For example, our free plan makes available our world-leading DDoS and WAF protection for millions of websites, apps, and APIs all around the world, including in Australia. We provide our suite of Zero Trust Tools for free to organizations with up to 50 users (more on Zero Trust below).
We also offer our world-leading, Enterprise-level cyber protection products and services at no cost to the most vulnerable populations, including human rights organizations, journalists and healthcare organizations. One example of this is Citizens of the Great Barrier Reef, which is a participant of Cloudflare’s Project Galileo. Through Project Galileo, they have access to our most advanced cybersecurity tools and support — freeing them to focus on their mission.
Shield 2: Safe technology
We agree with the Strategy’s push for Secure-by-Design and Secure-by-Default technology – these are in fact our core principles when developing our products and services in order to improve security for our end users automatically. We’ve taken this approach in deploying Web Application Firewall (WAF) protections for all of our users, such as the steps we took to protect our customers (including our free plan customers) against the log4j vulnerability, and in creating a machine-learning computed WAF attack score that enables customers to block likely attacks, even when they don’t match existing attack signatures.
This shield also notes both the opportunities and challenges brought by critical emerging technologies, such as quantum computing and artificial intelligence (AI). Cloudflare is getting ready for the quantum future – in order to protect against possible attacks from quantum computers, we believe that post-quantum cryptography tools should be readily available. In late 2022, we announced that by default, all websites and APIs served through Cloudflare, including those on our free plan, support post-quantum hybrid key agreement.
We also provide tools that help ensure that AI can be used securely. Given the incredible growth in this space, it’s critical that businesses can ensure that they are able to leverage AI innovation and growth — and doing so both securely and safely.
Shield 3: World-class threat sharing and blocking
We applaud the government’s efforts to strengthen threat sharing and threat blocking. For threat intelligence to be effective across sectors and industries, there needs to be a flow of information not only between government and industry, but also between industry peers. The support in the strategy for developing Information Sharing and Analysis Centers (ISACs) will help create a threat sharing culture within industry and support Australia to build a more mature cybersecurity ecosystem.
Cloudflare has supported ISACs to understand the impact of emerging vulnerabilities. One recent example concerned the HTTP/2 Rapid Reset Vulnerability, which resulted in record-breaking DDoS attacks. By working with our peers and sharing the latest insights we were able to help member organizations proactively protect themselves and their users.
Shield 4: Protected critical infrastructure
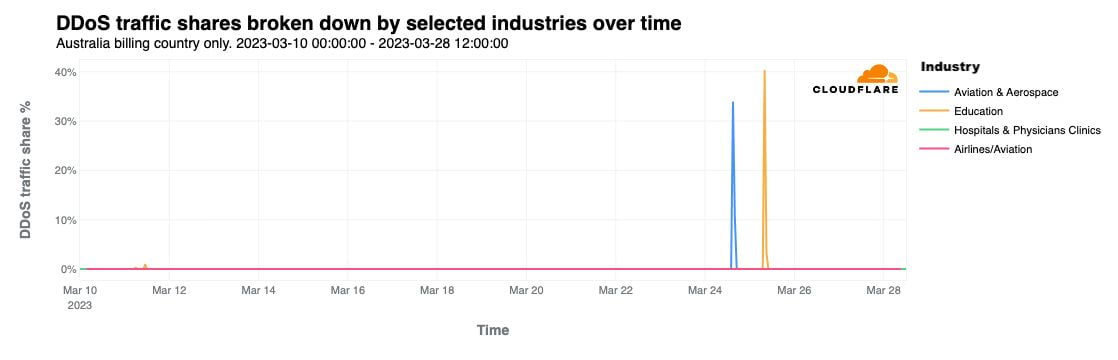
This shield focuses on critical infrastructure (CI) – those institutions vital to the nation’s functioning. Cloudflare understands the crucial importance of protecting CI: many of our customers are CI in their respective jurisdictions, including in Australia. Our tools help keep them, and those that rely on them, secure. For example, we mitigated threats to our customers when Anonymous Sudan and Killnet attacked and issued threats to Australian universities, airports, and hospitals in March 2023.
Equally concerning are the smaller critical infrastructure organizations that are the foundation of our communities: the neighborhood hospital, regional water treatment facility, and local energy provider that meet our basic needs like keeping the lights on and clean water running. Also vital, and noted in the Strategy – the small-yet-crucially-important companies that form the supply chains of our nationwide critical systems. These smaller organizations frequently lack the know-how and financial resources to deploy basic cyber security, let alone best-in-class cybersecurity tools and services. We felt that we could step up to help meet this crucial gap, so at the end of 2022, we launched Project Safekeeping in Australia and other global markets, providing no-cost and no-time limit Enterprise-level cybersecurity products for these critical entities.
Finally, we applaud the Strategy’s goal to strengthen the overall cyber posture of the Australian Commonwealth government, in particular by developing a Zero Trust culture. Zero Trust is generally considered a best practice in cybersecurity – the belief that organizations should not trust based on relationship to a perimeter (such as if someone is in the office), but instead must verify everything and everyone trying to connect to its systems before granting access. Zero Trust principles are being implemented successfully across the private sector and governments, and a Zero Trust strategy will certainly help uplift the security maturity and posture of Australia and its government.
Cloudflare is already providing our world-leading Zero Trust tools and services to government departments across Australia, both state and federal. For example, Australia’s National Disability Insurance Agency (NDIS) utilizes Cloudflare’s suite of security products to protect their environment and provide secure access into their application ecosystem.
Shield 5: Sovereign capabilities
This shield focuses on the essentials for having a diverse and professional cyber workforce in order to foster a vibrant Australian cyber ecosystem. Cloudflare also strives for a diverse workforce in order to have better business outcomes. To improve diversity across departments and roles, we rely on inclusive recruiting practices to help ensure a fair process, and we train employees on mitigating unconscious bias. In Australia, we actively foster diversity in cyber through internal associate programs designed to promote diverse groups into cyber engineering roles. We also run a series of external workshops and sessions aimed at the broader Australian women in cyber community, in order to foster greater learning and networking opportunities in this traditionally male-dominated sector.
Shield 6: Resilient region and global leadership
As a global company whose mission is to help build a better Internet, we believe it is vitally important for the international community to defend a free and open Internet. We were thrilled to see the Strategy acknowledge this as a key pillar of Australia’s cyber diplomacy. A free and open Internet is, in fact, both safer – as global knowledge is necessary to stop attacks that could come from anywhere in the world; and more resilient, as the Internet needs multiple global connection points to ensure that cyber attacks do not impact Internet access.
In addition, we fully agree with the Strategy that global technology markets should be competitive, reflecting a diverse pool of technology vendors. We strongly believe in the importance of having a vibrant security ecosystem, where different security providers can help mitigate the risk of services being compromised, helping to avoid security events.
Finally, this shield recognizes that international cyber standards must be harmonized. As a cybersecurity technology provider that adheres to multiple cybersecurity standards all around the world, we couldn’t agree more. Overlapping and redundant standards are a massive operational burden that do not equate to greater levels of security. However, onerous compliance regimes do prevent governments from having the best security technology available, given that many companies, particularly SMEs, simply can’t afford the high costs associated with numerous cybersecurity certifications.
We are thrilled to support Australia’s mission to be a world cyber leader by 2030. We look forward to our continued collaboration with the Australian government and industry in order to help ensure that everyone – from critical infrastructure, government, SMEs, nonprofits, to Australian citizens – can be more secure.