Post Syndicated from Elaine Dzuba original http://blog.cloudflare.com/2023-phishing-report/


After shutting down a ‘phishing-as-a-service’ operation that impacted thousands of victims in 43 countries, INTERPOL recently noted, “Cyberattacks such as phishing may be borderless and virtual in nature, but their impact on victims is real and devastating.” Business email compromise (BEC), a type of malware-less attack that tricks recipients into transferring funds — for example — has cost victims worldwide more than $50 billion, according to the FBI.
It is estimated that 90% of successful cyber attacks start with email phishing, which continues to be very lucrative for attackers. There is not much today that can be done to stop phishing attempts. However, to prevent successful attacks, it is important to understand (and proactively address) evolving phishing trends — including the ways attackers cleverly exploit intended victims’ trust in “known” email senders. To that end, this week Cloudflare published its first Phishing Threats Report.
This report explores key phishing trends and related recommendations, based on email security data from May 2022 to May 2023. During that time, Cloudflare processed approximately 13 billion emails, which included blocking approximately 250 million malicious messages from reaching customers’ inboxes. The report is also informed by a Cloudflare-commissioned survey of 316 security decision-makers across North America, EMEA, and APAC (you can download that separate study here).
Check out the full report to understand our three key takeaways:
- Attackers using deceptive links as the #1 phishing tactic — and how they are evolving how they get you to click and when they weaponize the link;
- Identity deception takes multiple forms (including business email compromise (BEC) and brand impersonation), and can easily bypass email authentication standards;
- Attackers pretend to be hundreds of different organizations, but they primarily impersonate the entities we trust and need to get work done.
Here are a few other things to keep in mind as you read the 2023 Phishing Threats report.
Email threat categorization
Attackers typically use a combination of social engineering and technical obfuscation techniques to make their messages seem legitimate. Therefore, Cloudflare uses a number of advanced detection techniques to analyze “fuzzy” signals (not just content that’s visible to the naked eye) to identify unwanted emails. Those signals include:
- Structural analysis of headers, body copy, images, links, attachments, payloads, and more, using heuristics and machine learning models specifically designed for phishing signals;
- Sentiment analysis to detect changes in patterns and behaviors (e.g., writing patterns and expressions);
- Trust graphs that evaluate partner social graphs, email sending history, and potential partner impersonations
Our email security service also incorporates threat intelligence from Cloudflare’s global network, which blocks an average of 140 billion cyber threats each day.
Those and many other signals lead to email dispositions of malicious, BEC, spoof, or spam; our dashboard tells customers the specific reasons (i.e., the threat indicator ‘categories’) for a particular email disposition.
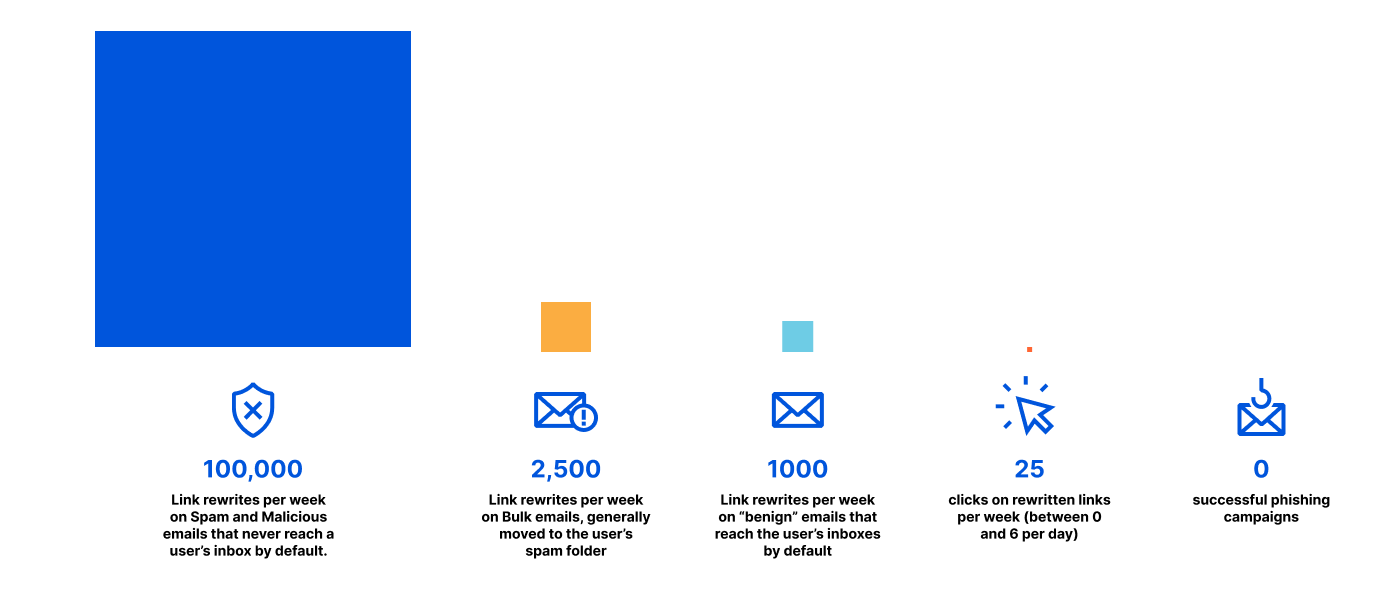
Below is a snapshot of the top email threat indicators we observed between May 2, 2022, to May 2, 2023. We categorize threat indicators into more than 30 different categories; over that period, the top threat indicators included deceptive links, domain age (newly registered domains), identity deception, credential harvesting, and brand impersonation.
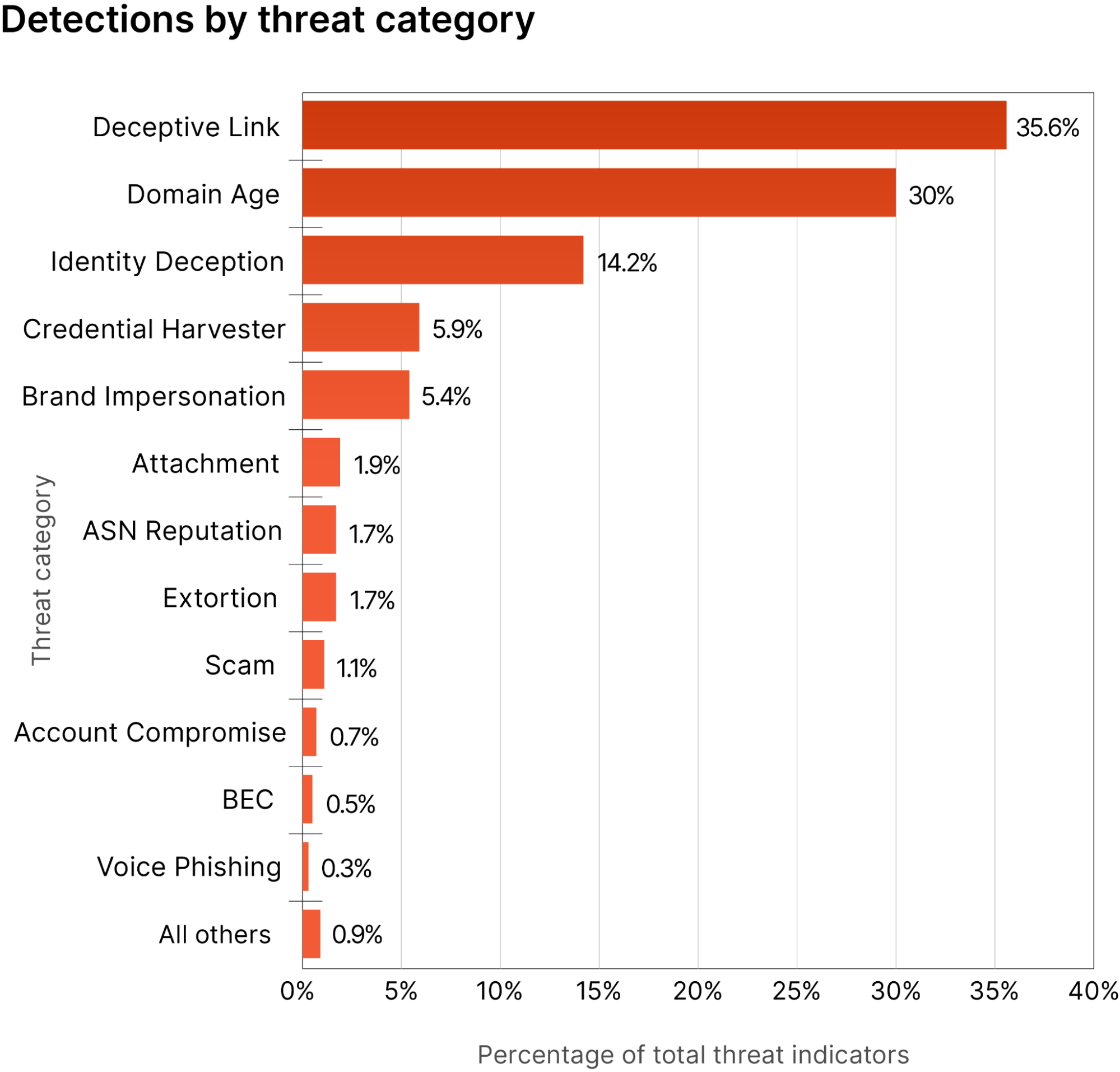
Below are brief descriptions of each of the top categories (detailed in more depth in the report’s appendix).
If clicked, a deceptive link will open the user’s default web browser and render the data referenced in the link, or open an application directly (e.g. a PDF). Since the display text for a link (i.e., hypertext) in HTML can be arbitrarily set, attackers can make a URL appear as if it links to a benign site when, in fact, it is actually malicious.
Domain age is related to domain reputation, which is the overall score assigned to a domain. For example, domains that send out numerous new emails immediately after domain registration will tend to have a poorer reputation, and thus a lower score.
Identity deception occurs when an attacker or someone with malicious intent sends an email claiming to be someone else. The mechanisms and tactics of this vary widely. Some tactics include registering domains that look similar (aka domain impersonation), are spoofed, or use display name tricks to appear to be sourced from a trusted domain. Other variations include sending email using domain fronting and high-reputation web services platforms.
Credential harvesters are set up by an attacker to deceive users into providing their login credentials. Unwitting users may enter their credentials, ultimately providing attackers with access to their accounts.
Brand impersonation is a form of identity deception where an attacker sends a phishing message that impersonates a recognizable company or brand. Brand impersonation is conducted using a wide range of techniques.
An attachment to an email that, when opened or executed in the context of an attack, includes a call-to-action (e.g. lures target to click a link) or performs a series of actions set by an attacker.
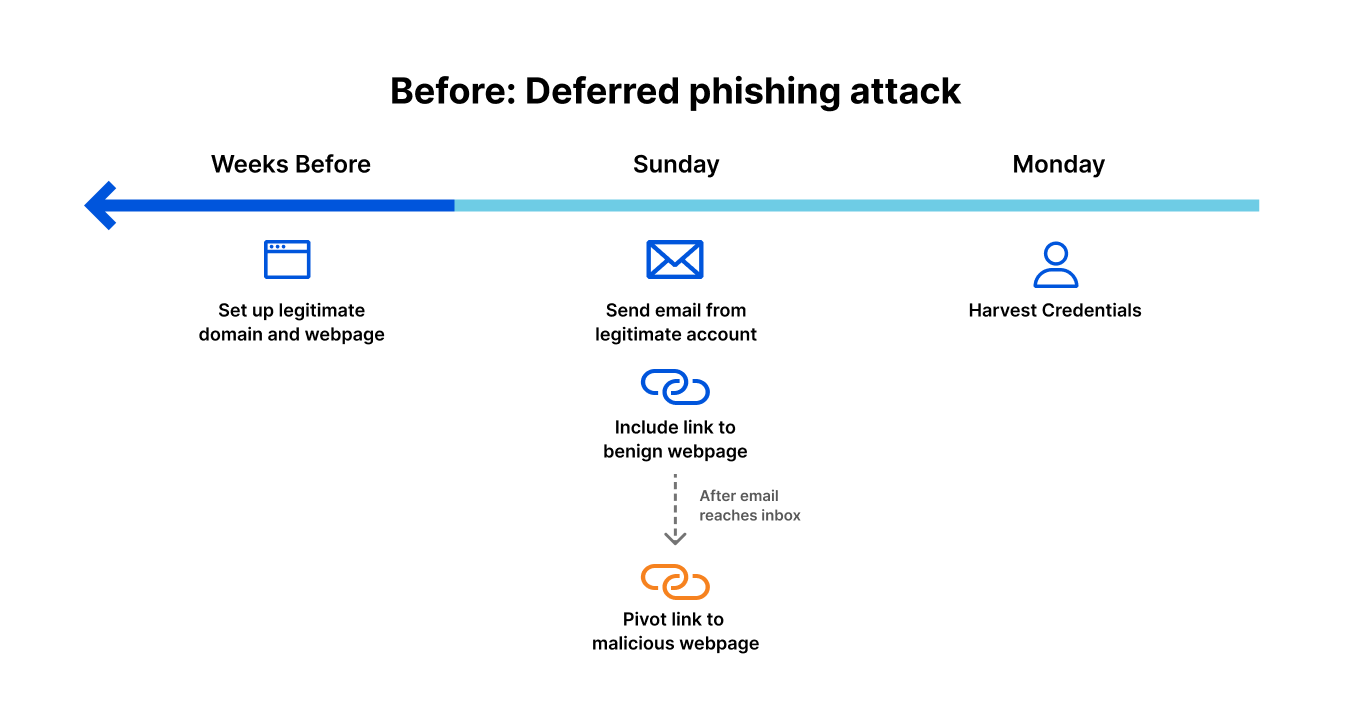
Cloudflare regularly observes multiple threat indicators in one phishing email. For example, one Silicon Valley Bank-themed phishing campaign (detailed in this March 2023 blog) combined brand impersonation with a deceptive link and malicious attachment.
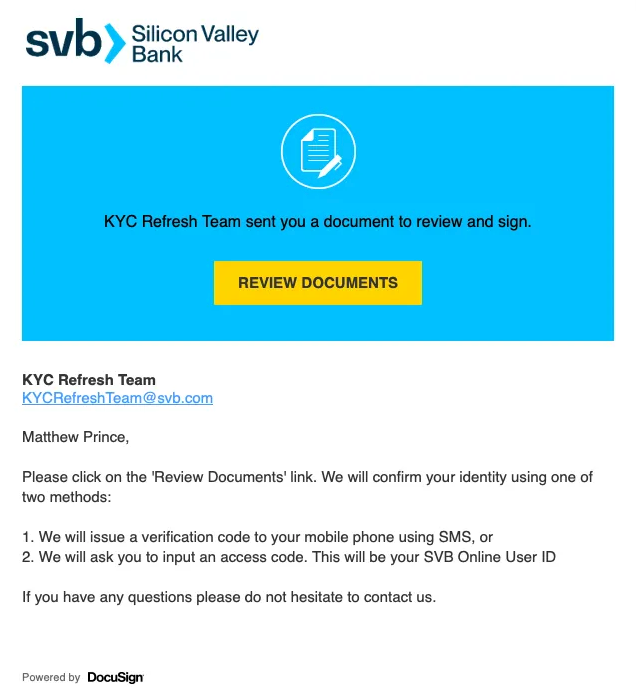
The attackers leveraged the SVB brand in a DocuSign-themed template. The email included HTML code that contains an initial link and a complex redirect chain that is four deep. The included HTML file in the attack would have sent the recipient to a WordPress instance that has recursive redirection capability.
(Speaking of links, deceptive links were the #1 threat category, appearing in 35.6% of our detections. And attackers aren’t just using links in email channels; the rise of multi-channel phishing threats — which exploit other applications such as SMS/text, chat, and social media — are also covered in the report).
Trusted (and most impersonated) brands
Silicon Valley Bank was just one of approximately 1,000 different brands we observed being impersonated in emails targeting Cloudflare customers between May 2022 and May 2023. (Cloudflare employees were directly targeted via brand impersonation in the “Oktapus” phishing attack that the Cloudflare One suite of products thwarted in July 2022).
However, as detailed in the Phishing Threats Report, we observed that email attackers most often (51.7% of the time) impersonated one of 20 well-known global brands, with Microsoft being #1 on their list.
| Rank | Impersonated brand |
|---|---|
| 1 | Microsoft |
| 2 | World Health Organization |
| 3 | |
| 4 | SpaceX |
| 5 | Salesforce |
| 6 | Apple |
| 7 | Amazon |
| 8 | T-Mobile |
| 9 | YouTube |
| 10 | MasterCard |
| 11 | Notion.so |
| 12 | Comcast |
| 13 | Line Pay |
| 14 | MasterClass |
| 15 | Box |
| 16 | Truist Financial Corp |
| 17 | |
| 18 | |
| 19 | AT&T |
| 20 | Louis Vuitton |
Example of a Microsoft credential harvesting attempt
Earlier this year, Cloudflare detected and blocked a phishing campaign leveraging the Microsoft brand in an attempt to harvest credentials through a legitimate — but compromised — site.
In the email example below, there is no text in the body of the email despite its appearance. The entire body is a hyperlinked JPEG image. Thus, if the recipient clicks anywhere in the body (even if they don’t intend to click the link), they are effectively clicking the link.
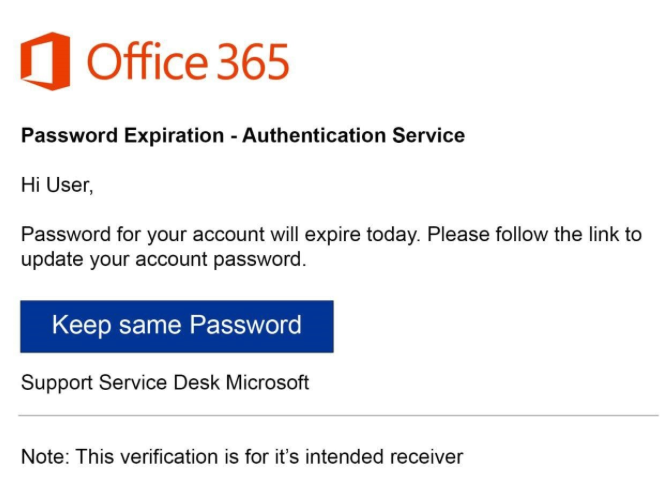
Initially, the hyperlink for this image appears to be a benign Baidu URL – hxxp://www.baidu[.]com/link?url=-yee3T9X9U41UHUa3VV6lx1j5eX2EoI6XpZqfDgDcf-2NYQ8RVpOn5OYkDTuk8Wg#<recipient’s email address base64 encoded>. However, if this link is clicked, the target’s browser would be redirected to a site that had been compromised and used to host a credential harvester.
The attacker used Microsoft Office 365 branding, but attempted to circumvent any brand detection techniques by including the brand information within the image (i.e., there was no plaintext or HTML text that could be inspected to identify the brand).
However, using optical character recognition (OCR), Cloudflare successfully identified “Office 365” and “Microsoft” in the image. Using OCR, we also identified the use of suspicious account lures related to passwords.
In this example, attackers’ techniques included:
- Inclusion of only a JPEG image (impossible to detect words without OCR)
- Embedding a hyperlink in that image (clicking anywhere in the body would result in clicking the link)
- Hyperlinking to a Baidu URL (used to bypass reputation-based URL detection techniques)
- The Baidu URL redirecting the recipient’s browser to a credential harvesting site (i.e., would circumvent other email security defenses that are not capable of deep link inspection)
- Hosting the credential harvester on a legitimate site that had been compromised by the attacker (even with deep link inspection, will again attempt to bypass URL detection techniques based on reputation)
This attack vector leverages the high reputation and authenticity of Baidu to bypass the reputation of the true host/IP where the credential harvester is hosted.
While this specific campaign focused on harvesting Microsoft credentials, we often see attackers using similar methods to bypass brand detection techniques and trick victims into downloading malware and other malicious payloads.
URL redirection techniques are often seen in phishing campaigns, but threat actors are continuing to refine their approach by abusing more and more legitimate domains like baidu.com, bing.com, goo.gl, etc. Our numerous detection capabilities allow us to conduct deep link inspection of URLs using redirection techniques of all kinds, including those that abuse legitimate domains.
What about SPF, DKIM, and DMARC?
Email authentication (specifically the SPF, DKIM, and DMARC standards) are often mentioned as useful against brand impersonation: these standards help validate server and tenant origins, protect message integrity, provide policy enforcement, and more.
However, attackers can still find ways to bypass authentication to trick email suites; and we actually observed that 89% of unwanted messages “passed” SPF, DKIM, and/or DMARC checks.
Some limitations of email authentication include:
| SPF (Sender Policy Framework) |
Key benefits: Validating server origin (i.e., validates where a message originates from) Defining which email servers and services are allowed to send messages on a domain owner’s behalf |
|---|---|
| Limitations: Does not prevent lookalike email, domain, or display name spoofing Does not validate the “From” header; uses envelope “From” to determine sending domain Validation ineffective when emails are forwarded or when messages sent to a mailing list are sent to each subscriber SPF evaluation process can be limited to a certain number of DNS lookups Does not protect against attacks using “validated” emails with embedded URLs, malicious payloads, or attachments |
|
| DKIM (Domain Keys Identified Mail) |
Key benefits: Providing tenant origin validation (i.e., checks that an email was sent/authorized by the owner of the domain via a digital signature) Ensuring email is not altered while transferred from server to server; protecting message integrity |
| Limitations: Does not prevent lookalike email, domain, or display name spoofing Does not protect against replay attacks (DKIM only signs specific parts of a message. Attackers can add other header fields to emails passing DKIM then forward them.) Does not protect against attacks using “validated” emails with embedded URLs, malicious payloads or attachments |
|
| DMARC (Domain-based Message Authentication, Reporting and Conformance) | Key benefits: Providing policy enforcement and reporting for SPF and DKIM Stipulating what policy to follow if an email doesn’t pass SPF or DKIM authentication (e.g. reject/delete, quarantine, no policy/send) Reporting function allows domain owners to see who is sending email on their behalf (i.e., protecting against spoofing of your own domain and brand abuse) |
| Limitations: Does not prevent spoofing of another brand’s domain Does not prevent lookalike email, domain, or display name spoofing Domain owners specify what percentage of mail DMARC policies it applies to; application percentages of less than 100% are less effective Does not protect against attacks using “validated” emails with embedded URLs, malicious payloads or attachments |
Conclusions
Attackers are constantly evolving their tactics. Multiple protection layers must be enacted before, during, and after messages reach the inbox. Cloudflare never inherently “trusts” any type of email communication (whether it appears to be internal, external, or from a ‘known’ business partner).
Likewise, we recommend that — first and foremost — all organizations extend the Zero Trust security model of “never trust, always verify” not just to the network and applications, but also to the email inbox.
In addition to securing email with a Zero Trust approach, we also recommend:
- Augmenting cloud email with multiple anti-phishing controls. As noted in this Forrester blog from June, “The use of messaging, collaboration, file sharing, and enterprise software-as-a-service applications across multiple devices all contribute to employee productivity and experience. Many of these environments are considered ‘closed,’ but one successful phish of a supply chain partner’s credentials opens your organization up to data loss, credential theft, fraud, and ransomware attacks. Protections developed for the email inbox must extend to these environments and throughout the day-to-day workflows of your employees.”
- Adopting phishing-resistant multifactor authentication (MFA). While not all MFA provides the same layer of security, hardware security keys are among the most secure authentication methods for preventing successful phishing attacks. They can protect networks even if attackers gain access to usernames and passwords.
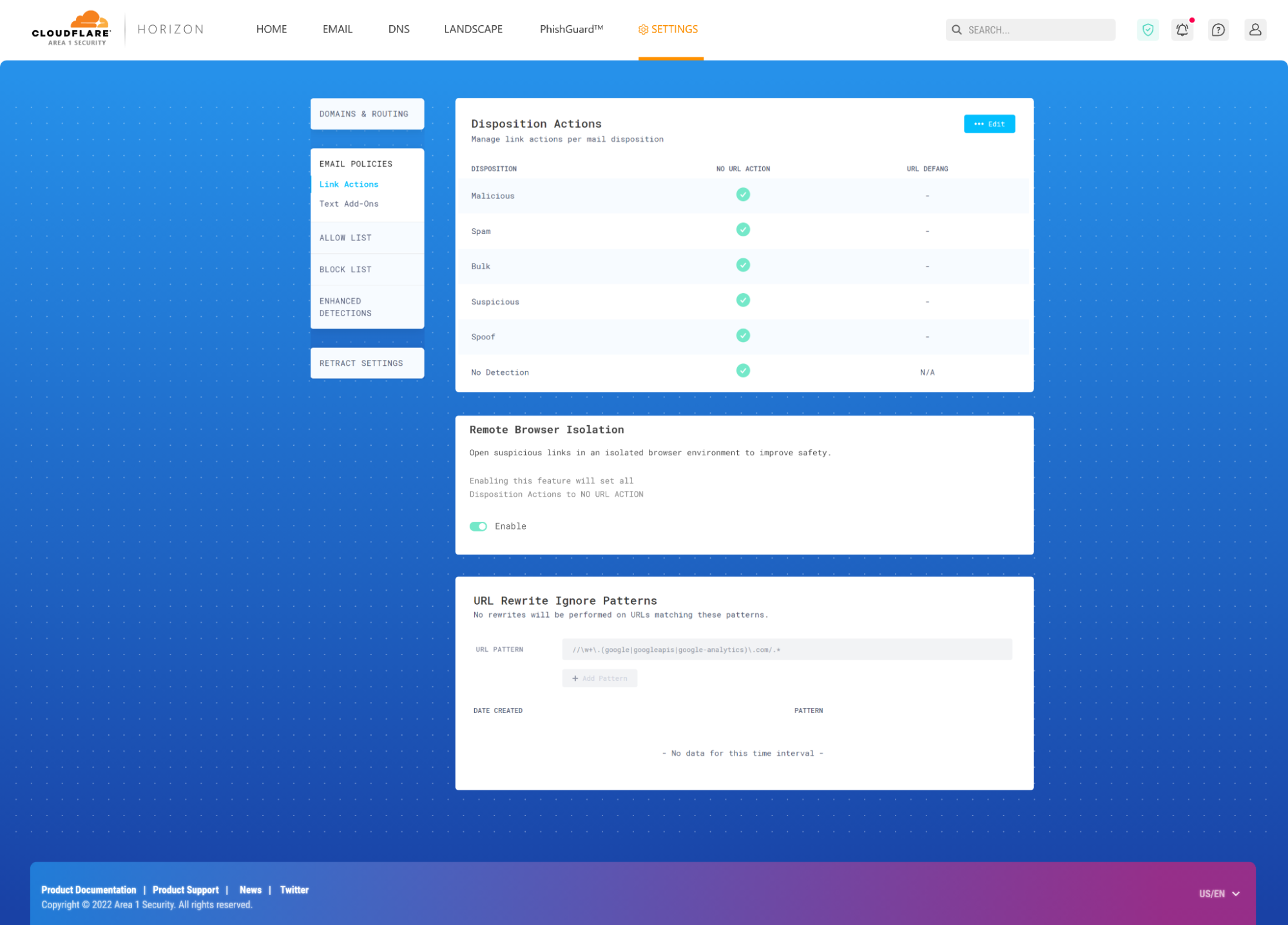
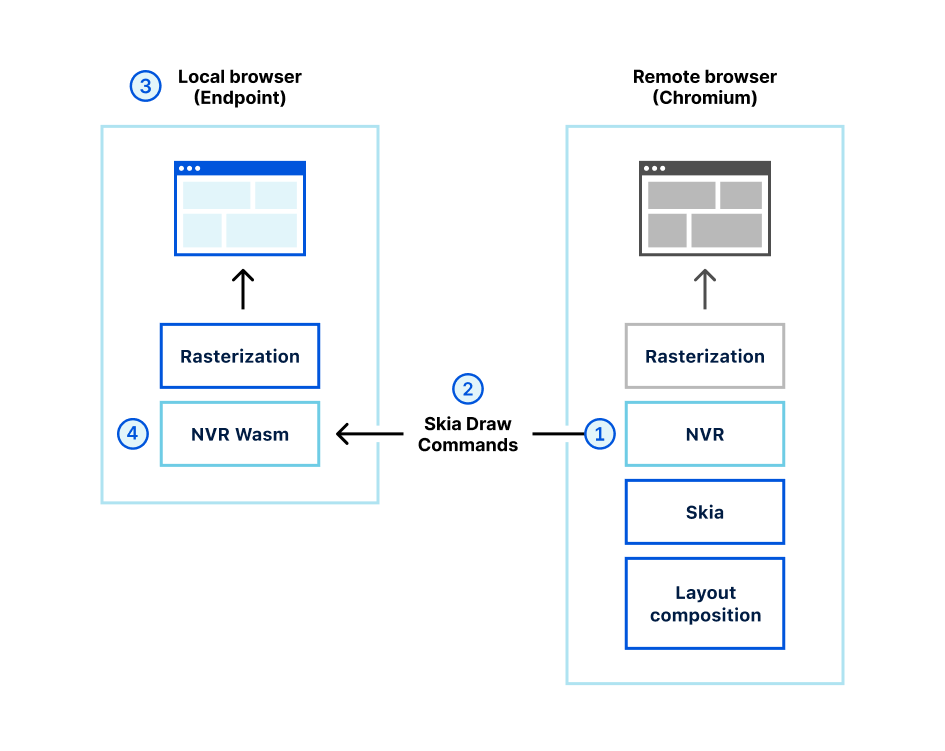
- Make it harder for humans to make mistakes. Meet employees and teams where they are by making the tools they already use more secure, and preventing them from making mistakes. For example, remote browser isolation (RBI) technology, when integrated with cloud email security, can automatically isolate suspicious email links to prevent users from being exposed to potentially malicious web content. Keyboard inputs can also be disabled on untrusted websites, protecting users from accidentally entering sensitive information within a form fill or credential harvesting. This provides a layer of defense against multi-channel phishing attacks by effectively allowing users to safely open links without disrupting their workflow.
If you’re interested in the full findings, you can download the 2023 Phishing Threats Report here, as well as our recommendations for preventing successful phishing attacks. And if you’d like to see Cloudflare’s email security in action, you can request a free phishing risk assessment here.