Post Syndicated from The History Guy: History Deserves to Be Remembered original https://www.youtube.com/watch?v=k4qpQ6zwyhs
Amazon Has Trucks Filled with Hard Drives and an Armed Guard
Post Syndicated from Bruce Schneier original https://www.schneier.com/blog/archives/2021/01/amazon-has-trucks-filled-with-hard-drives-and-an-armed-guard.html
From an interview with an Amazon Web Services security engineer:
So when you use AWS, part of what you’re paying for is security.
Right; it’s part of what we sell. Let’s say a prospective customer comes to AWS. They say, “I like pay-as-you-go pricing. Tell me more about that.” We say, “Okay, here’s how much you can use at peak capacity. Here are the savings we can see in your case.”
Then the company says, “How do I know that I’m secure on AWS?” And this is where the heat turns up. This is where we get them. We say, “Well, let’s take a look at what you’re doing right now and see if we can offer a comparable level of security.” So they tell us about the setup of their data centers.
We say, “Oh my! It seems like we have level five security and your data center has level three security. Are you really comfortable staying where you are?” The customer figures, not only am I going to save money by going with AWS, I also just became aware that I’m not nearly as secure as I thought.
Plus, we make it easy to migrate and difficult to leave. If you have a ton of data in your data center and you want to move it to AWS but you don’t want to send it over the internet, we’ll send an eighteen-wheeler to you filled with hard drives, plug it into your data center with a fiber optic cable, and then drive it across the country to us after loading it up with your data.
What? How do you do that?
We have a product called Snowmobile. It’s a gas-guzzling truck. There are no public pictures of the inside, but it’s pretty cool. It’s like a modular datacenter on wheels. And customers rightly expect that if they load a truck with all their data, they want security for that truck. So there’s an armed guard in it at all times.
It’s a pretty easy sell. If a customer looks at that option, they say, yeah, of course I want the giant truck and the guy with a gun to move my data, not some crappy system that I develop on my own.
Lots more about how AWS views security, and Keith Alexander’s position on Amazon’s board of directors, in the interview.
Found on Slashdot.
Raspberry Pi ‘Swear Bear’ keeps your potty mouth in check
Post Syndicated from Ashley Whittaker original https://www.raspberrypi.org/blog/raspberry-pi-swear-bear-keeps-your-potty-mouth-in-check/
Why use a regular swear jar to retrain your potty-mouthed brain when you can build a Swear Bear to help you instead?
Swear Bear listens to you. All the time. And Swear Bear can tell when a swear word is used. Swear Bear tells you off and saves all the swear words you said to the cloud to shame you. Swear Bear subscribes to the school of tough love.
Artificial intelligence
The Google AIY kit allows you to build your own natural language recogniser. This page shows you how to assemble the Voice HAT from the kit, and it also includes the code you’ll need to make your project capable of speech-to-text AI.
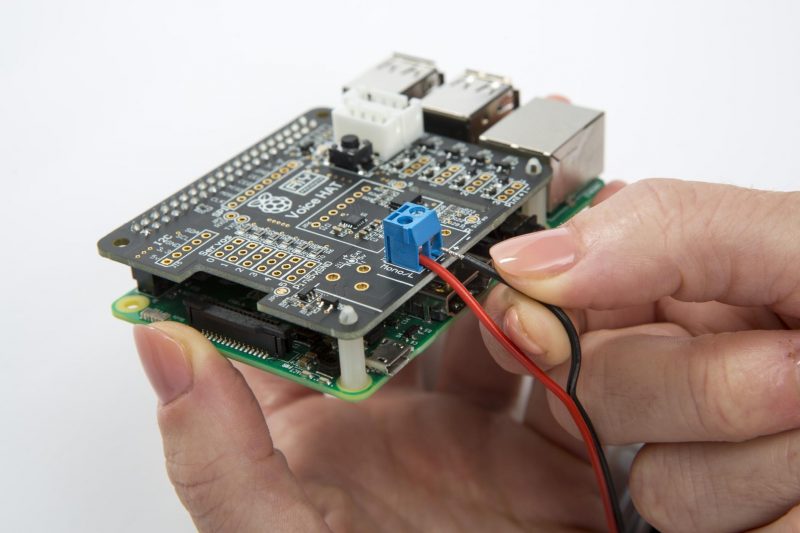
To teach Swear Bear the art of profanity detection, Swear Bear creators 8 Bits and a Byte turned to the profanity check Python library. You can find the info to install and use the library on this page, as well as info on how it works and why it’s so accurate.
You’ll hear at this point in the video that Swear Bear says “Oh dear” when a swear word is used within earshot.
Hardware
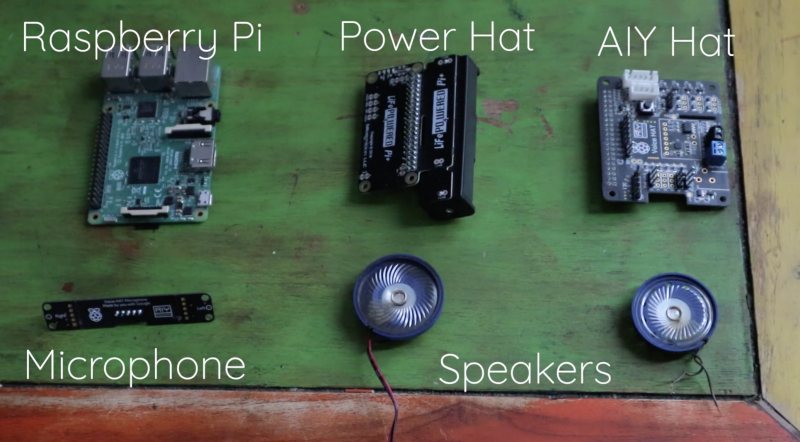
This project uses the the first version of Google’s AIY Voice Kit, which comes with a larger black AIY Voice HAT and is compatible with Raspberry Pi 3 Model B. The kit also includes a little Voice HAT microphone board.
Version 2 of the kit comprises the smaller Raspberry Pi Zero WH and a slimmer ‘Voice Bonnet’.
The microphone allows Swear Bear to ‘hear’ your speech, and through its speakers it can then tell you off for swearing.

All of hardware is squeezed into the stuffing-free bear once the text-to-speech and profanity detection software is working.
Babbage Bear hack?

8 Bits and a Byte fan Ben Scarboro took to the comments on YouTube to suggest they rework one of our Babbage Bears into a Swear Bear. Babbage is teeny tiny, so maybe you would need to fashion a giant version to accomplish this. Just don’t make us watch while you pull out its stuffing.
The post Raspberry Pi ‘Swear Bear’ keeps your potty mouth in check appeared first on Raspberry Pi.
Comic for 2021.01.04
Post Syndicated from Explosm.net original http://explosm.net/comics/5759/
New Cyanide and Happiness Comic
Depth and Breadth
Post Syndicated from original https://xkcd.com/2407/
Conversations on Mindful Leadership from the Front Lines | Talks at Google
Post Syndicated from Talks at Google original https://www.youtube.com/watch?v=pXUyI-6AWu4
Model Posing Guide – Pre-Order Sale
Post Syndicated from Matt Granger original https://www.youtube.com/watch?v=nYhlIlxJ0qY
Нова година, нов късмет
Post Syndicated from original https://bivol.bg/ng-nm.html

– Ало, шефе, за много години! Да си здрав като мене и да имаме още дълги години все така ползотворно сътрудничество! – Казал съм ти да не ми звъниш. Когато…
Comic for 2021.01.03
Post Syndicated from Explosm.net original http://explosm.net/comics/5758/
New Cyanide and Happiness Comic
Portrait Posing
Post Syndicated from Matt Granger original https://www.youtube.com/watch?v=STACPhdIxxg
2021-01-02 равносметъчно
Post Syndicated from original https://vasil.ludost.net/blog/?p=3444
За да докарам поне един post тая година (щото не е ясно дали ще намеря време за повече), ето една равносметка за миналата година:
– Оживяхме, и не карахме вируса;
– Малките зверове растат усилено и правят всякакви интересни и опасни открития;
– Жена ми още не ме е убила;
– Успяхме да случим FOSDEM преди големите заразявания и затваряния;
– За да успявам да работя и да съм около семейството, правихме всякакви странни неща – работа от вкъщи, от Бургас, пътувах си с цялата техника и т.н.. Много се разглезих с квадратния монитор и хубавата клавиатура, та пренасянията ми не са толкова прости 🙂 ;
– На практика цялото лято го изкарах в Бургас, ДОРИ ме заведоха няколко пъти на плаж (и спокойно мога да кажа, че все още не ми харесва) (и ми напомниха да спомена, че не съм си свалил кубинките на плажа);
– Годината като цяло показа, че работата от вкъщи поне за мен се получава. Допълнителен плюс е, че мога да си ползвам шумната Model M клавиатура без целия офис да иска да ме удуши (освен когато забравя да си mute-на микрофона);
– “Кривото” на ъгъла на “Дондуков” и “Будапеща” го закриха още преди пандемията, но ние пренесохме ИББ online на b.1h.cx (една BBB инстанция на машина на Мариян). Малко се промениха посетителите, но пък така успяваме да се видим с доста хора от други времеви зони и други места, та май си е плюс;
– От време на време успявах да се наспя, повечето време – не;
– Случи се OpenFest, online, в общи линии без мое участие. Супер горд съм с екипа 🙂
Селекция “офисни” снимки:
– Вкъщи 1;
– Бургас 1;
– Бургас в полеви условия;
– Вкъщи 2;
– Бургас 2;
За новата година… Очаквам да не е по-зле от изминалата, или поне се надявам 🙂 Определено чакам с нетърпение да видя колко карантинни бебета ще се появят.
И ето ни една обща снимка.
HaXmas Hardware Hacking
Post Syndicated from Tod Beardsley original https://blog.rapid7.com/2021/01/02/haxmas-hardware-hacking/

Usually, when you read an IoT hacking report or blog post, it ends with something along the lines of, “and that’s how I got root,” or “and there was a secret backdoor credential,” or “and every device in the field uses the same S3 bucket with no authentication.” You know, something bad, and the whole reason for publishing the research in the first place. While such research is of course interesting, important, and worth publishing, we pretty much never hear about the other outcome: the IoT hacking projects that didn’t uncover something awful, but instead ended up with, “and everything looked pretty much okay.”
So, this HaXmas, I decided to dig around a little in Rapid7’s library of IoT investigations that never really went anywhere, just to see which tools were used. The rest of this blog post is basically a book report of the tooling used in a recent engagement performed by our own Jonathan Stines, and can be used as a starting point if you’re interested in getting into some casual IoT hacking yourself. Even though this particular engagement didn’t go anywhere, I had a really good time reading along with Stines’ investigation on a smart doorbell camera.
Burp Suite
While Burp Suite might be a familiar mainstay for web app hackers, it has a pretty critical role in IoT investigations as well. The “I” in IoT is what makes these Things interesting, so checking out what and how those gadgets are chatting on the internet is pretty critical in figuring out the security posture of those devices. Burp Suite lets investigators capture, inspect, and replay conversations in a proxied context, and the community edition is a great way to get started with this kind of manual, dynamic analysis.
Frida
While Burp is great, if the IoT mobile app you’re looking at (rightly) uses certificate pinning in order to secure communications, you won’t get very far with its proxy capabilities. In order to deal with this, you’ll need some mechanism to bypass the application’s pinned cert, and that mechanism is Frida. While Frida might be daunting for the casual IoT hacker, there’s a great HOWTO by Vedant that provides some verbose instructions for setting up Frida, adb, and Burp Suite in order to inject a custom SSL certificate and bypass that pesky pinning. Personally, I had never heard of Frida or how to use it for this sort of thing, so it looks like I’m one of today’s lucky 10,000.
Binwalk
When mucking about with firmware (the packaged operating system and applications that makes IoT devices go), Binwalk from Refirm Labs is the standard for exploring those embedded filesystems. In nearly all cases, a “check for updates” button on a newly opened device will trigger some kind of firmware download—IoT devices nearly always update themselves by downloading and installing an entirely new firmware—so if you can capture that traffic with something like Wireshark (now that you’ve set up your proxied environment), you can extract those firmware updates and explore them with Binwalk.
Allsocket eMMC153 chip reader
Now, with the software above, you will go far in figuring out how an IoT device does its thing, but the actual hands-on-hardware experience in IoT hacking is kinda the fun part that differentiates it from regular old web app testing. So for this, you will want to get your hands on a chip reader for your desoldered components. Pictured below is an Allsocket device that can be used to read both 153-pin and 169-pin configurations of eMMC storage, both of which are very common formats for solid-state flash memory in IoT-land. Depending on where you get it, they can run about $130, so not cheap, but also not bank-breaking.
Thanks!
Thanks again to Jonathan Stines, who did all the work that led to this post. If you need some validation of your IoT product, consider hiring him for your next IoT engagement. Rapid7’s IoT assessment experts are all charming humans who are pretty great at not just IoT hacking, but explaining what they did and how they did it. And, if you like this kind of thing, drop a comment below and let me know—I’m always happy to learn and share something new (to me) when it comes to hardware hacking.
More HaXmas blogs
- Help Others Be “Cyber Aware” This Festive Season—And All Year Round!
- UPnP With a Holiday Cheer
- Metasploit Tips and Tricks for HaXmas 2020
- Top Security Recommendations for 2021
- Rapid7 Labs’ 2020 Naughty List Summary Report to Santa
- Taking Inspiration from Our Security Nation in an Otherwise Uninspiring Year
- Metasploit 2020 Wrap-Up
- Predicting the Unpredictable: What Will the Cybersecurity Space Look Like in 2021?
Predicting the Unpredictable: What Will the Cybersecurity Space Look Like in 2021?
Post Syndicated from Bri Hand original https://blog.rapid7.com/2021/01/02/predicting-the-unpredictable-what-will-the-cybersecurity-space-look-like-in-2021/

Not to start off another blog post about how insane this year has been, but let’s just take a moment to appreciate HOW INSANE THIS YEAR HAS BEEN. As I sat down to write this blog post, I took a look at last year’s predictions post and was amused (and slightly depressed?) to see how little we knew about what was coming. And while predicting anything these days seems just slightly impossible, we gathered our in-house experts, customers, and industry leaders to take their best bets on what the security sphere will offer up in 2021. Check out their thoughts below!
Reserve Your 2021 Cybersecurity History Calendar
Babak Mirzahosseiny, Head of Cyber Security at Greenstone Financial Services
There will be more remote work for sure, as many companies realized they can survive with that, and with the financial pressure on the majority of businesses, they may decide to save some money by reducing the office size and letting people work from home. This means there will be more threats targeting remote workers, and it won’t be surprising if they get more sophisticated, too. Ransomware would continue being on top of the list, but attackers may add more nasty actions to it as well. On the other side, threat intelligence will grow and start playing a more serious role in our day-to-day life.
Tod Beardsley, Director of Research at Rapid7
Okay, I have two predictions. One is pretty pedestrian and short term, one is a little more exotic and has longer-term consequences.
First, I believe that 2021 will be defined by the scams, spam, and phishing centered around COVID-19 vaccines and their availability. Online criminals are well-practiced at capitalizing on natural disasters, and SARS-CoV-2 is the most significant natural disaster of the last 100 years. On top of this, state-backed disinformation and misinformation operations will similarly run wild with COVID-19. I expect to see a million and one campaigns promoting dodgy sources for COVID-19 vaccines and therapeutics, similar to the pharmaceutical spam trade that we see today, as well as campaigns warning against the same. Vaccines for this pandemic are a commodity that have huge demand, limited supply, a nationalistic character, and a nonzero level of suspicion and distrust.
Second, planet Earth now has a critical amount of compute cycles (both traditional and quantum), data creation and ingestion, and bandwidth across long and short distances (fiber and 5G). Because of this, I believe that we will see an emergent artificial intelligence arise from the internet. Further, I expect this superintelligence will have its own, internal subjective set of experiences and ethical framework. It will be unlike anything we’ve ever seen on this planet, namely because this self-ware entity will not be bound by the limitations of a chemical/electric substrate that we see in biological lifeforms. Thanks to a silicon/electronic substrate, it will appear to plan, decide, and act in its own interests extremely quickly, and any attempt to contain it after the fact will be laughably inadequate. I do think we have some chance to coexist with this entity for at least the short term, since it will incidentally be hyper-civilized and unlikely to be needlessly cruel, but we should be preparing ourselves now for this inevitability.
Chad Kliewer, Information Security Officer at Pioneer Telephone Cooperative, Inc.
With everything 2020 threw at us, the human element still comes out as the biggest security threat, but probably not in the way you are thinking. Technical controls will continue to improve, which will force the bad guys and gals to use more social-engineering tactics. As more and more businesses move away from traditional data centers to the cloud, behavior analytics will continue to evolve and play a very important role in identifying compromised credentials. As security professionals, we will need to ensure our co-workers, technical and nontechnical alike, stay aware of the current threats and don’t accidentally give our adversaries a foothold in our socially distanced workplace.
Deral Heiland, IoT Research Lead at Rapid7
With the continued expansion of IoT sensor and actuator technologies that leverage cellular communication, it is highly probable we will start to see new classes of exploits and attacks against cellular-based edge devices, which will have a dramatic impact on critical infrastructure security in 2021.
Kirk Lewis, Information Security Administrator at AmeriBen
I predict an increase in cyberattacks and ransomware, more consolidation within security companies, and more integrations, among others.
Josh Petrucka, Security Analyst at Conexus Credit Union
With more integration on cloud services, we will be focusing on cloud security and CASB. From a threat perspective, I believe the industry will see new ransomware tactics and malware.
Bob Rudis, Chief Data Scientist at Rapid7
Bitcoin is climbing—albeit, erratically—back to its high point back at the cusp of 2018, and neither local municipalities, school districts, healthcare providers, nor many other industries have learned the lessons from 24 months of nigh-continuous ransomware assaults. As such, we can be fairly certain ransomware tactics and techniques will continue to be commoditized and industrialized, and criminals will continue to exploit organizations that are strapped for resources and distracted by attempting to survive in these chaotic times.
2021 will also see a dramatic increase in cure-related phishing attacks as we all desperately hope for a true end to this current global malady. However, as 25% of us are still working sheltered in-place, we can expect to see even more vulnerabilities discovered in remote access technologies with more exploit campaigns taking advantage of them.
Rick Heil, IT Director / InfoSec Officer at MERGE
I think 2021 will bring more social engineering and more scams. As people are looking to digital methods to connect with friends and family, it is inevitable that scammers will take advantage of the shift with their pitches.
Jen Ellis, Vice President of Community and Public Affairs at Rapid7
The United States is firmly in a new era of political discourse in which cyber-espionage, sabotage, and disinformation have a growing impact. This will certainly not end with the 2020 election. Many attacks are seemingly designed to undermine confidence in American societal cohesion and democratic processes, rather than change the outcome of a single election cycle. As a result, the need for strong cybersecurity practices is increasing for lesser-known organizations that affect politics on a more local level, extending well beyond national campaigns, government agencies, or traditional targets of for-profit attacks. How media outlets and social networks report on and disseminate hacked material and cyber-attacks (such as not rushing to attribution and declining to act as a force multiplier for attackers) will also continue taking on growing importance. While these patterns started before 2021, we should expect them from day one in 2021 through the year. Please prepare accordingly.
Galal Nabil, Security Specialist at Fresh Electric for Home Appliances
I think the growth of cybercrimes will increase year by year.
Erick Galinkin, Principal Artificial Intelligence Research at Rapid7
In 2021, the interplay between AI and cybersecurity will be increasingly apparent—security vendors are spending more time and money than ever on specialists in artificial intelligence and data science to mine their data and enhance their products using AI and machine learning. Additionally, development on artificial intelligences for aggregating and correlating security data is rapidly improving. A variety of security companies and researchers are deeply invested not only in using data science generally to build use cases within their products, but also in using natural language processing and other machine learning technologies to improve the ability of their existing products to ingest and integrate information from additional sources.
It’s your turn!
We’d love to know what you’re expecting to see in the coming year, so hit us up on Twitter (@Rapid7) using the hashtag #Rapid7Predicts to share your own predictions. Also, if you’re interested in seeing how our predictions have stacked up in past years, check out our previously published New Years prediction blogs here:
More HaXmas blogs
- Help Others Be “Cyber Aware” This Festive Season—And All Year Round!
- UPnP With a Holiday Cheer
- Metasploit Tips and Tricks for HaXmas 2020
- Top Security Recommendations for 2021
- Rapid7 Labs’ 2020 Naughty List Summary Report to Santa
- Taking Inspiration from Our Security Nation in an Otherwise Uninspiring Year
- Metasploit 2020 Wrap-Up
- HaXmas Hardware Hacking
Portrait POSING – Live
Post Syndicated from Matt Granger original https://www.youtube.com/watch?v=v_5ktMaFLP0
Densha de Go! Plug & Play TV Game Train Simulator – A surprisingly capable dedicated console
Post Syndicated from Techmoan original https://www.youtube.com/watch?v=Do-ZBPWhhbQ
Comic for 2021.01.02
Post Syndicated from Explosm.net original http://explosm.net/comics/5757/
New Cyanide and Happiness Comic
My New Camera Kit!
Post Syndicated from Matt Granger original https://www.youtube.com/watch?v=n_9NIHXwfWA
Friday Squid Blogging: Linguine allo Scoglio Recipe
Post Syndicated from Bruce Schneier original https://www.schneier.com/blog/archives/2021/01/friday-squid-blogging-linguine-allo-scoglio-recipe.html
Delicious seafood pasta dish — includes squid — from America’s Test Kitchen.
As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered.
Read my blog posting guidelines here.
Bottomley: Deploying Encrypted Images for Confidential Computing
Post Syndicated from original https://lwn.net/Articles/841549/rss
James Bottomley has posted a
detailed description of what it takes to get an encrypted image running
securely with AMD’s SEV mechanism. “In this post I’ll discuss how
you actually bring up a confidential VM from an encrypted image while
preserving secrecy. However, first a warning: This post represents the
state of the art and includes patches that are certainly not deployed in
distributions and may not even be upstream, so if you want to follow along
at home you’ll need to patch things like qemu, grub and OVMF.”
Tegan and Sara | High School with Tegan and Sara | Talks at Google
Post Syndicated from Talks at Google original https://www.youtube.com/watch?v=ZPC-KFzxIMA