Post Syndicated from Azmina Hashim original https://blog.cloudflare.com/how-cloudflare-helps-protect-small-businesses/


Large-scale cyber attacks on enterprises and governments make the headlines, but the impacts of cyberattacks can be felt acutely by small businesses that struggle to keep the lights on during normal times. In this blog, we’ll share new research on how small businesses, including those using our free services, have leveraged Cloudflare services to make their businesses more secure and resistant to disruption, along with a real story about how Cloudflare makes a tangible impact for small business customers.
Research has indicated that 43% of cyber attacks target small businesses [Source: Institute for Security and Technology, Blueprint for Ransomware Defense, 2022]. Small businesses face many of the same cybersecurity challenges as larger organizations, but with fewer resources to plan, design, and manage their IT systems and security protections. Most small businesses say they don’t have the personnel to address IT security adequately or appropriately [Source: Ponemon Institute, 2018 State of Cybersecurity in Small & Medium Size Businesses].
Your local florist, fitness studio, café, or pet shop is likely using a wide variety of cloud-based SaaS apps to stay open for customers, including online accounting software, booking systems, point-of-sale credit card readers, inventory management systems, content management systems, and cloud email providers. Each of these systems can be compromised and used to launch an attack. As the global pandemic showed us, small businesses operate with tight margins and very little room for any sort of disruption to daily operations.
While larger enterprises may be able to absorb the temporary loss of revenue from a system outage or a ransomware attack, small business owners can quickly find themselves headed for disaster after just a short period of degraded service quality or system outages. Without a full time security operations center at their disposal or even a dedicated IT staff to focus attention on security issues, small business owners might feel powerless to predict, stop, or mitigate any cyber attacks that could affect their bottom lines and, more worryingly, their livelihoods.
At Cloudflare, our mission is to help build a better Internet. We believe the Internet should be open and free, and that all Internet properties, no matter how small, should be safe, secure, and fast. We believe that every website should have access to the best security and performance available, whether that website belongs to a large multinational corporation, a local non-profit organization, a global human rights advocacy group, an institution of higher learning, or a clothing boutique with a single location in a small town. And most importantly, we believe that everyone on the Internet deserves protection against cyber attacks, even if they use a Free plan and don’t spend any money with Cloudflare.
Small business users
We identified over 94,000 small customers using at least one Cloudflare service, such as small businesses. What do some of these small customers look like? One is a small clothing and apparel company based in Central Europe. Another is a popular coffee shop in Southeast Asia. The largest group of small customers (around 30%) are located in the United States, though they are present across North America, Europe, South America, Australia, and Asia.
| Location | Small Business Accounts* |
|---|---|
| United States | 28,558 |
| United Kingdom | 6,952 |
| Australia | 3,454 |
| Canada | 3,444 |
| Germany | 3,024 |
| Brazil | 2,822 |
| China | 2,777 |
| India | 2,214 |
| France | 1,793 |
| Vietnam | 1,666 |
*Small Customer Accounts Top Ten Locations
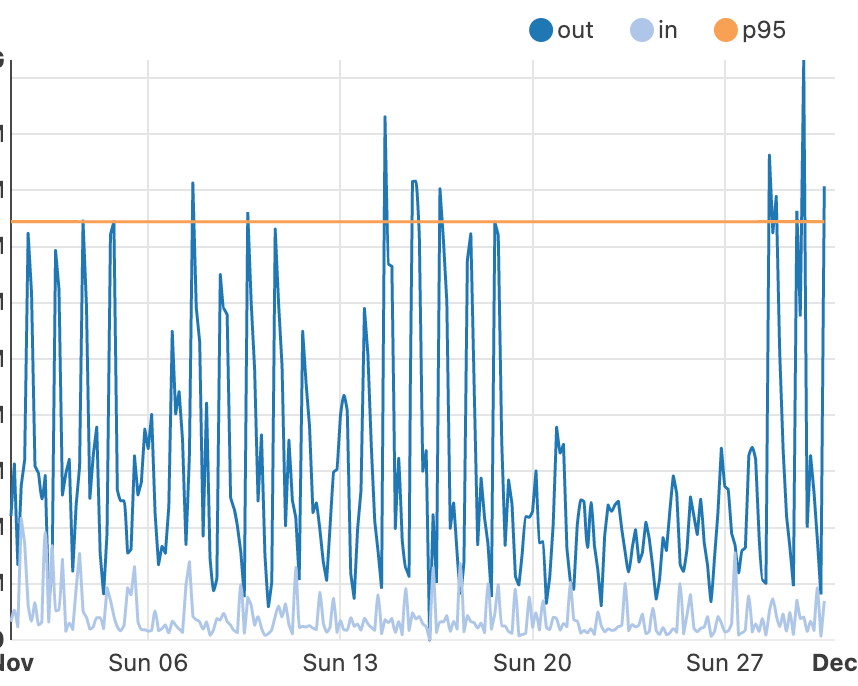
In 2022, these small businesses and organizations were responsible for over seven billion cached requests per day. We identified over 38,000 Layer 3 DDoS attacks that Cloudflare helped mitigate for small customers in 2022. For small businesses, stopping a cyber attack means keeping their doors open – and potentially keeping their businesses afloat.
| Location | Layer 3 attacks on small business customers |
|---|---|
| United States | 18,738 |
| United Kingdom | 7,366 |
| China | 6,576 |
| Germany | 5,423 |
| Canada | 2,517 |
| Australia | 2,374 |
| Brazil | 1,871 |
| Hong Kong | 3,365 |
| Russia | 4,579 |
| Taiwan | 1,666 |
Free plan users
What about the users on Free plans? As of December 2022, we identified 4.2 million Cloudflare accounts using only services available in our Free plan – representing a 40% increase year-over-year from 2021. Together, these Free plan customers were responsible for roughly 70 trillion requests over the Cloudflare network in 2022 – a value of $7 million of content delivery network services that they received at no cost. Many of our Free plan users are also leveraging Cloudflare Access for free, with over two million free Access seats currently in use.
With so many Free plan users, it can be challenging to know what impact these aggregate numbers have on the individuals who run these accounts. That’s why we were pleased to speak with a user on a Free plan who shared their story.
Customer story
A small local hosting company in the southern United States has the responsibility to protect the websites they host, which all belong to small local businesses – the florists, bakeries, and pet shops who are spending their time and resources supporting the local community and who cannot afford to experience downtime from a cyber attack. Some of these websites have e-commerce capabilities, while others contain WordPress sites. Other properties have some level of customized development in need of protection from SQL injections, spoofing, bot scraping attacks, and other malicious activities. While these small business websites are not being specifically targeted by cyber attackers (and instead experience broad, less focused attacks on a wide range of IP addresses) they suffer the same consequences of reduced performance, downtime, and business disruption as larger properties would.
To help mitigate these consequences, the hosting provider uses our free WAF Managed Ruleset and Bot Fight Mode capabilities to protect customer properties. Cloudflare offers another layer of protection and peace of mind for the websites of small businesses to remain operational. By using Cloudflare’s free services, the hosting provider has significantly reduced the large volumes of malicious traffic coming in from overseas IPs. Since the businesses are small and local, any traffic coming from outside the country is unlikely to be a local customer and clearly is not there to transact with the local businesses.
This hosting provider said that their use of Cloudflare had also cut down on their bandwidth egress fees by $100 per month. That may not seem like much from the perspective of a large enterprise – but it adds up quickly for a smaller company. By caching requests through Cloudflare’s network, the provider also reduces server load, so they have more capacity to handle attacks. Most importantly, the hosting provider finds Cloudflare intuitive to deploy and use, and straightforward to customize for the specific needs of the small business websites that need protection.
We closed our conversation with one final thought: “I can’t believe you’re doing this for free!”
No business of any size should have to face cyber attacks alone, whether they are a paying customer or not. Cloudflare is trusted by millions of Internet properties, from the largest global companies to your corner grocery store. Getting started with Cloudflare is simple, fast, and straightforward. You can sign up for a Free plan in minutes to get the tools you need to secure and accelerate your web presence and keep your small business thriving.