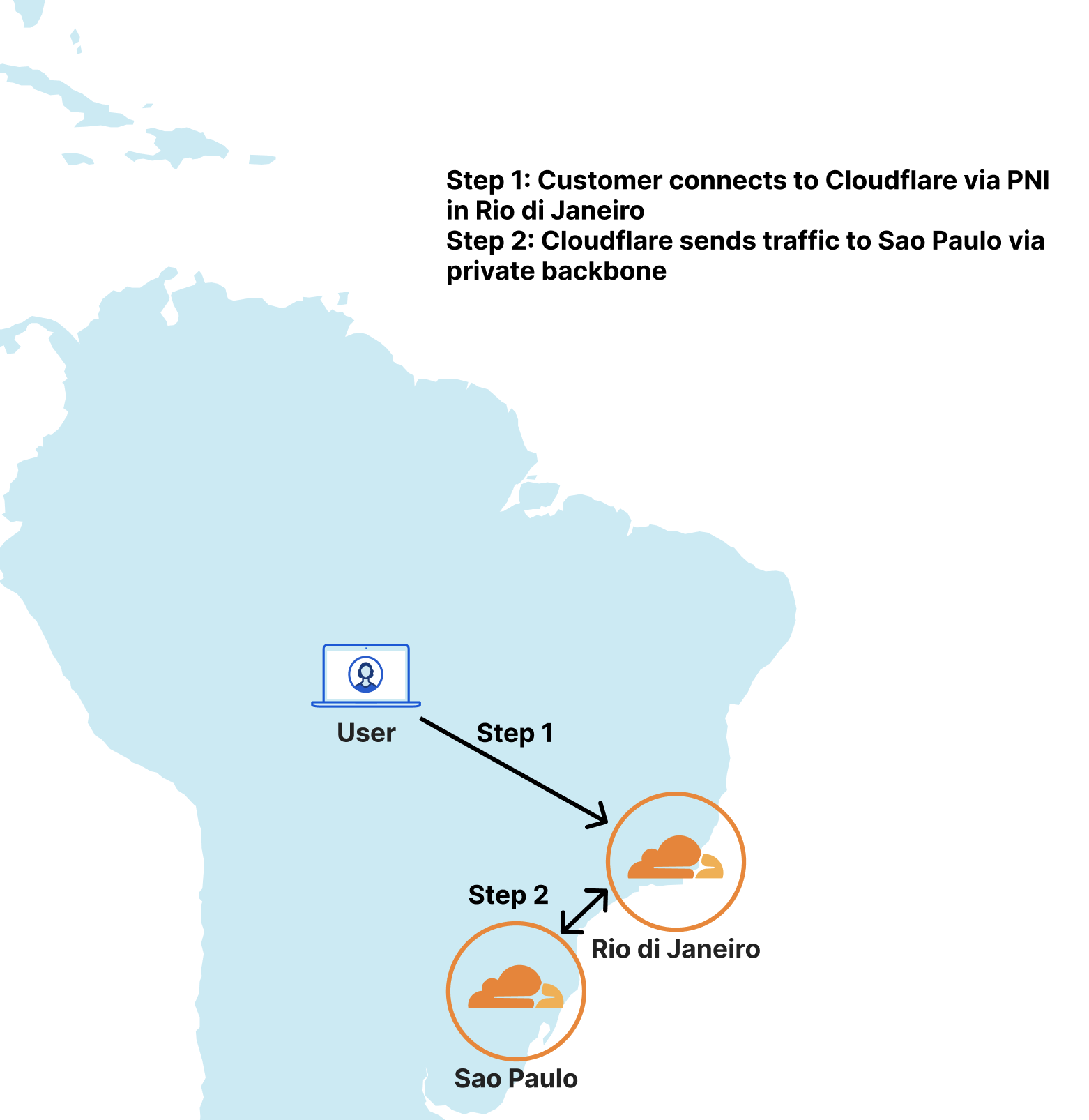
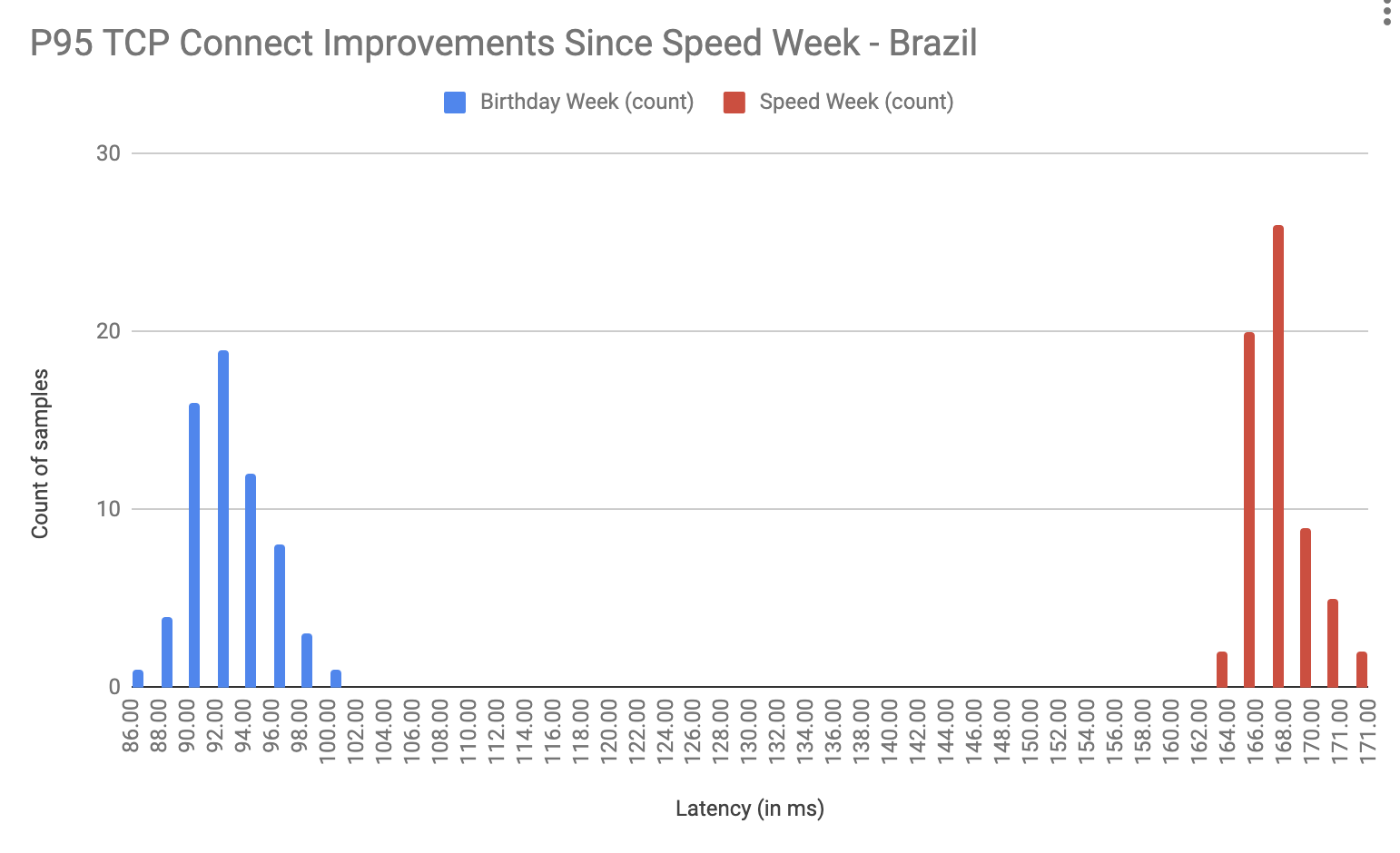
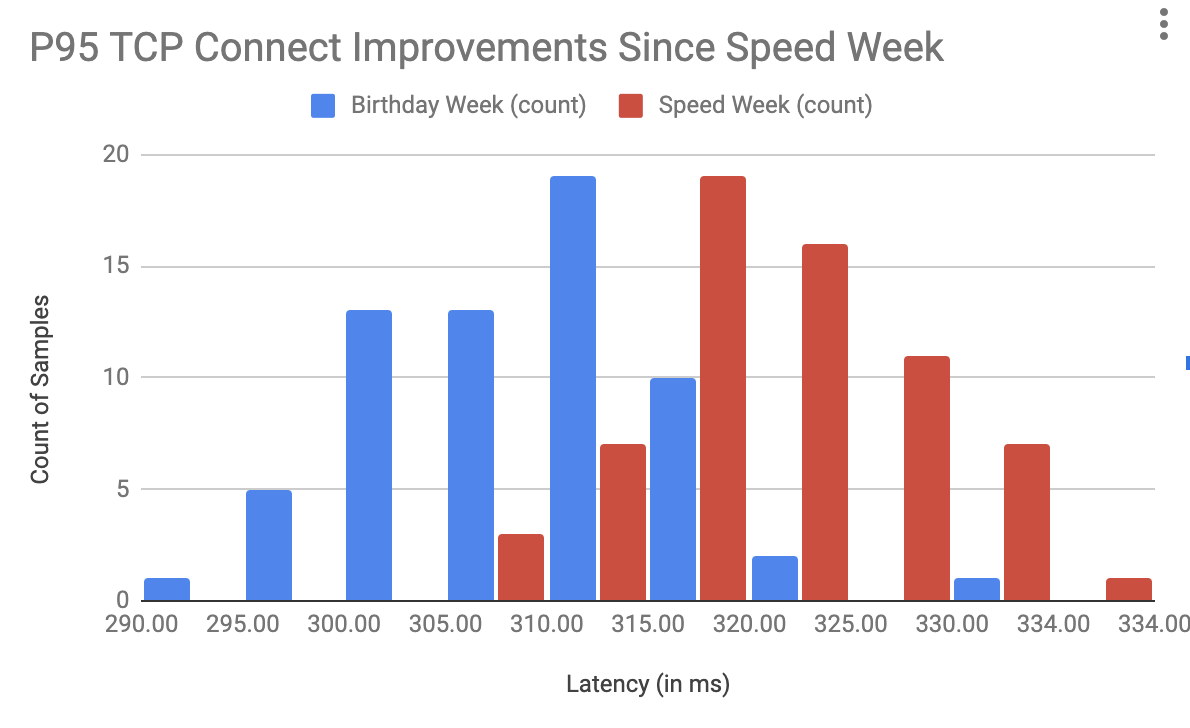
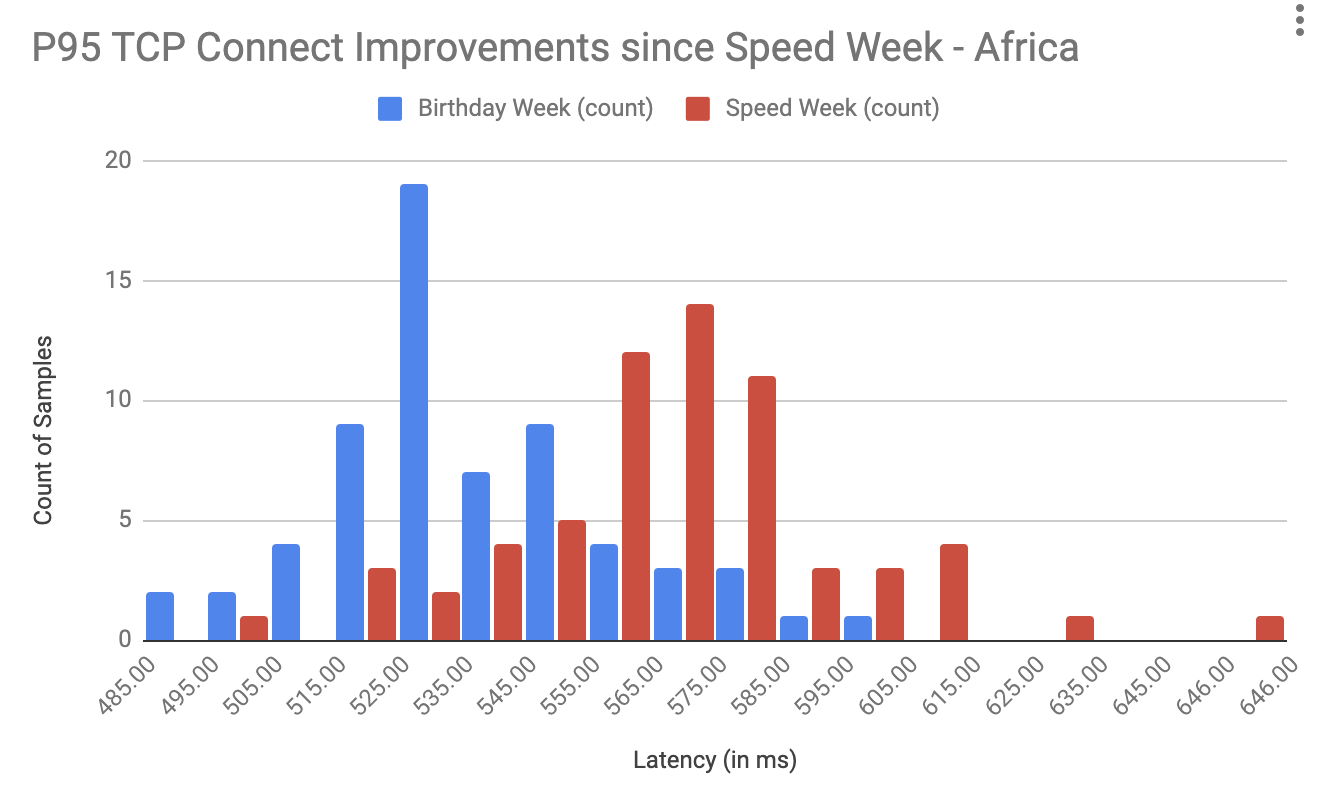
Post Syndicated from Jen Taylor original https://blog.cloudflare.com/the-secret-to-cloudflare-pace-of-innovation/


We are 11! And we also may be a little bleary-eyed and giddy from a week of shipping.

Our Birthday Weeks are one of my favorite Cloudflare traditions — where we release innovations that help to build a better Internet. Just this week we tackled email security, expanded our network into office buildings, and entered into the Web3 world.

But these weeks also precipitate the most common questions I’m asked from my product and engineering peers across the industry: how do we do it? How do we get so much stuff out so quickly? That we are able to innovate — and innovate so quickly — is no happy accident. In fact, this capability has been very deliberately built into the DNA of Cloudflare. I want to touch on three of the reasons unique to us: one relates to our people, one relates to our technology, and one relates to our customers.
Cultivating curiosity
The seeds of innovative ideas start with our team. One of the core things we look for when hiring in every role at Cloudflare — be it engineering and product or sales or account — is curiosity. We seek people who approach a situation with curiosity — who seek to understand the what, the how, and perhaps most importantly, the why of the world around them. Innovation at its core is finding new ways to solve existing problems, and this curiosity is jet fuel for innovation. It pushes us to challenge the status quo. It is through this inquiry that we identify assumptions and unnecessary points of friction.

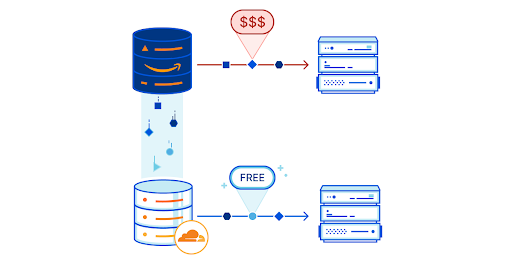
We turn our curiosity towards the world in front of us, the problems that “bug” us about our workflows and the business of the Internet. This is as much about innovating with code as it is about upending business models that don’t make sense to us. It frustrated us that hackers used DDoS attacks to perpetrate financial terrorism by driving up the cost of their victim’s web hosting and delivery bills, so as part of Birthday week in 2017 we made our DDoS protection free and accessible to all. Interestingly, we also have seen a correlating drop in DDoS attacks against many types of sites since then. This year we turned our attention to the egregious egress fees charged by cloud providers and delivered R2, our object storage solution which offers the ability to store large amounts of data — both expanding what developers can build on Cloudflare while slashing the egress bandwidth fees associated with cloud provider storage to zero. We also continue to expand our at-cost registrar service to more TLDs.
There’s an important attribute that partners with curiosity, however. To innovate, we listen. One of the things I screen for when we hire product managers is their ability to listen and synthesize the information they are hearing and then their ability to distill it into actionable problems for us to tackle. We ship early and often with initial concepts. We must listen closely to the feedback from customers — both what they tell us through community forums, support tickets, and meetings and through what they show us in how they adopt and use a feature — and quickly fold this back into the roadmap and the next stage of development. Like some of what you saw this week? Watch our blog for updates and new features as we round out and mature the products.
The best dog food
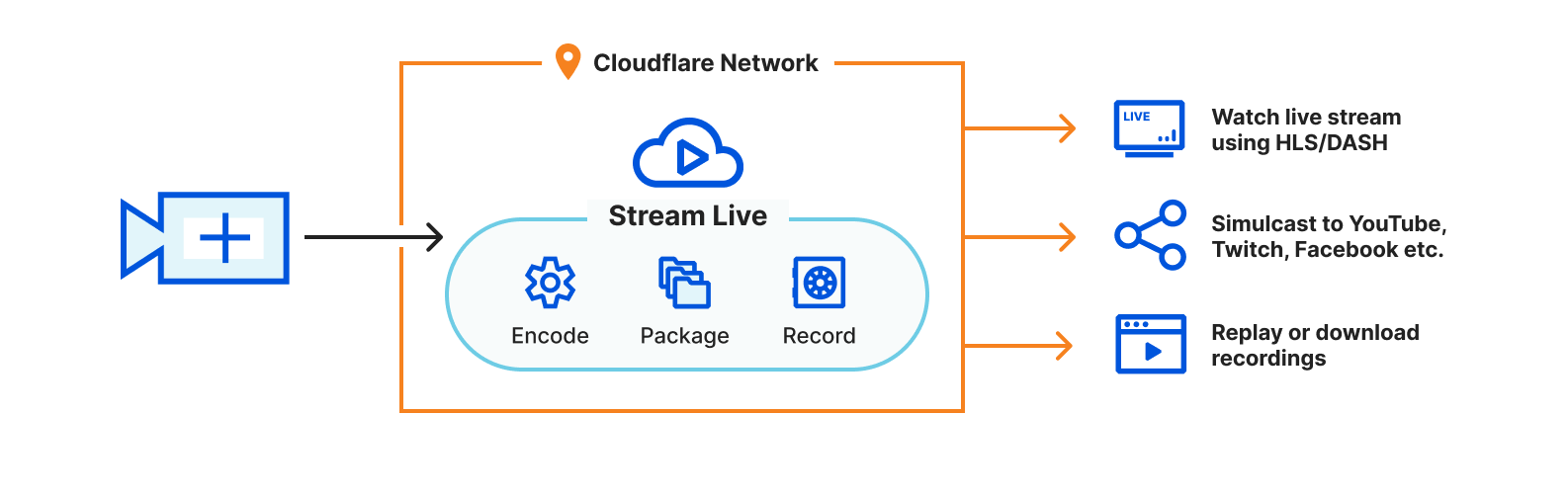
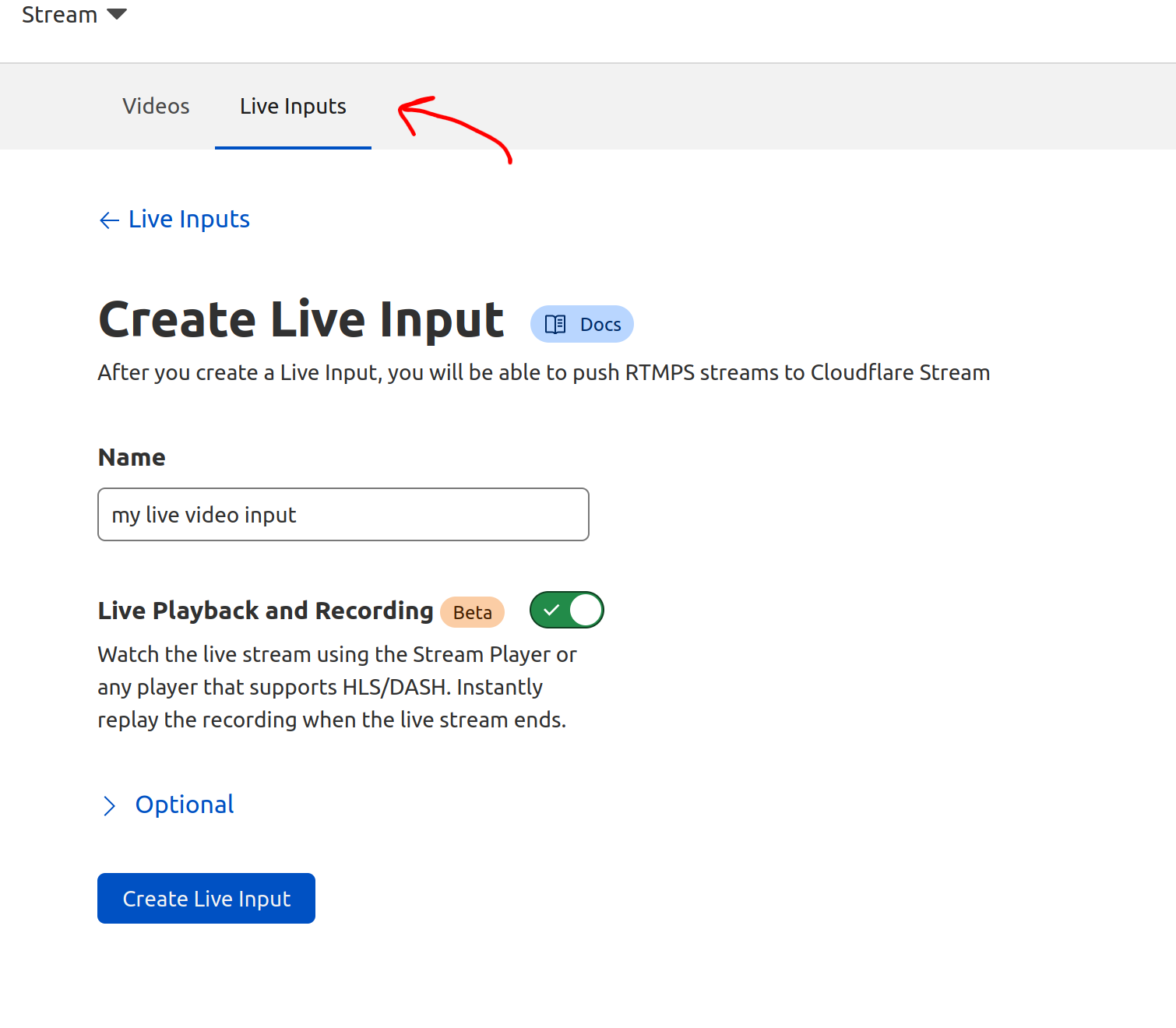
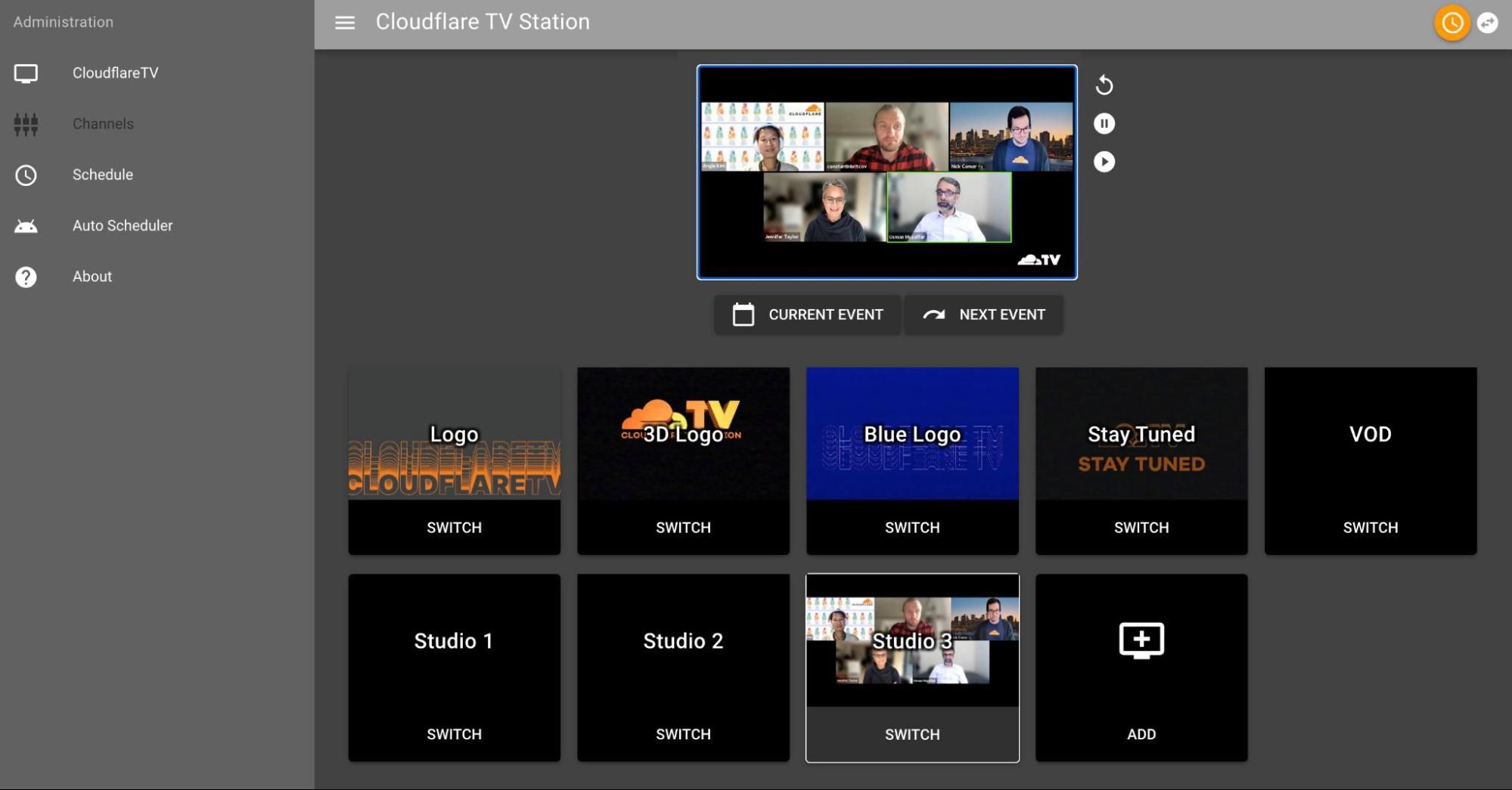
We like to say Cloudflare was built on Cloudflare and for Cloudflare. This means we eat our own dog food with a glass of our own champagne on the side. We wanted a way to connect with our customers and the community, so we built ourselves a real-time streaming service and launched CloudflareTV. Over the past 18 months we ironed out the kinks and this week we made that available to all of you to stand up your own network. We care deeply not only about the capabilities we deliver but how they look and feel. This focus leads to big innovations, but also leads to smaller improvements in how our tools look and feel, like Dark Mode, which was a passion project of a few of our front-end developers and one of the most requested features of all time by our own team.

So that’s an example of what happens. But how were we able to do this?
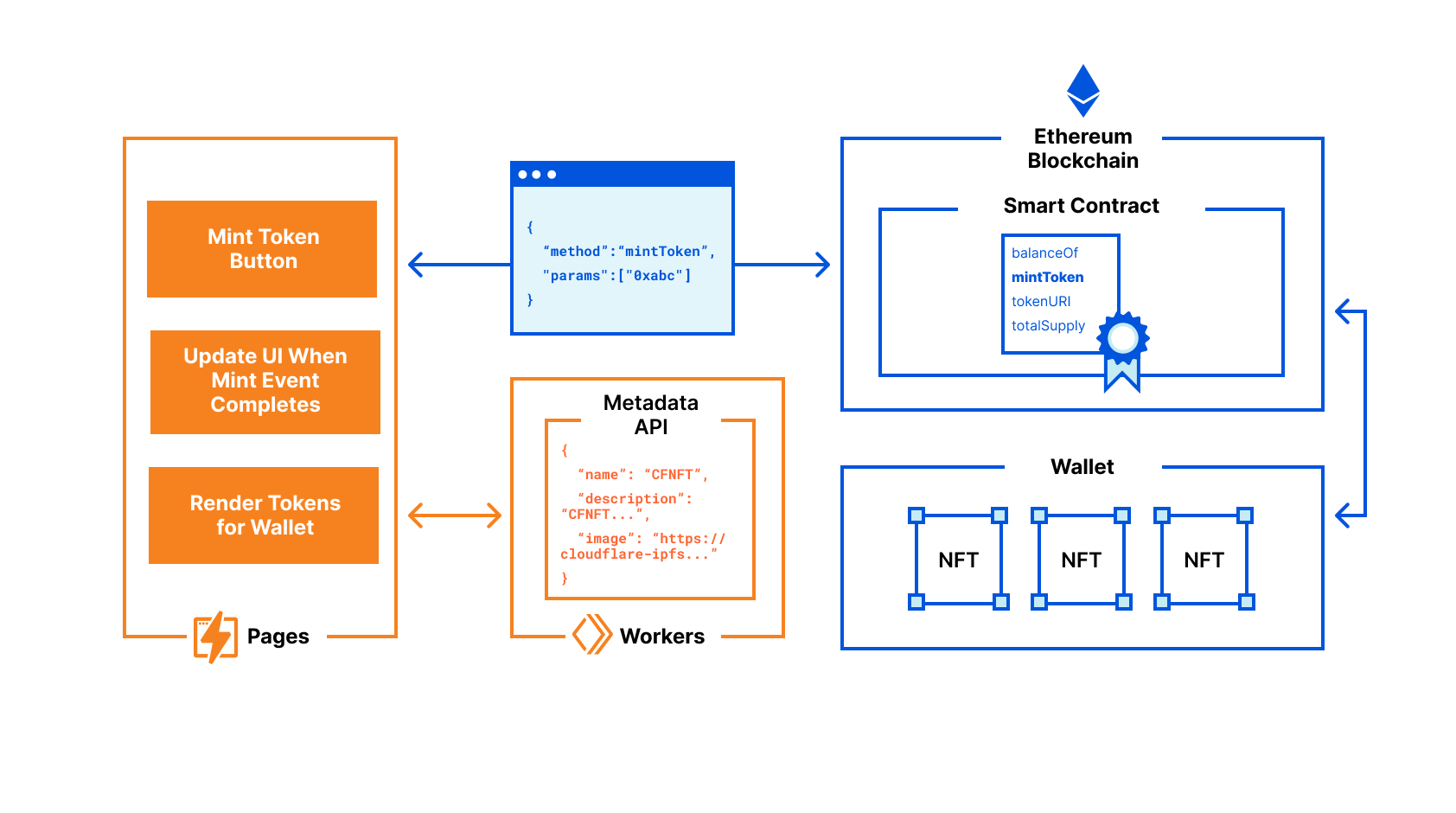
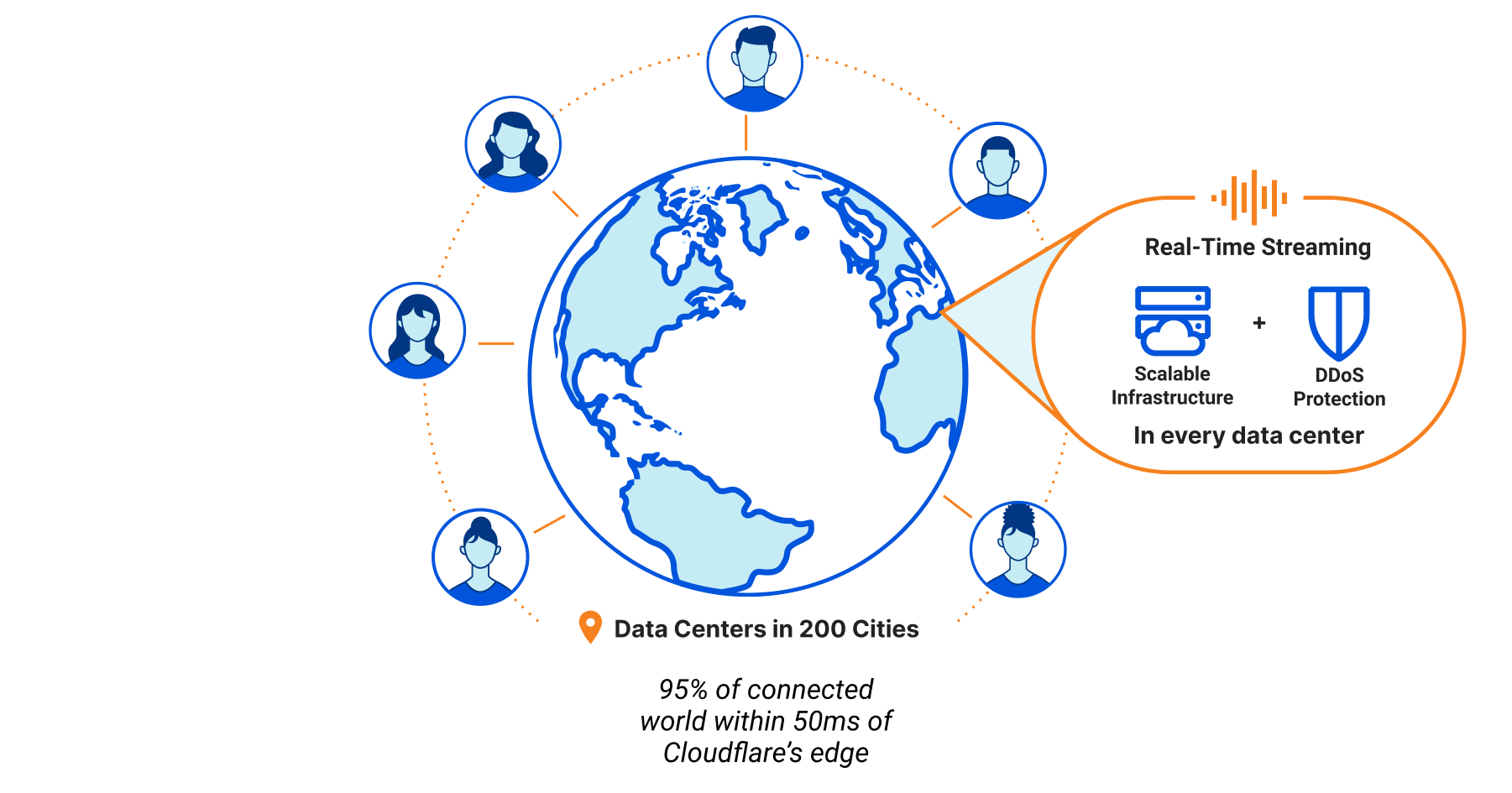
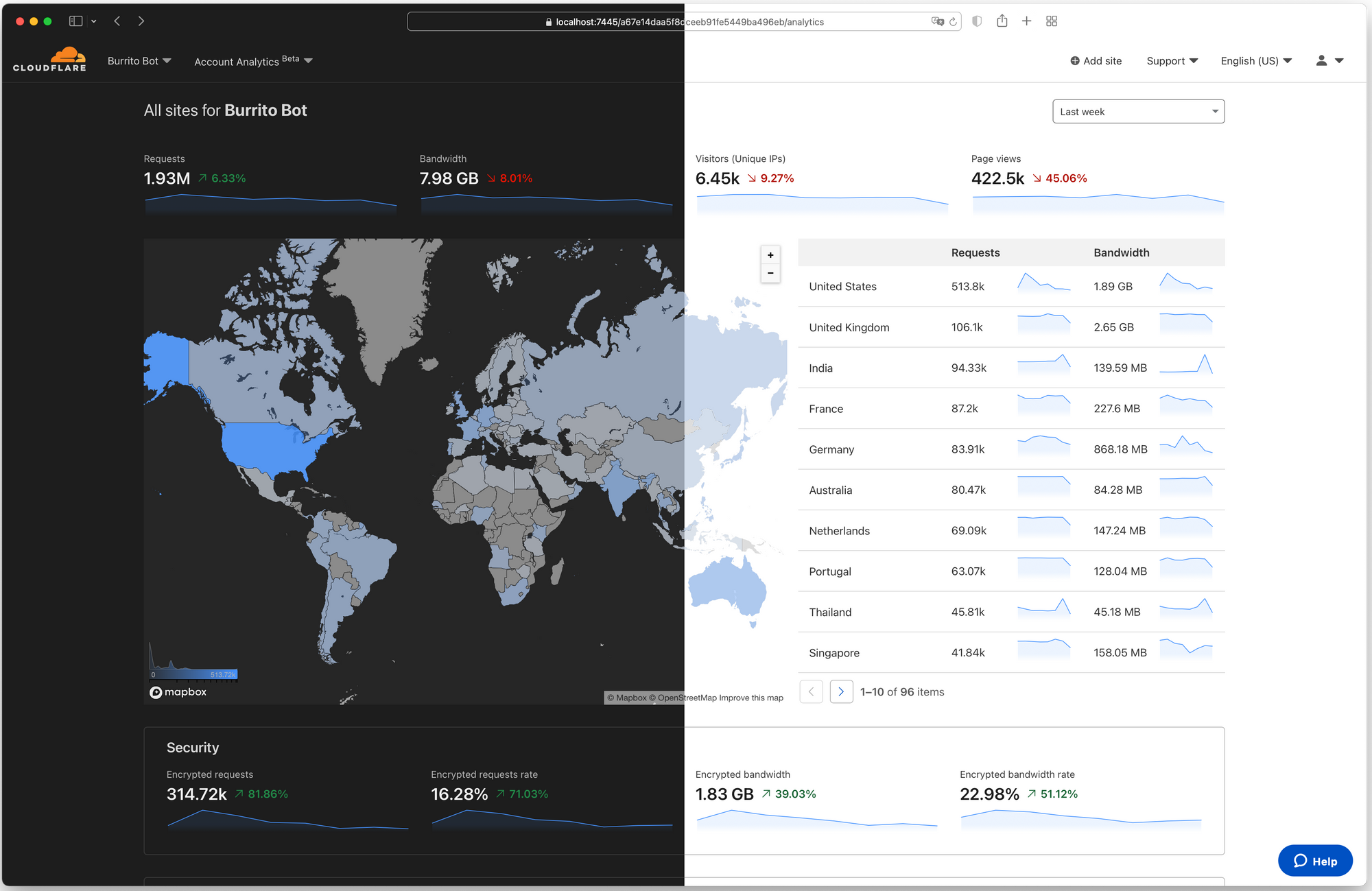
It’s driven by our Workers platform. This isn’t just something that’s making our customers’ lives easier. No containers to manage; no scaling to handle. We use it, too. It’s a layer of abstraction on top of our network that enables a massive amount of development velocity. Our unified architecture provides a single, scalable platform on which to innovate and allows us to roll things out in a matter of seconds across our entire network (and roll them back even more quickly if things don’t go to plan, which also sometimes happens). We’re constantly striving to make this network faster, safer, and more reliable. We’re constantly evolving our network to make it better. A couple of weeks ago we announced we’d expanded to 250 cities and are now within 50 milliseconds of 95% of the Internet-connected population. This week we expanded the footprint of our network into office buildings, getting even closer to end users.

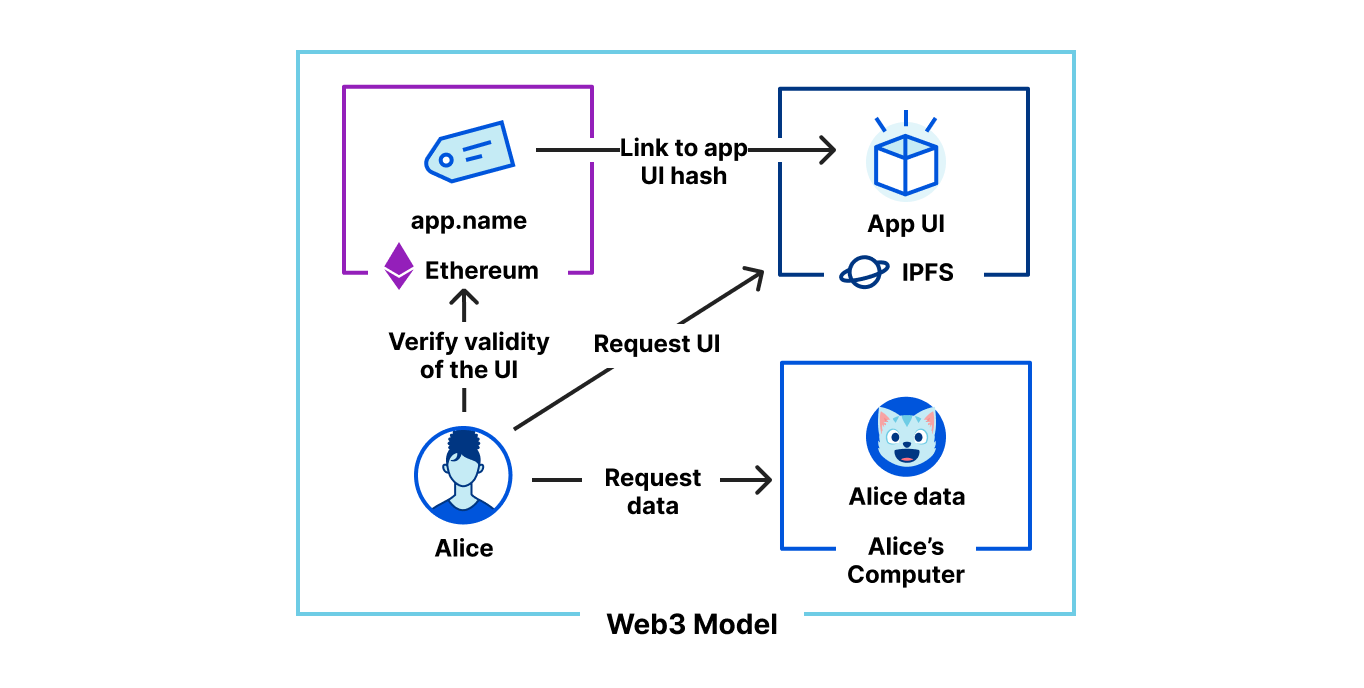
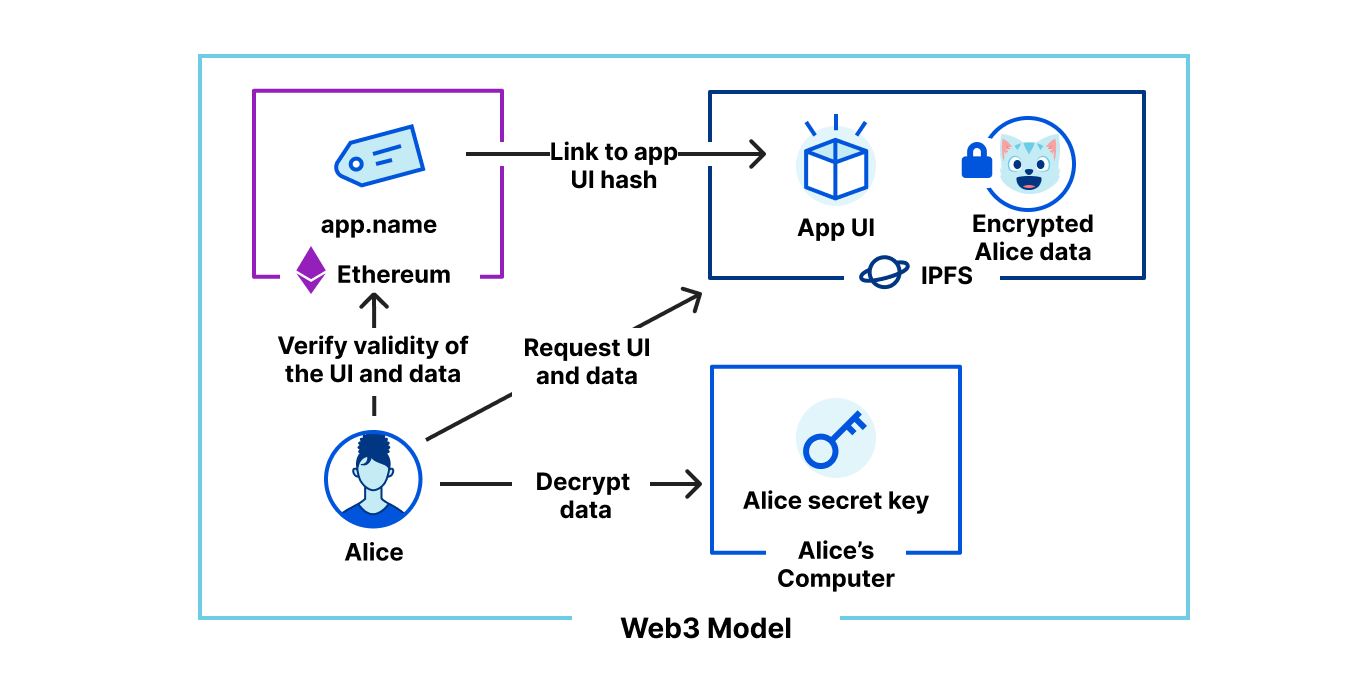
This abstraction enables us to have smaller teams to build any new product or service. While others in the industry talk about building “pizza box” teams — teams small enough that they can all share a pizza together — many of our innovation efforts start with teams even smaller. At Cloudflare, it is not unusual for an initial product idea to start with a team small enough to split a pack of Twinkies and for the initial proof of concept to go from whiteboard to rolled out in days. We intentionally staff and structure our teams and our backlogs so that we have flexibility to pivot and innovate. Our Emerging Technology and Incubation team is a small group of product managers and engineers solely dedicated to exploring new products for new markets. Our Research team is dedicated to thinking deeply and partnering with organizations across the globe to define new standards and new ways to tackle some of the hardest challenges. These efforts drove our Web3 announcements and I could not be more excited to see where you all take them.

We ship software for businesses like a consumer software company. Traditional B2B software development typically follows longer development cycles and focuses on delivering more fully featured and deeply integrated offerings out of the gate. This cautious approach yields fewer more fully featured offerings shipped less frequently. Consumer software, on the other hand, is typically built in a highly iterative process — where teams develop initial concepts quickly and roll them out frequently in small pieces to subsets of users to test and understand how people use them and then use these observations to guide development. Many of the seeds that shaped the email security offerings this week started as small experiments by the DNS team, Emerging Technology, and our Customer Support team.
There’s one more aspect to all of this — because we’ve innovated in the way we’ve built our network — making it highly scalable and cost-effective — we’re able to pass these savings on to our customers. In a lot of instances, these savings amount to a pretty good price for our products and services: nothing at all.
Born to be free
Typically, in B2B enterprise software companies, the big customers and the multi-million dollar contracts get 99.99% of the focus. Here’s what I would say: our free customers are the secret sauce to our innovation. Today, millions of websites and applications across the globe use our service for free. Free is invaluable to innovation.
One of the most difficult parts of building B2B software is getting the first 100 users. These early users are critical to assess the quality, scale, and capabilities of a product. But B2B folks are notoriously risk averse: their application or users are their lifeblood, and they aren’t necessarily willing to make them guinea pigs. They would rather sit on the sidelines and wait for someone else to go first. So when you are building B2B software, you are stuck in a conundrum — how do you get the users you need to prove out the capabilities? We’re fortunate to have millions of free sites and applications on our network. Like a consumer app developer, we typically roll out new capabilities to pods of these users first. These users give us the volume and scale to get confident in what we’ve delivered. The more confident we get, the more broadly we roll out, such that by the time it hits broad rollout, our customers can feel confident in the quality and stability.
The large and diverse free customer base also helps fuel innovation. Through servicing a large and diverse base — from a personal blog in Bolivia to a small business in Chennai to a start-up in Munich — we observe unique traffic and threat patterns. We take these learning and fold the insights back into our product to dynamically route traffic across the fastest route and stop emerging threats before they scale.
The other thing I love about Birthday Week? It is the place critical innovations start that will ultimately transform the way we work. Universal SSL in 2014 made SSL free and available to all customers, doubling the number of active sites that use encryption within 24 hours of launch. Seedling ideas, such as Workers, which we launched in 2017, have become the foundation of a whole new generation of applications.
I mentioned earlier that two of the most common questions I’m asked about Cloudflare relate to how we do it. Well, there’s often a third, and that too comes up quite a lot during Birthday Week. And that question is: “are you hiring?!” The answer is a resounding yes! We have opportunities across a variety of roles in Cloudflare: Legal, Product, Engineering, Sales, IT. Good ideas come from everywhere. I’d love nothing more than to engage your curiosity to help us build a better Internet.