Post Syndicated from Dmitry Lambert original https://blog.zabbix.com/how-to-upgrade-to-zabbix-5-2/12872/
Zabbix recently released the new 5.2 version with awesome new features overviewed in the video, such as hashicorp vault, IoT monitoring, improved performance, granular permission system, and much more. The upgrade to the latest Zabbix 5.2 is fast and easy.
Contents
I. Upgrade Zabbix on CentOS 8 (0:45)
II. New in Zabbix 5.2 (2:26)
III. Upgrade procedure (3:39)
IV. Conclusion (9:51)
Upgrade Zabbix on CentOS 8
To upgrade the existing Zabbix instance installed on CentOS 7, it is recommended to migrate to CentOS 8 first as currently there are no official packages available of CentOS 7 for Zabbix 5.2. Since there is no clean way to upgrade CentOS installation, it is recommended to create a new server on CentOS 8 and then migrate your database and spin up Zabbix Server there. CentOS 7 is old and has limited packages in the repositories, which are not updated anymore. Even if you use all the latest software and packages from the official repo, it will not be enough to successfully run all of the functionality of Zabbix 5.2. For instance, TLS 1.3 will not be available, as well as database encryption.
If you run the default frontend and default server from the packages, and if you don’t have any customization patches, any custom functionality, or edited PHP source code that you want to save, then the upgrade is straightforward.
New in Zabbix 5.2
To find out what we can expect after the upgrade, on the Zabbix documentation page for the 5.2 release, go to Installation > Upgrade notes for 5.2.0.
- The minimum required PHP version has been upped from 7.2.0 to 7.2.5, which might be an issue on CentOS 7.
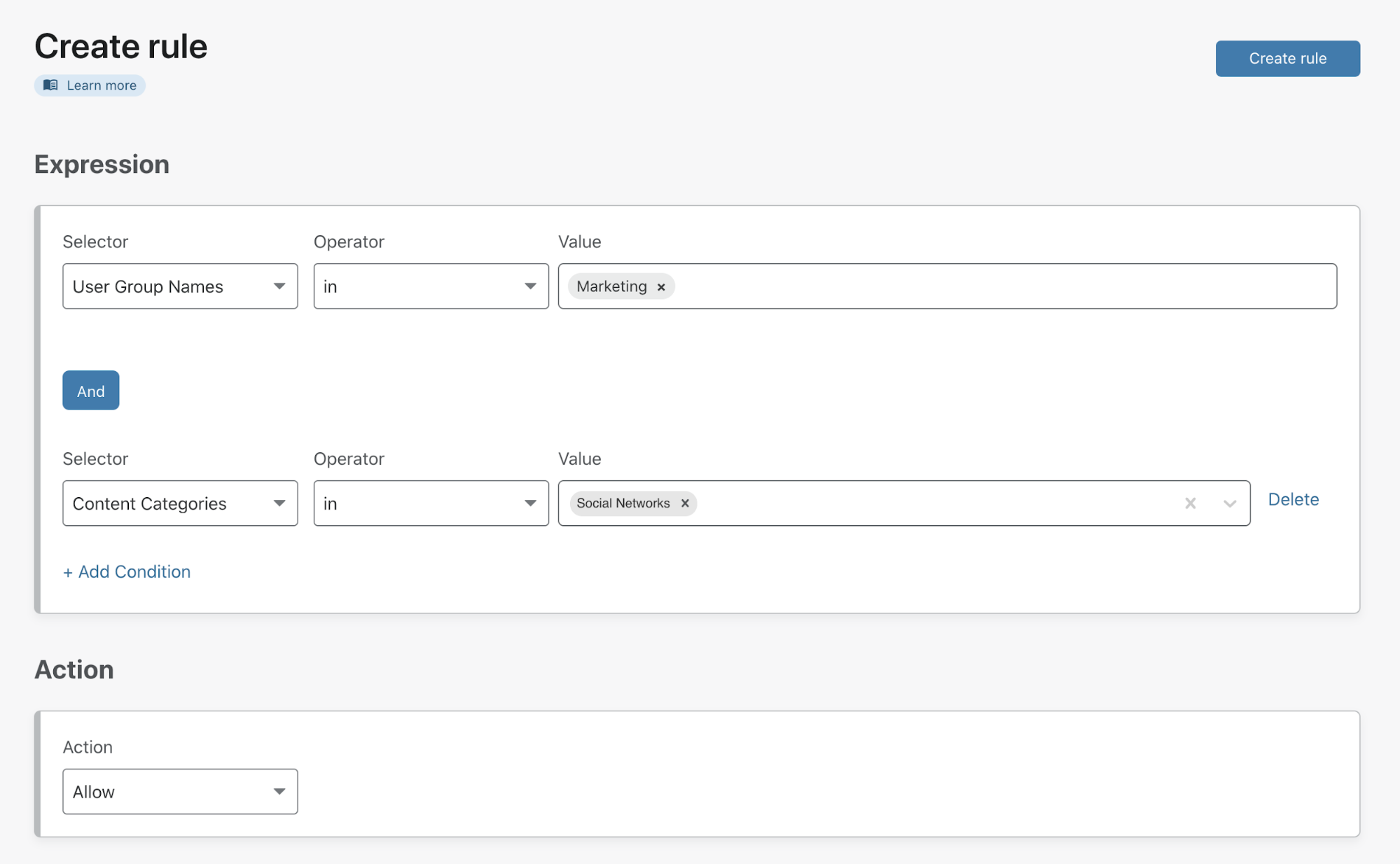
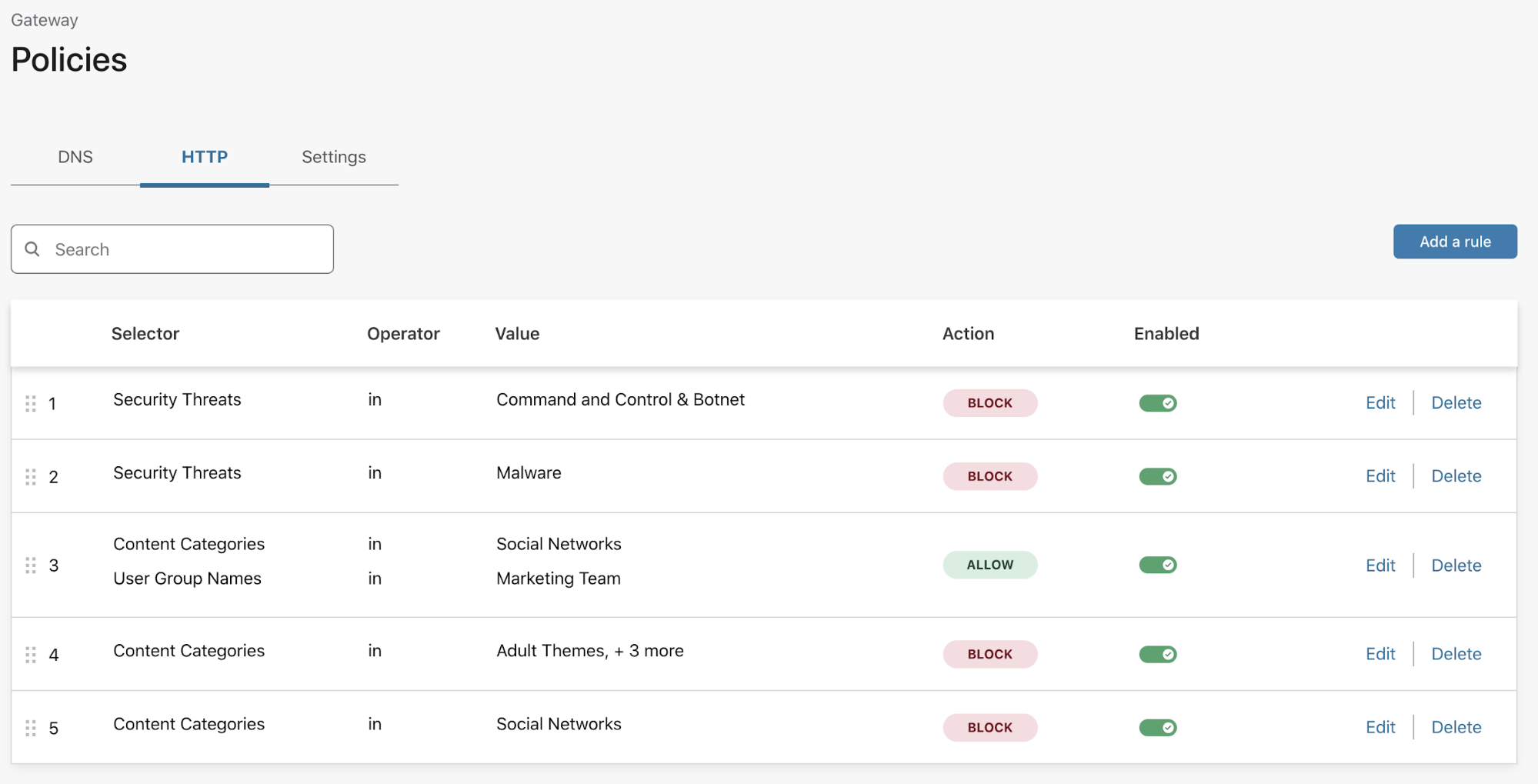
- User roles. Now you can assign different roles to your existing users through your existing permission system will not be broken.
- Time zone definition. If you are running your frontend with multiple virtual hosts, you can delete all of those and configure everything natively in the frontend.
- Refreshing unsupported items setting has been removed from Administration > General > Other, with the item update interval now used for each unsupported item.
- Template screens converted to dashboards with the screens to be set up in the dashboards now as widgets of template dashboards.
- The session of the Zabbix frontend is now stored in a cookie.
If you upgrade, you will still have to log in to the frontend providing the username and password.
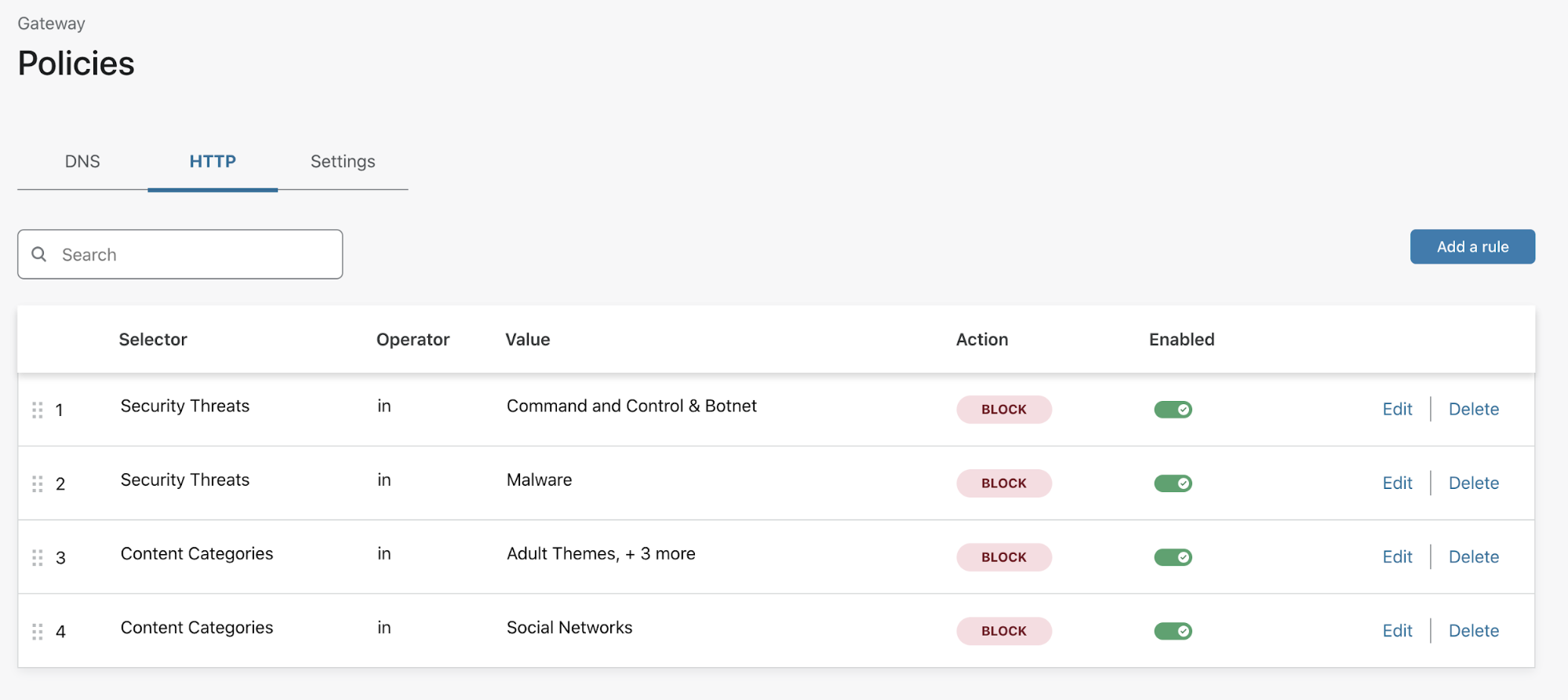
Upgrade procedure
In the Zabbix documentation page, open Upgrade procedure > Upgrade from packages > 1 Red Hat Enterprise Linux/CentOS, where the upgrade notes are available, which are helpful if you’re upgrading from the old version.
1. Stop Zabbix server.
# systemctl stop zabbix-server
2. Back up the existing Zabbix database. It is very important as there is no rollback functionality. If you can’t test the upgrade in the dev environment, it is recommended to backup the database.
3. Back up configuration files, PHP files, and Zabbix binaries.
Configuration files:
# mkdir /opt/zabbix-backup/ # cp /etc/zabbix/zabbix_server.conf /opt/zabbix-backup/ # cp /etc/httpd/conf.d/zabbix.conf /opt/zabbix-backup/
PHP files and Zabbix binaries:
# cp -R /usr/share/zabbix/ /opt/zabbix-backup/ # cp -R /usr/share/doc/zabbix-* /opt/zabbix-backup/
This step is optional if you have an official frontend, official server, etc., without any patches or customizations. In this case, you can download the required official files for Zabbix 5.2 from the sources or install them from the repository as a package in case is something goes wrong.
4. Update repository configuration package. To proceed with the upgrade, you need to update your current repository package, especially if you don’t have packages for Zabbix 5.2 yet.
# rpm -Uvh https://repo.zabbix.com/zabbix/5.2/rhel/8/x86_64/zabbix-release-5.2-1.el8.noarch.rpm
Then you can run:
# yum clean all
and
# yum makecache
to make sure that the repository will be picked up. Then you’ll see the new packages of Zabbix 5.2.
Metadata cache created
These commands are not mandatory, but otherwise, you could upgrade your repository and then find out that the Zabbix 5.2.0 upgrade package is ‘not found’.
5. Upgrade Zabbix components. If you’re new to Zabbix and this is your first upgrade, you don’t need to do anything manually, run any database upgrade scripts, manually change or adjust the schema of the database, or do whatever else. All you have to do is upgrade your packages:
# yum upgrade zabbix-server-mysql zabbix-web-mysql zabbix-agent
NOTE. You can substitute the elements of this command depending on the software actually installed.
Type ‘-y‘ to automatically confirm everything. After the update is complete, you can check the installed version by running:
# zabbix_server -V
To upgrade the web frontend with Apache on RHEL 8 correctly, also run:
# yum install zabbix-apache-conf
NOTE. Type ‘y’ when asked for confirmation.
Now all you have to do to start the upgrade automatically is run:
# systemctl start zabbix-server
Then check the log file of the Zabbix server:
# tail -f /var/log/zabbix/zabbix_server.log
or
# less /var/log/zabbix/zabbix_server.log
After starting the new 5.2 binary, you will see in the log file that the current database version is 5.0, while the required mandatory version is 5.2. That’s why the Zabbix server package will start the automatic database upgrade.
Now we need to run:
# systemctl restart httpd php-fpm
as those were still running while we were upgrading the packages.
Then you need to log in as cookies are stored differently.
In the frontend, you’ll see the updated version and new features, such as new roles we can add in Administration > User roles.
User roles
6. Review component configuration parameters. Make sure to see the upgrade notes for details on mandatory changes.
7. Start Zabbix processes.
# systemctl start zabbix-server # systemctl start zabbix-proxy # systemctl start zabbix-agent # systemctl start zabbix-agent2
Conclusion
This was everything required for the installation to run successfully. The process is straightforward if you don’t have any complicated customizations of your frontend, Zabbix server binaries, etc. Though in production, it is recommended to test installation out in the dev environment and make backups.
I definitely recommend you to try out the newest Zabbix 5.2.
Thanks for your attention! Like, comment, subscribe!





















 Asser Moustafa is an Analytics Specialist Solutions Architect at AWS based out of Dallas, Texas. He advises customers in the Americas on their Amazon Redshift and data lake architectures and migrations, starting from the POC stage to actual production deployment and maintenance
Asser Moustafa is an Analytics Specialist Solutions Architect at AWS based out of Dallas, Texas. He advises customers in the Americas on their Amazon Redshift and data lake architectures and migrations, starting from the POC stage to actual production deployment and maintenance
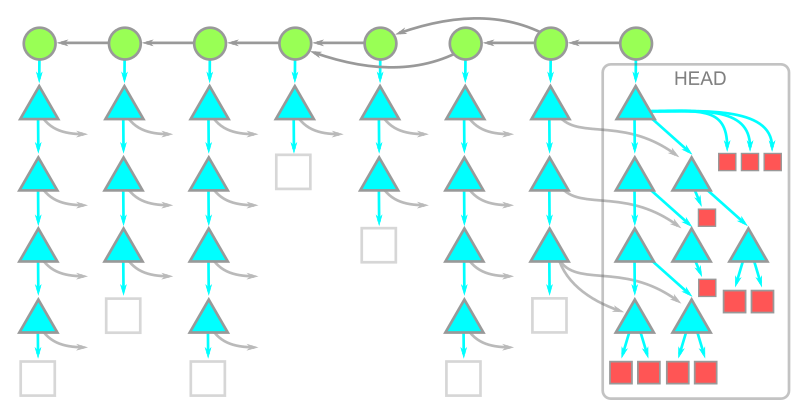
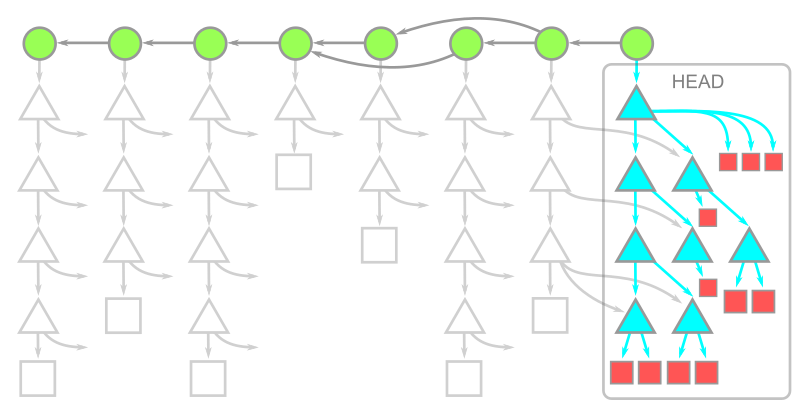
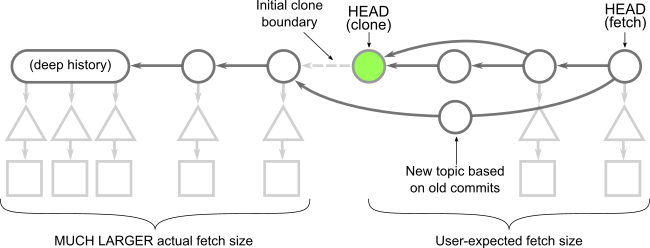
 Warning: While writing this article, we were putting treeless clones to the test beyond the typical limits. We noticed that repositories that contain submodules behave very poorly with treeless clones. Specifically, if you run
Warning: While writing this article, we were putting treeless clones to the test beyond the typical limits. We noticed that repositories that contain submodules behave very poorly with treeless clones. Specifically, if you run 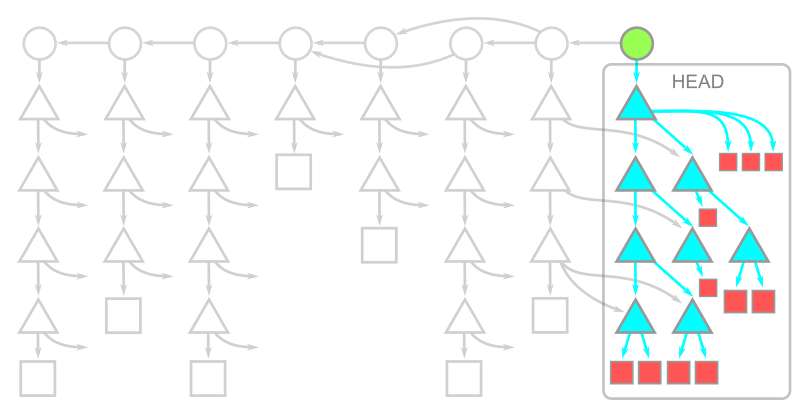






 Damian Grech is a Data Engineering Senior Manager at FanDuel. Damian has over 15 years of experience in software delivery and has worked with organizations ranging from large enterprises to start-ups at their infant stages. In his spare time, you can find him either experimenting in the kitchen or trailing the Scottish Highlands.
Damian Grech is a Data Engineering Senior Manager at FanDuel. Damian has over 15 years of experience in software delivery and has worked with organizations ranging from large enterprises to start-ups at their infant stages. In his spare time, you can find him either experimenting in the kitchen or trailing the Scottish Highlands. Shiv Narayanan is Global Business Development Manager for Data Lakes and Analytics solutions at AWS. He works with AWS customers across the globe to strategize, build, develop and deploy modern data platforms. Shiv loves music, travel, food and trying out new tech.
Shiv Narayanan is Global Business Development Manager for Data Lakes and Analytics solutions at AWS. He works with AWS customers across the globe to strategize, build, develop and deploy modern data platforms. Shiv loves music, travel, food and trying out new tech. Sidhanth Muralidhar is a Senior Technical Account Manager at Amazon Web Services. He works with large enterprise customers who run their workloads on AWS. He is passionate about working with customers and helping them in their cloud journey. In his spare time, he loves to play and watch football.
Sidhanth Muralidhar is a Senior Technical Account Manager at Amazon Web Services. He works with large enterprise customers who run their workloads on AWS. He is passionate about working with customers and helping them in their cloud journey. In his spare time, he loves to play and watch football.